Giacomo Lanzi
Giacomo Lanzi
Updating php: why and how
PHP is one of the most popular scripting languages on the web today. According to W3Techs, PHP is used by over 82% of all websites that use a server-side programming language. This means that 8 out of 10 sites use PHP in one form or another. Being a scripting language, it is essential to update PHP to the latest version available, unless you have special needs.
Today we try to understand the importance of updating to the latest PHP versions, not only for security reasons, but also to improve performance and support. The precise procedure will also be shown via a simple how-to.
When to update PHP?
As with any software, PHP has a lifecycle that it must adhere to in order to continue making improvements and moving forward in development. Each major PHP release is generally fully supported for two years. During this time, bugs and security issues are regularly fixed and fixed. a third year of support is guaranteed, only for what concerns language security and not performance.
PHP versions supported
As of today (summer 2020), anyone running a version of PHP 7.1 or lower no longer benefits from security support and is exposed to vulnerabilities that will not be fixed. According to the official WordPress Stats page, at the time of writing this article, over 41% of WordPress users are still using PHP 7.1 or lower. This is not only a security issue, but it is also a hindrance as there are still many sites that do not take advantage of the further performance improvements introduced with PHP 7.2 and later.
Unfortunately, not everyone is aware of the danger and since updating PHP is an operation that must be done on the server and not from the site itself, a good portion of users do not even know how to proceed.
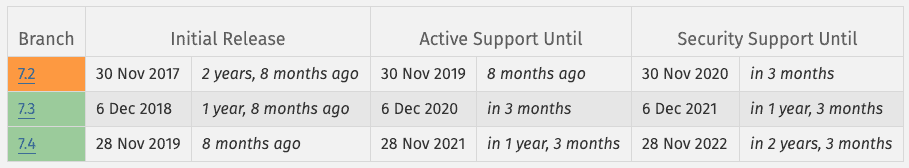 As can be seen from this image, the currently supported versions of PHP are 3: 7.2, whose security support will end on November 30, 2020; 7.3, supported until December 2021 and 7.4 supported until November 2022. Warning: in the last 12 months of the version’s life, the only guaranteed support is the security one.
As can be seen from this image, the currently supported versions of PHP are 3: 7.2, whose security support will end on November 30, 2020; 7.3, supported until December 2021 and 7.4 supported until November 2022. Warning: in the last 12 months of the version’s life, the only guaranteed support is the security one.
Slow updates
There are many factors that could affect a slow adoption of recent versions of the language, here are some of them:
1. The owners of the sites, not being technicians, do not know the language and do not know they have to update PHP in order to have a safe and up-to-date site.
2. Those who use custom themes or plugins on their site want to be sure that the new PHP versions do not have backwards compatibility problems. These developers are waiting for the new guidelines to be released for the most recent versions, and only after checking their plugins and themes do they fully adopt the new version.
3. Some hosts are afraid to update the language on the server as it could lead to a wave of support tickets. Luckily, providers increasingly make the choice of version available to the end user, as we will see shortly.
Honestly, I don’t understand all this fear of updating PHP and keeping your systems running well and safe. I think the wait is quite useless and risky.
How to update PHP on SOD hosting panel
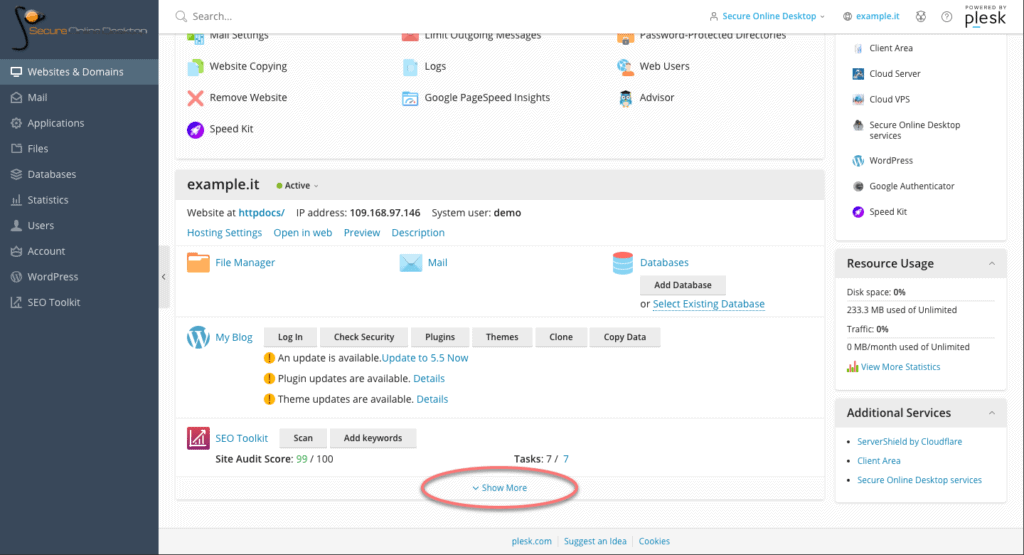
First, log into your control panel and from the main dashboard, scroll down to the section of the site concerned. At the bottom, click on the “Show More” button to view hosting options.
