Giacomo Lanzi
Giacomo Lanzi
Mitre Att&ck ™: an overview
Mitre Att&ck is a global knowledge base of adversary tactics and techniques based on real observations of cyber attacks. These are displayed in arrays organized by attack tactics, from initial system access and data theft to machine control. There are arrays for common desktop platforms (Linux, macOS and Windows) and for mobile ones.
What is MITRE ATT&CK ™ and what does it mean?
ATT&CK stands for “adversarial tactics, techniques, and common knowledge” and that is: tactics, adversary techniques and common knowledge. Let’s try to go deeper.
Tactics and techniques are a modern way of thinking about cyber attacks. Rather than looking at the results of an attack – an indicator of compromise (IoC) – security analysts should look at the tactics and techniques that indicate an attack is in progress. Tactics represent the goal you want to achieve, while techniques represent how an opponent plans to achieve it.
Common knowledge is the documented use of tactics and techniques used by opponents. Essentially, common knowledge is the documentation of the procedures used by the attacker. Those familiar with cybersecurity may be familiar with the term “tactics, techniques and procedures” or TTP. This same concept has been used by ATT&CK ™, replacing the term procedure with common knowledge.
Who is MITRE and what is the goal of ATT&CK ™?
MITRE is a US government funded research organization based in Bedford, MA, and McLean, VA. The company was spun off from MIT in 1958 and was involved in a number of top secret commercial projects for various agencies. These included the development of the FAA’s air traffic control system and the AWACS radar system. MITRE has a substantial cybersecurity practice funded by the National Institute of Standards and Technology (NIST).
A curiosity: the word Mitre means nothing. Apparently one of the first members, James McCormack, wanted a name that meant nothing but was evocative. Some mistakenly think it means Massachusetts Institute of Technology Research and Engineering.
ATT&CK’s goal is to create a comprehensive list of known opponent tactics and techniques used during a cyber attack. Open to governmental, educational and commercial organizations, it should be able to gather a wide, and hopefully comprehensive, range of attack phases and sequences. MITRE ATT&CK aims to create a standard taxonomy to make communications between organizations more specific.
How is the ATT&CK ™ matrix used?
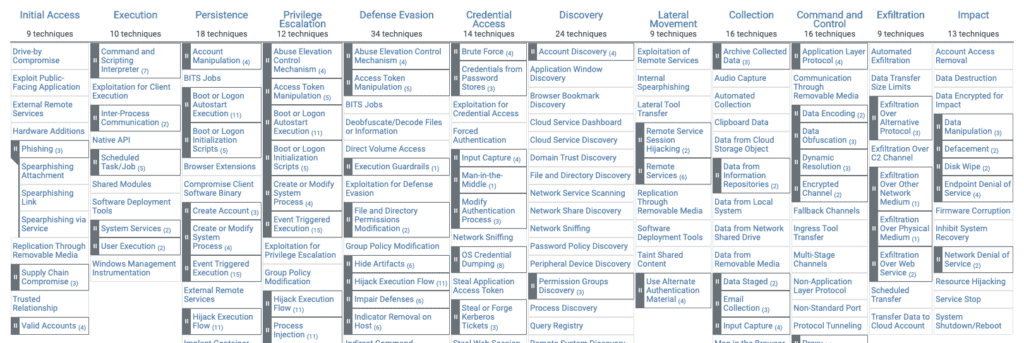
The matrix visually organizes all known tactics and techniques in an easy to understand format. Attack tactics are shown above, and individual techniques are listed below in each column. An attack sequence would involve at least one technique per tactic, and a complete attack sequence would be constructed by moving from left (Initial Access) to right (Command and Control). It is possible to use more techniques for a single tactic. For example, an attacker might try both a Spearphishing Attachment and a Spearphishing Link as initial login tactics.
Here is an example of a matrix:
In this matrix there are all the phases of an attack sequence. It is organized so that the tactics are ordered from right to left according to the attack sequence. Under each tactic the corresponding techniques, some of which contain sub-techniques. The two techniques mentioned above are actually sub-techniques of phishing which are part of the first step in the sequence (first column on the left).
Example
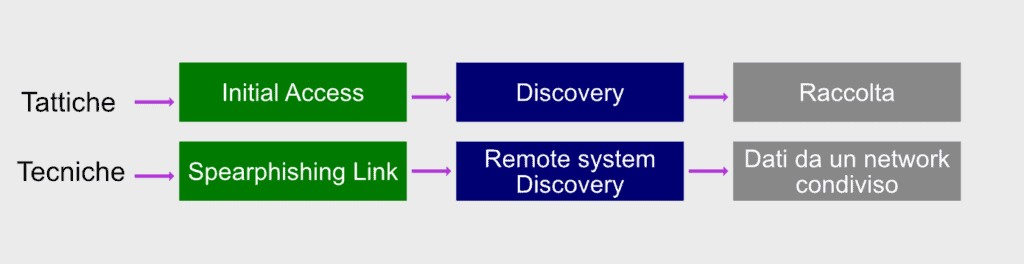
It is not necessary for an attacker to use all eleven tactics at the top of the matrix. Rather, the attacker will use the minimum number of tactics to achieve his goal, as it is more efficient and provides less chance of discovery. In this attack (illustrated in the diagram below), the adversary performs initial access to the CEO’s administrative assistant credentials using a Spearphishing link delivered in an email. Once in possession of the administrator’s credentials, the attacker searches for a Remote System Discovery of the Discovery phase.
