Node.js via SOD hosting panel
Home » Node.js via SOD hosting panel
 Giacomo Lanzi
Giacomo Lanzi
Node.js via SOD hosting panel
If you are interested in hosting Node.js apps on your web space, we have good news! The control panel offered by SOD, based on Plesk, is equipped with a Node.js extension that allows you to easily manage applications. In this article we see how it is possible to integrate Node through the control panel.
Host a Node.js application from the Plesk panel
To verify that everything is working, let’s try hosting a Node.js application in the panel. We will use a generic “Hello, World” application. To do this, we will use the Git extension that you find directly from the panel. It would also be possible to upload the application directly to the server, but I thought that implementing a second extension could also be useful for the purposes of this mini guide.
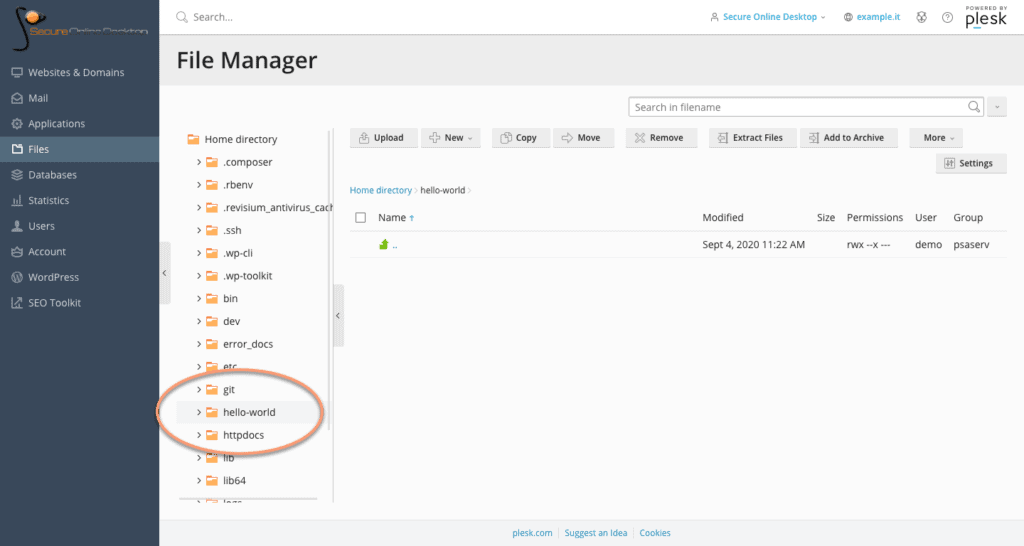
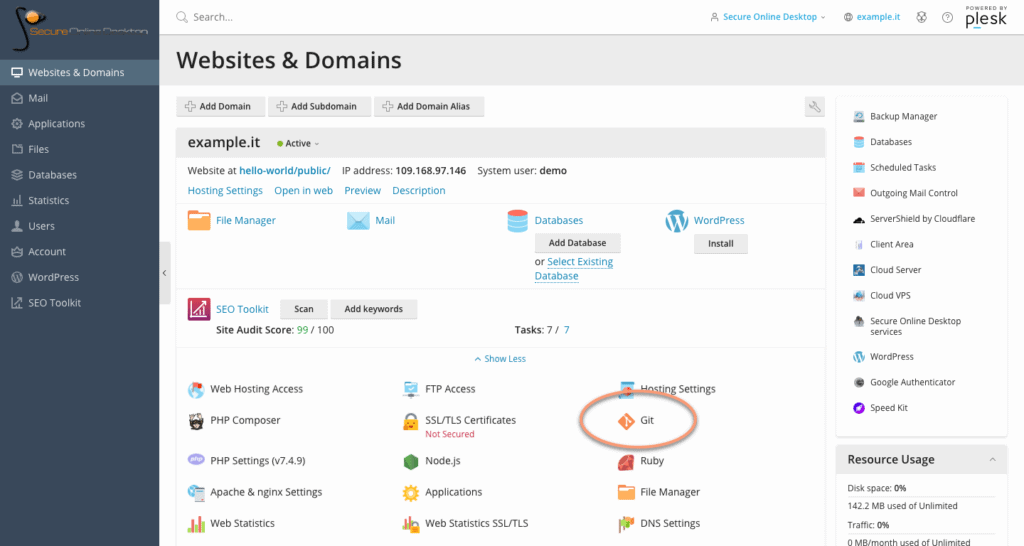
Once you have accessed the SOD Plesk panel, you will need to create a destination folder for the application. Select the “Files” tab, create a “hello-world” folder. From the “Websites & Domains” tab, among the available components, select Git. If you own more than one domain, be sure to select the option under the correct one.
