 Giacomo Lanzi
Giacomo Lanzi
“Left of boom” and “right of boom”: having a winning strategy
Tempo di lettura stimato: 7 minutes
Quando parliamo di “left of boom” o “right of boom” ci riferiamo ad un concetto che all’apparenza può sembrare superficiale. Invece, è un potente strumento che offre la possibilità di analizzare i conflitti di sicurezza sia da un punto di vista offensivo che da uno difensivo. In una ipotetica linea temporale di un attacco, ciò che si trova alla sua sinistra (left of boom) si riferisce a quello che accade prima. Analogamente, ciò che sta alla destra, è quello che avviene dopo.
Nel linguaggio comune molto spesso anziché “boom” si utilizza il termine “bang”, ma il significato resta comunque invariato. Si tratta, in sostanza, dell’evento stesso intorno al quale si analizza il periodo precedente e successivo.
Quindi, “left of boom” è l’insieme di eventi che si verificano prima dell’attacco. “Right of boom”, invece, è l’insieme di eventi che seguono il “boom”. Questa è la differenza sostanziale tra i due termini. Se le azioni difensive riescono a rilevare gli eventi nel periodo “left of boom”, è possibile trovare e adottare soluzioni per prevedere quando accadrà il “boom”.
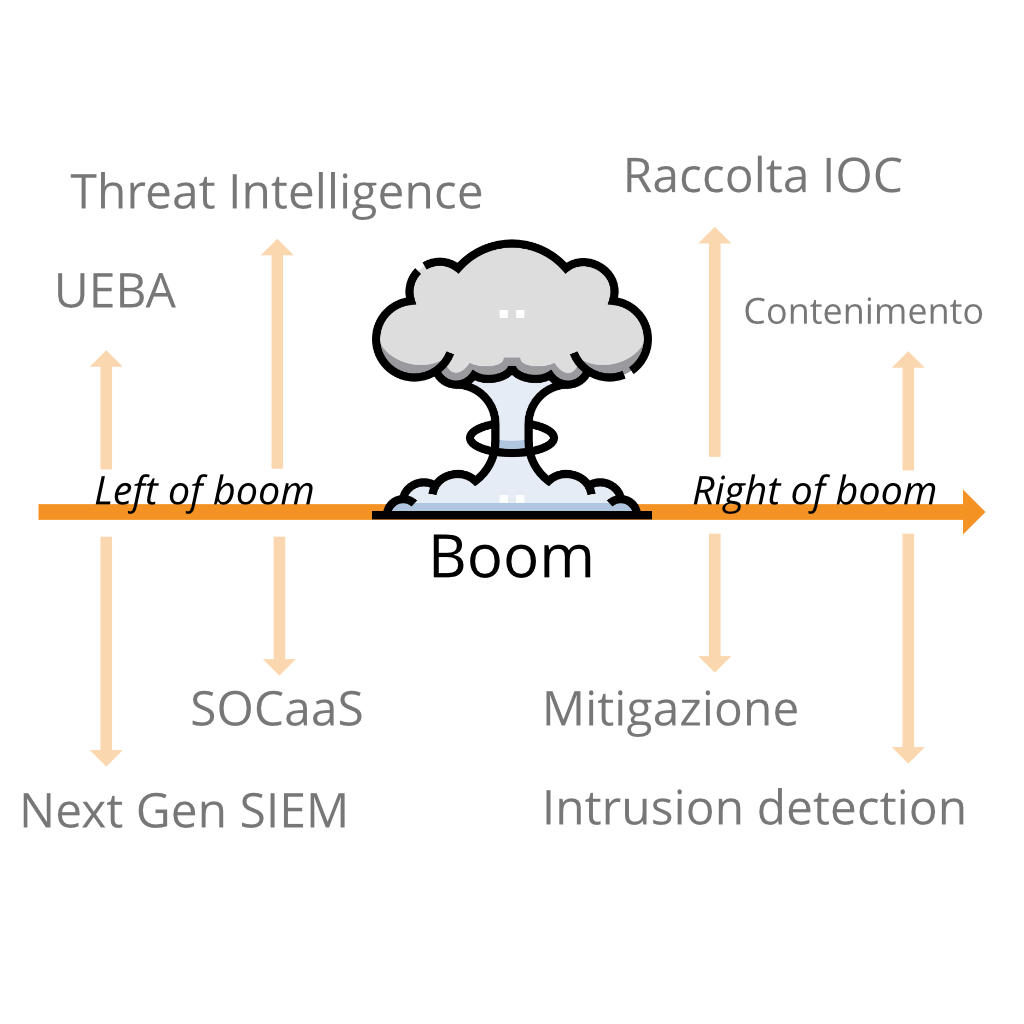
Per una persona inesperta nell’ambito della sicurezza informatica, questi concetti riguardanti la linea temporale di un attacco informatico potrebbero non essere nemmeno presi in considerazione, per questo motivo molte aziende preferiscono avvalersi di un SOCaaS.