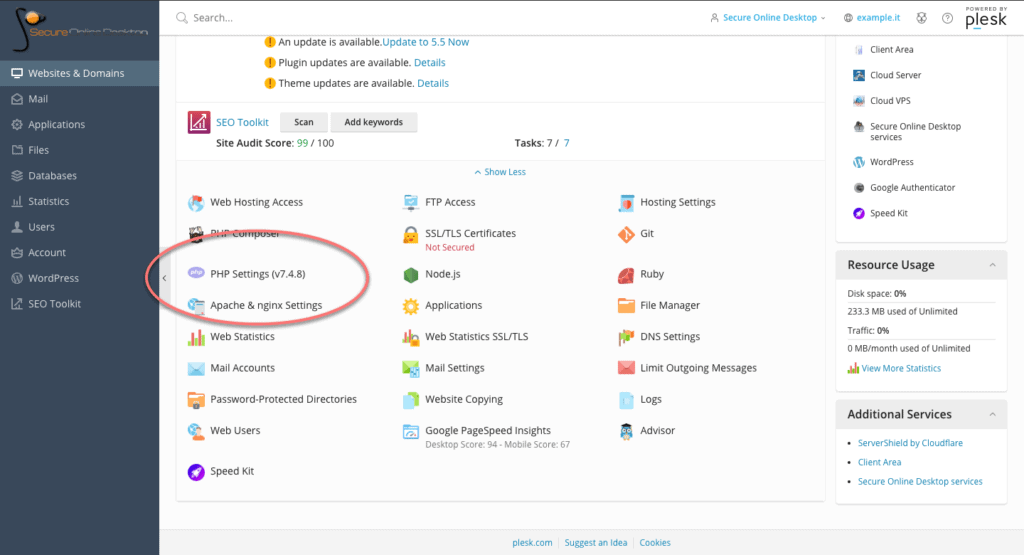
Among the options, look for the one called “PHP Settings”. Note that the version currently in use by the server is already shown next to the name. Click on the option to land on the PHP settings page.
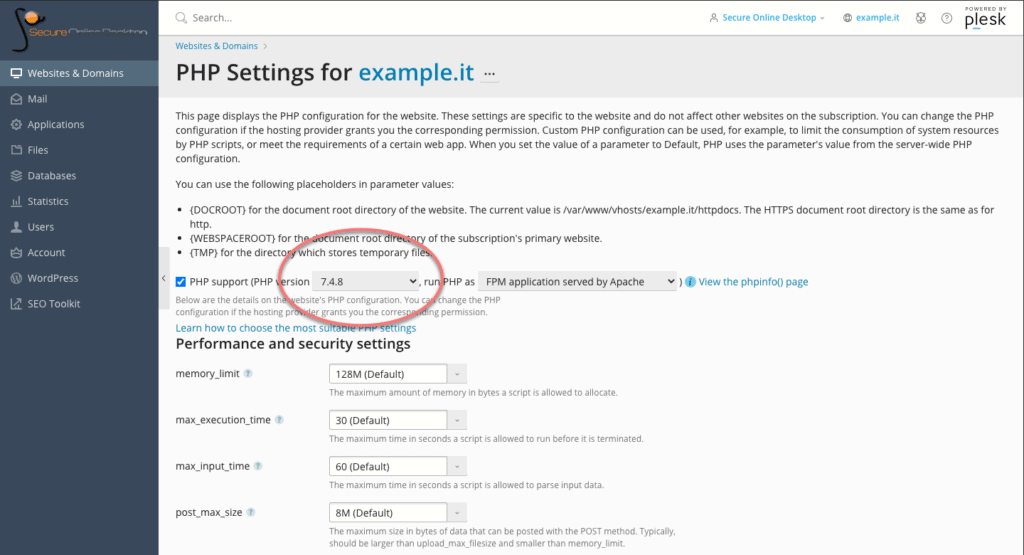
Within the PHP section, it is possible, through a drop-down menu, to change the version in use. Versions that are no longer updated are marked as “outdated”, but still selectable.
On the page, in addition to the version active on the server, it is possible to modify many other PHP options relating to performance and security. For example the limit of the dedicated memory, the maximum execution time of the scripts, the location of the scripting folders and so on.
These are all features that the average user does not need on a daily basis, but the fact that such in-depth control of PHP options is available is a plus for the flexibility of the control panel and service.
Make sure your host is using the latest versions of PHP
As we have seen, updating PHP to the supported version is a simple operation to be performed through the appropriate panel of the hosting plan.
A few years ago, a great article titled “Whipping Your Host Into Shape” by Joost de Valk went into detail about how the real problem is that providers don’t adopt recent versions faster and, even if they do, they don’t encourage users to update themselves. Years have passed since that article and I hope that the trend will improve, and that more and more people think about the security of their portals also through the updating of the infrastructure that hosts them.
Through the control panel of SOD hosting plans, keeping the service updated and secure is simple, and updating PHP is just an example of the potential of the panel itself. Check for yourself by accessing a demo of the service.
[btnsx id=”2931″]
Useful links:
Manage WordPress from the hosting panel
Customers
Twitter FEED
Recent activity
-
SecureOnlineDesktop
Estimated reading time: 6 minutes L'impatto crescente delle minacce informatiche, su sistemi operativi privati op… https://t.co/FimxTS4o9G
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The growing impact of cyber threats, on private or corporate operating systems… https://t.co/y6G6RYA9n1
-
SecureOnlineDesktop
Tempo di lettura stimato: 6 minuti Today we are talking about the CTI update of our services. Data security is… https://t.co/YAZkn7iFqa
-
SecureOnlineDesktop
Estimated reading time: 6 minutes Il tema della sicurezza delle informazioni è di grande attualità in questo peri… https://t.co/tfve5Kzr09
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The issue of information security is very topical in this historical period ch… https://t.co/TP8gvdRcrF
Newsletter
{subscription_form_1}© 2023 Secure Online Desktop s.r.l. All Rights Reserved. Registered Office: via dell'Annunciata 27 – 20121 Milan (MI), Operational Office: via statuto 3 - 42121 Reggio Emilia (RE) – PEC [email protected] Tax code and VAT number 07485920966 – R.E.A. MI-1962358 Privacy Policy - ISO Certifications