The second screen on where to find the Git icon:
Setting up a local repository
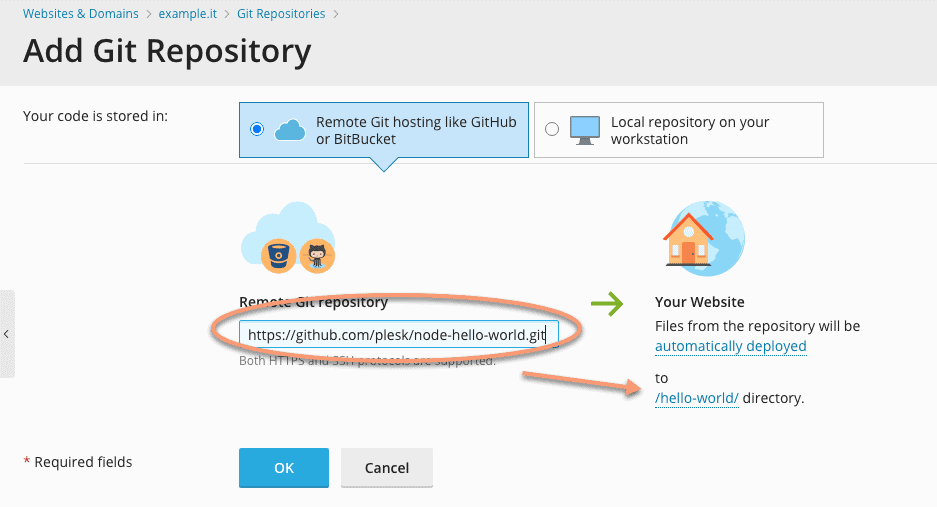
Now let’s set up a local repository as a clone of a remote one to download the code to the folder you created a moment ago. The URL of the repository we will clone is: https://github.com/plesk/node-hello-world.git
To do this, click on the Git icon, set the URL in the space provided and select the “hello-world” folder you created a while ago.
Differences between “Application root” and “Document root” folders
The next step is to change the Document root folder for the domain. Note that the Document root and Application root folders are not the same. When we talk about web apps (such as those based on Node.js), the document root is the position where the static resources are located, while the application root is the root directory where the app. In most cases, the Document root is a folder within the Application root.
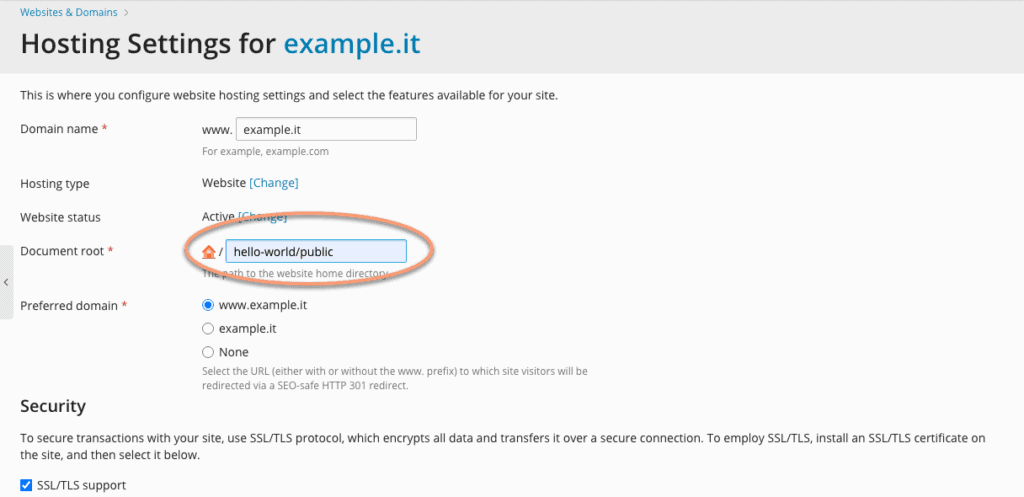
Right now we need to change the document root. To do this, go to the “Websites & Domains” panel, select the correct site and go to “Hosting Settings” (right above Git) and click the link:
Change the current “Document root” to hello-world/public.