Let’s say they’re looking for sensitive data in a Dropbox folder that the admin also has access to, so there’s no need to increase privileges. The collection, which is the last stage, is done by downloading the files from Dropbox to the attacker’s machine.
Note that if you are using behavior analysis, a security analyst could detect the attack in progress by identifying abnormal user behavior.
And that’s exactly what a SOC should do, here, roughly, how the attack could be mitigated: suppose the administrator clicked a link that no one in the company has ever clicked before, then the administrator logged in a particular Dropbox folder at an unusual time. During the final phase of the attack, the attacker’s computer entered the Dropbox folder for the first time. With behavioral analysis, these activities would be flagged as suspicious user behavior.
To consult ATT&CK
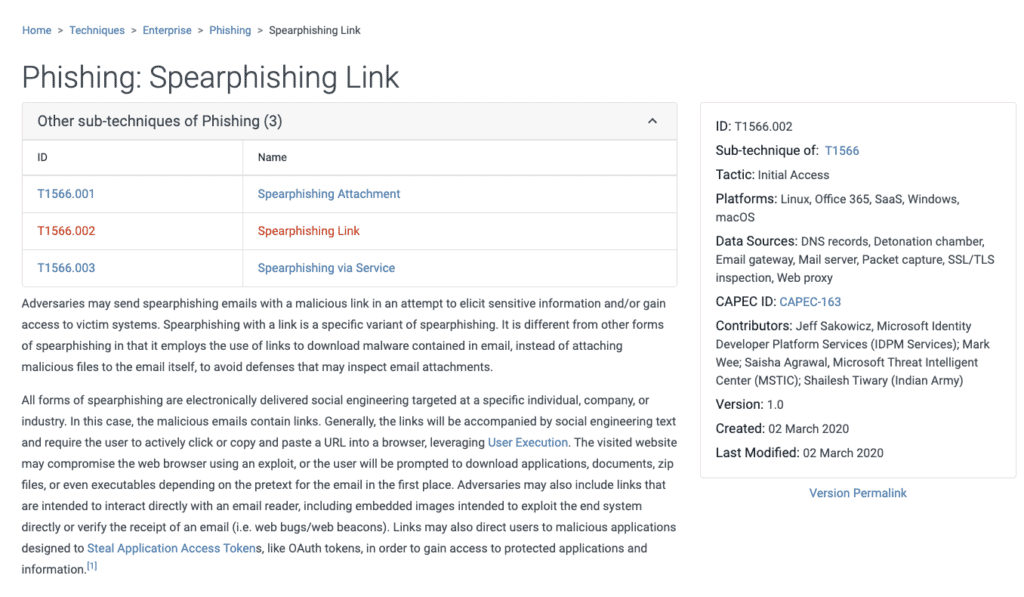
To consult this resource just visit his site and you will find yourself in front of the matrix of which I published a screenshot a little while ago. Suppose we want to consult the Spearphishing Link technique. By clicking on it, the corresponding page will open containing in-depth information about it, such as a description of the technique, what sub-techniques exist, examples of procedures that include it and suggestions for risk mitigation.
Basically all the information necessary to know and defend oneself appropriately from each technique is available.
Conclusions
The advantages of a resource like MITRE ATT&CK are truly remarkable. Cyber security teams have a valuable ally at their disposal, to which they can add dedicated tools for its consultation.
While it is almost certain that attackers are adapting as defenders deploy new skills, it is also true that ATT&CK provides a way to describe the new techniques they develop.
[btnsx id=”2931″]
Useful links:
Security: Pentest and verification of vulnerabilities
What is a Network Lateral Movement and how to defend yourself
Is SOCaaS useful for your business?
Computer network security: PT vs. VA
Customers
Twitter FEED
Recent activity
-
SecureOnlineDesktop
Estimated reading time: 6 minutes L'impatto crescente delle minacce informatiche, su sistemi operativi privati op… https://t.co/FimxTS4o9G
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The growing impact of cyber threats, on private or corporate operating systems… https://t.co/y6G6RYA9n1
-
SecureOnlineDesktop
Tempo di lettura stimato: 6 minuti Today we are talking about the CTI update of our services. Data security is… https://t.co/YAZkn7iFqa
-
SecureOnlineDesktop
Estimated reading time: 6 minutes Il tema della sicurezza delle informazioni è di grande attualità in questo peri… https://t.co/tfve5Kzr09
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The issue of information security is very topical in this historical period ch… https://t.co/TP8gvdRcrF
Newsletter
{subscription_form_1}© 2023 Secure Online Desktop s.r.l. All Rights Reserved. Registered Office: via dell'Annunciata 27 – 20121 Milan (MI), Operational Office: via statuto 3 - 42121 Reggio Emilia (RE) – PEC [email protected] Tax code and VAT number 07485920966 – R.E.A. MI-1962358 Privacy Policy - ISO Certifications