Left of Boom
Un buon penetration tester riesce a rilevare alcuni eventi di tipo “left of boom”, ma spesso si tralascia la raccolta di informazioni sulle minacce. Certe volte non è in grado di distinguere tra loro concetti come “ingegneria della sicurezza, scoperta e risoluzione delle vulnerabilità” da un “controllo di prevenzione automatizzato”.
Non esiste in realtà un vero strumento valido di prevenzione, più che altro i controlli di sicurezza sono controlli di rilevamento. Alcuni di questi controlli integrano dei meccanismi di risposta automatizzati che impediscono il susseguirsi di spiacevoli eventi.
Un’applicazione web che previene attacchi di tipo XSS o SQLI è davvero utile per rilevare input non validi e risponde scartando il contenuto prima che l’iniezione possa verificarsi.
Un firewall progettato per bloccare le porte rileva semplicemente il traffico indesiderato in relazione al protocollo usato per la connessione e al numero della porta verso la quale si desidera accedere, interrompendo e reimpostando la richiesta di connessione.
Questi esempi si legano bene al concetto di “right of boom”. I controlli di prevenzione rilevano il “boom”, l’evento, e rispondono immediatamente arginando i possibili danni. “Left of boom” e “right of boom” sono così vicini nella linea temporale che sono difficilmente distinguibili, fino a quando non si esegue un’analisi accurata degli eventi.
Questo è uno dei motivi per cui i professionisti, nell’ambito della sicurezza informatica, amano i controlli di prevenzione. Lavorano rapidamente per correggere gli errori prima che gli hacker riescano a raggiungere i loro obbiettivi, limitando i danni.
Un SOCaaS in questi casi è una delle soluzioni migliori da adottare per proteggere l’integrità di un sistema informatico.
Right of Boom
Generalmente minore è la distanza tra “right of boom” e il tempo di risposta ad una minaccia, minori sono le conseguenze provocate da un eventuale attacco informatico. Ovviamente questa è solo una considerazione logica, non vale come regola assoluta.
Per alcune violazioni, la linea temporale tra l’evento e l’eliminazione completa della minaccia è discutibile, poiché il rilevamento è avvenuto dopo che l’hacker ha raggiunto il suo obbiettivo. Se gli hacker riescono ad infiltrarsi nel sistema ma vengono fermati in tempo, non arrecando nessun danno all’infrastruttura. In questo secondo caso, quindi, non c’è il “boom” di cui stiamo parlando.
Un esempio di right of boom
Per spiegare meglio il concetto di “right of boom” potremmo prendere come esempio un comune “malware”. I malware generalmente vengono sviluppati per attaccare in massa molti dispositivi, senza tanta discrezione. Con “right of boom” ci riferiamo a quel periodo di tempo che è passato da quando è avvenuta l’infezione da parte del malware.
Se hai letto gli altri articoli pubblicati da noi avrai appreso come gli hacker utilizzano queste tipologie di infezioni allo scopo di raccogliere informazioni sensibili, che vengono rivendute ad un terzo soggetto. Se il “right of boom” è più breve del tempo che l’hacker impiega per vendere queste informazioni, il danno può essere contenuto.
I migliori sistemi di sicurezza riescono ad accorciare il tempo “right of boom” riuscendo a raccogliere informazioni sugli attaccanti nel “left of boom”. Ci si può riuscire implementando delle contromisure in base al modello di minaccia. Questi strumenti permettono di scansionare intere infrastrutture, osservando i nuovi indicatori di minaccia giorni o addirittura settimane prima che gli attacchi si distribuiscano.
Come abbiamo visto anche in altri articoli, non sempre gli attacchi si svolgono in breve tempo. È, anzi, più probabile che gli hacker coinvolti agiscano in un primo, lento, periodo solo per raccogliere le informazioni necessario per sferrare l’attacco. Nel periodo “right of boom”, tornano utili strumenti come la cyber threat intelligence e un team di threat hunting.