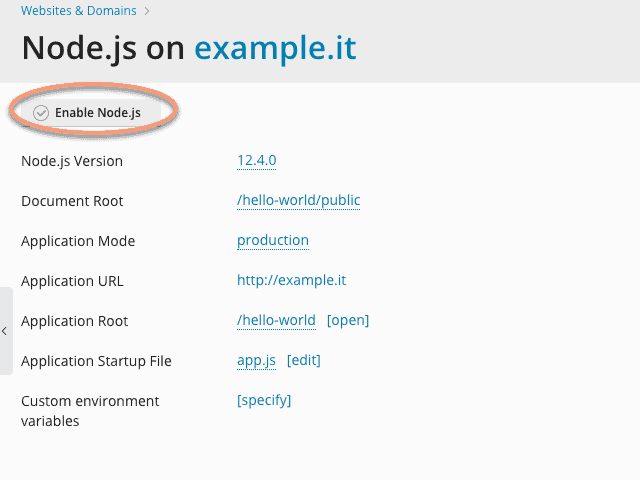
Enable support for Node.js
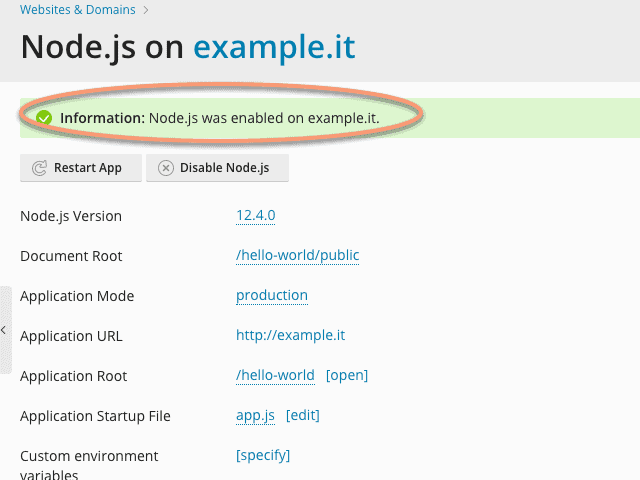
Before running the “Hello World” app, the last thing you need to do is enable support for Node.js on the domain. Then go to the “Websites & Domain” panel and click on the appropriate option. Here you can see some information about the app. Click on “Enable Node.js” and in a few moments this will be enabled.
At this point, if everything went well, clicking on the “Application URL” you should see a screen that says “Hello World!”. Congratulations, you have just installed and run an app on your domain.
Applications with dependencies
Applications built with Node.js, more often than not, must satisfy dependencies that are defined in the package.json file, which is installed in the “node_modules” directory.
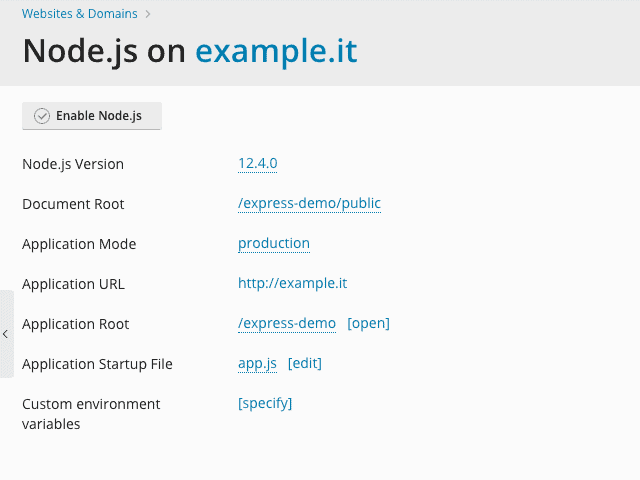
Let’s look at another ExpressJS-based application. You can find it in its repository, upload it manually, or repeat the steps described in the previous section. Here is the repository: https://github.com/plesk/node-express.git. Once you have things sorted out, you will find yourself as in the screenshot below, assuming you have cloned the repository in the express-demo folder:
Install the dependencies and change the startup file
Before trying to access the app, you need to initialize it. Let’s start by installing the dependencies. Fortunately, in the Plesk panel of SOD, there is a simple “NPM install” button. This is done to install app dependencies based on the “package.json” file. Install the dependencies this way, for convenience.
