Giacomo Lanzi
Giacomo Lanzi
Application programming interface: our User API
In the IT development process, sooner or later we come across API services, which stands for Application Programming Interface. To date it is impossible to imagine IT development without. With the API it is possible to connect a service to an application and integrate it efficiently. Before introducing the specific APIs of the Cloud Server service, it is good to know broadly what an API is and why they are so used in computer science.
What is an API and how does it work?
An Application Programming Interface is like an open language, whose rules are shared by a certain service. By teaching the rules of language to an application, it can communicate with the service and access all the functions and data that are available.
Speaking a little more formal: the API is an interface that allows an app to interact with an external service through a set of commands. It is not necessary to know the internal logic of the service, just use a simple command and the service will return the requested data.
I want to propose an analogy that can be useful to understand this tool. When you enter a restaurant and talk to a waiter, you can order the dishes, ask questions on the menu, ask for the bill and so on. This person is like a filter that separates you from all the complications behind the scenes. You won’t have to worry about dishes, ovens, staff or food reserves. The waiter becomes the interface that allows you to take advantage of all the services, without having to worry about how a restaurant works. Here, the waiter can be interpreted as the API of the restaurant.
The specific command, the request (or call) method and the syntax to be used, are information described in the documentation of the service that offers the application programming interfaces.
Purposes
This powerful tool is now everywhere, so much so that often we do not even realize how many services we use via API. Mainly application programming interfaces are a great way to do one of the following:
Exchange of data
In the restaurant example, asking the waiter a question is like exchanging data. It would be like an answer to a question regarding the data made available.
Hide complex parts and perform operations
In the restaurant example, you don’t need to know how to cook a perfect lasagna, you will just order it. The request requires that the service provide a product, not simply raw data.
Extend functionality
For example, in mobile operating systems, widgets, which display useful information on the screen as part of the background, are used through APIs. The OS requires the app that provides the widget, all the information it needs to correctly show this functionality. This is also done via API.
Increase security
Since it is the OS that manages the authorizations for the use of the various hardware components, it is in charge of requesting the user for authorization to share a component. The SO is therefore responsible for the security and management of the data collected by the sensors of the mobile phone.
To learn more about the API topic, we share an explanation video from the Simply Explained channel.
Secure Online Desktop User API
Secure Online Desktop provides its User API to enable complete control of your account and services from your apps / systems. Through the HTTP REST API made available, it is also possible to resell the services with the white label formula, thus being able to brand the services in complete freedom.
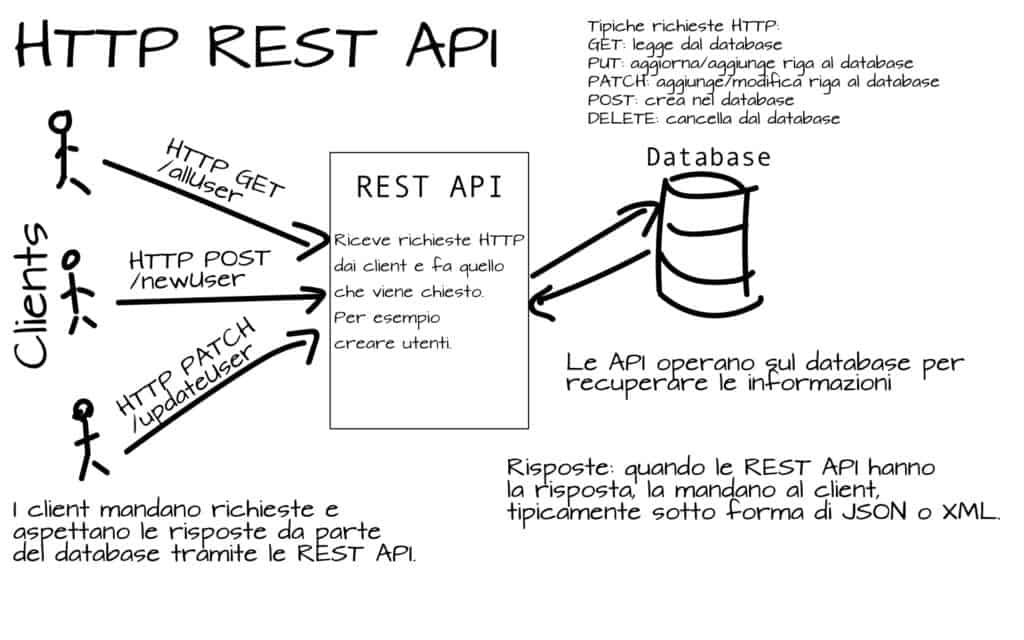
HTTP REST API
This type of API is characterized by communication via HTTP protocol and compliance with architectural principles defined as REpresentational State Transfer. If the HTTP protocol and its communication methods are well known and widely understood, perhaps it is good to mention the REST principles.
In a university analysis published as a thesis by Roy Fielding, the principles for a software architecture that would allow us to see the Web as a distributed computing platform were analyzed. According to this analysis, which hypothesized a generic architecture, the Web was found to have all that is needed to be considered a perfect platform for distributed processing.
A set of API which respects the REST logic hypothesized in 2000 by Roy Fielding, is called RESTful API. Although the terms create confusion, in reality they perfectly reflect the concept that REST is not a technology or a language, but are simply guidelines that can be respected or not.
White Label
Our APIs are offered specifically to offer the possibility to our customers to offer our services in white label mode. This means that our services can be offered to the customers of our customers, without them realizing anything.
The practice of white label, in fact, consists precisely in offering products without brands, with the specific aim of encouraging the rebranding of the service. Another interesting advantage derived from the use of APIs.
Conclusions
In addition to the possibility of offering our services to your customers in white label, you can also use the API to implement the services directly in your apps, expanding the available development possibilities.
The APIs are offered with complete documentation of all the request methods offered. A multitude of different API calls are allowed including management of users, domains, DNS, virtual machines and much more.
Summarizing, through SOD’s HTTP REST API it is possible:
1. implement access to virtual machines, hypervisors, network, disks, backups and much more in their applications
2. offer our re-branded services to your customers
Request further information or advice.
Useful links:
Customers
Twitter FEED
Recent activity
-
SecureOnlineDesktop
Estimated reading time: 6 minutes L'impatto crescente delle minacce informatiche, su sistemi operativi privati op… https://t.co/FimxTS4o9G
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The growing impact of cyber threats, on private or corporate operating systems… https://t.co/y6G6RYA9n1
-
SecureOnlineDesktop
Tempo di lettura stimato: 6 minuti Today we are talking about the CTI update of our services. Data security is… https://t.co/YAZkn7iFqa
-
SecureOnlineDesktop
Estimated reading time: 6 minutes Il tema della sicurezza delle informazioni è di grande attualità in questo peri… https://t.co/tfve5Kzr09
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The issue of information security is very topical in this historical period ch… https://t.co/TP8gvdRcrF
Newsletter
{subscription_form_1}© 2024 Cyberfero s.r.l. All Rights Reserved. Sede Legale: via Statuto 3 - 42121 Reggio Emilia (RE) – PEC [email protected] Cod. fiscale e P.IVA 03058120357 – R.E.A. 356650 Informativa Privacy - Certificazioni ISO