Perché sono importanti i concetti “Right e Left of boom”
Se ci mettessimo nell’ottica dell’hacker, il concetto di “right of boom” e di “left of boom” può aiutare a decidere quale schema d’azione sia meglio intraprendere.
Supponiamo il caso in cui un hacker abbia a disposizione due metodi per potersi introdurre in un sistema informatico. Se uno dei due metodi potrebbe venire rilevato nel periodo “left of boom”, invece l’altro nel “right of boom”, è ovvio che l’hacker preferirà il secondo. Infatti, questo garantirebbe maggiori probabilità di successo dell’attacco.
Analogamente, tra due metodi che possono essere rilevati “right of boom” si sceglie quello che ha più possibilità di venir scoperto in ritardo. Più tempo passa dal boom alla rilevazione, maggiori sono le probabilità di successo. Questo tipo di ragionamento è importante per determinare quale tattica ha una linea temporale più ampia.
Ragionare in quest’ottica non è affatto semplice, richiede delle conoscenze avanzate da parte dell’esperto di sicurezza. Richiede inoltre il dover prendere in considerazione tutte quelle ipotesi che potrebbero potenzialmente determinare il successo dell’hacker.
Velocità
Un hacker è in grado di riuscire a prevedere se, utilizzando determinate tattiche, riuscirebbe a raggiungere l’obbiettivo più velocemente rispetto all’esperto che cerca di rilevare gli attacchi. Il “boom” è il primo contatto, nell’insieme delle tattiche d’intrusione utilizzate per accedere illegalmente ad un sistema informatico. Le rimanenti tattiche si collocano prima e dopo di esso.
Velocità e furtività solitamente si annullano a vicenda. Infatti, molto spesso si può essere più veloci sacrificando parte della furtività.
Velocità e furtività non vanno molto d’accordo quando parliamo di attacchi informatici. Essere furtivi, evitando di lasciare tracce, richiede più attenzione e quindi inevitabilmente anche più tempo. Tuttavia se lo scopo di un hacker non è un singolo obbiettivo ma una serie di più obbiettivi, l’essere veloci può rivelarsi efficace.
Per difendersi dagli attacchi, è possibile raccogliere gli indicatori di compromissione (IOC) per rimediare alle vulnerabilità presenti e per introdurre nuovi controlli di rilevamento, rendendo più sicuro il sistema informatico.
Conclusioni
È importante conoscere il concetto di linea temporale degli attacchi e abbiamo visto come i concetti di “left of boom” e “right of boom” influenzino i meccanismi di risposta alle minacce di intrusione.
I concetti che abbiamo visto in questo articolo, nonostante non aggiungano niente di concreto alle tecniche di difesa o di attacco di un sistema, offrono un punto di vista. Nella continua lotta tra hacker e operatori di sicurezza, avere una strategia vincente significa non solo disporre di strumenti efficienti, ma anche pianificare in modo dettagliato ogni dettaglio, prima e dopo gli attacchi.
Per sapere come un SOCaaS può aiutarti a monitorare l’infrastruttura aziendale e cogliere gli indizi “left of boom”, non esitare a contattarci, sapremo rispondere a ogni domanda e ti offriremo una soluzione per la tua azienda.
Useful links:
Customers
Twitter FEED
Recent activity
-
SecureOnlineDesktop
Estimated reading time: 6 minutes L'impatto crescente delle minacce informatiche, su sistemi operativi privati op… https://t.co/FimxTS4o9G
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The growing impact of cyber threats, on private or corporate operating systems… https://t.co/y6G6RYA9n1
-
SecureOnlineDesktop
Tempo di lettura stimato: 6 minuti Today we are talking about the CTI update of our services. Data security is… https://t.co/YAZkn7iFqa
-
SecureOnlineDesktop
Estimated reading time: 6 minutes Il tema della sicurezza delle informazioni è di grande attualità in questo peri… https://t.co/tfve5Kzr09
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The issue of information security is very topical in this historical period ch… https://t.co/TP8gvdRcrF
Newsletter
{subscription_form_1}© 2023 Secure Online Desktop s.r.l. All Rights Reserved. Registered Office: via dell'Annunciata 27 – 20121 Milan (MI), Operational Office: via statuto 3 - 42121 Reggio Emilia (RE) – PEC [email protected] Tax code and VAT number 07485920966 – R.E.A. MI-1962358 Privacy Policy - ISO Certifications