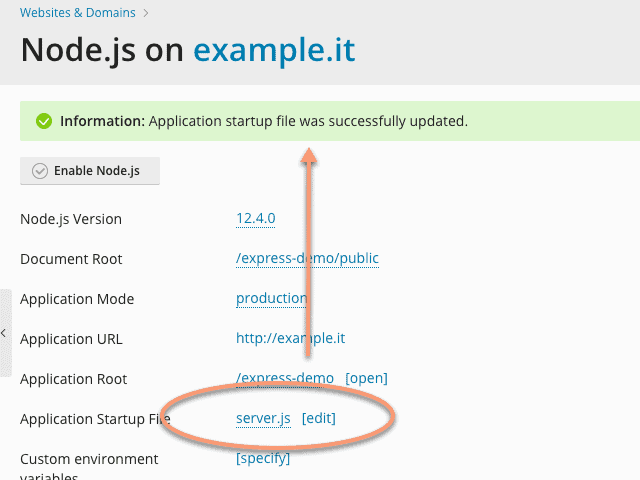
Finally, we need to set up the app’s startup file. Plesk uses the Phusion Passenger server application to service the Node.js apps. In the demonstration repository, there is a file called “server.js”. This, which is not a common part of ExpressJS-based apps, contains a few lines of code necessary to make the app work:
const app = require (‘./ app’);
const http = require (‘http’);
http.createServer (app) .listen (process.env.PORT);
You can use the idea behind this file when hosting other Node.js applications, for example based on a different framework. The last thing you have to do is change the “Application Startup File” option and set it to “server.js”.
At this point, browsing to the address that hosts the app, you should see the ExpressJS welcome screen.
Solve problems
For every Node.js developer it is essential to know how to identify problems to find a solution. To do this, here are a couple of tips that might help you Debug.
Checking the log file
The first thing to do when debugging a Node.js application is to check the log files. For example, if you forget to install the dependencies for the Express demo app, the server error log will contain the error “cannot find module ‘express'”. Unfortunately, due to how Phusion Passenger works, server level error logs are used instead of per domain error logs. In this case, end users will see a simple generic error message.
To check the server log messages, go to the “Websites & Domain” panel, under the domain concerned, look for the log option. Clicking on it will give you access to a screen of the logged messages.
See messages directly on the app screen
It can be very useful to see the error messages directly on the app website, without looking for the option in the control panel. Go to the Node.js app settings screen and change the application mode to “development”. The next time a problem occurs, the error will be shown in the browser window.
Furthermore, if the app is in “development” mode, it is not necessary to restart the app every time you change the contents of a file.
Conclusions
As we have seen, implementing Node.js applications on your domain is really simple with the Plesk control panel of the SOD hosting service, which is once again very flexible, intuitive and easy to use.
If you want to try this and other features, you can test the demo version by simply clicking here.
Useful links:
VPS hosting services – Cloud server
Share
RSS
More Articles…
- NIS: what it is and how it protects cybersecurity
- Advanced persistent threats (APTs): what they are and how to defend yourself
- Penetration Testing and MFA: A Dual Strategy to Maximize Security
- Penetration Testing: Where to Strike to Protect Your IT Network
- Ransomware: a plague that brings companies and institutions to their knees. Should you pay the ransom? Here is the answer.
- Why IT audit and log management are important for Cybersecurity
- Red Team, Blue Team and Purple Team: what are the differences?
- Mercedes’ Oversight Puts Company Secrets at Risk: Why Cyber Threat Intelligence is Critical
Categories …
- Backup as a Service (18)
- Acronis Cloud Backup (11)
- Veeam Cloud Connect (4)
- Cloud Conference (3)
- Cloud CRM (1)
- Cloud Server/VPS (22)
- Conferenza Cloud (4)
- ICT Monitoring (5)
- Log Management (2)
- News (24)
- ownCloud (4)
- Privacy (7)
- Secure Online Desktop (14)
- Security (203)
- Cyber Threat Intelligence (CTI) (8)
- Deception (4)
- Ethical Phishing (11)
- Netwrix Auditor (2)
- Penetration Test (11)
- Posture Guard (3)
- SOCaaS (65)
- Vulnerabilities (84)
- Web Hosting (15)
Tags
 darkreading
darkreading
- Licensed to Bill? Nations Mandate Certification & Licensure of Cybersecurity Pros April 23, 2024Malaysia, Singapore, and Ghana are among the first countries to pass laws that require cybersecurity firms — and in some cases, individual consultants — to obtain licenses to do business, but concerns remain.
- ToddyCat APT Is Stealing Data on 'Industrial Scale' April 22, 2024The threat actor is deploying multiple connections into victim environments to maintain persistence and steal data.
- Nespresso Domain Serves Up Steamy Cup of Phish, No Cream or Sugar April 22, 2024An open direct vulnerability in the Nespresso Web domain lets attackers bypass detection as they attempt to steal victims' Microsoft credentials.
- MITRE ATT&CKED: InfoSec's Most Trusted Name Falls to Ivanti Bugs April 22, 2024The irony is lost on few, as a nation-state threat actor used eight MITRE techniques to breach MITRE itself — including exploiting the Ivanti bugs that attackers have been swarming on for months.
- Zero-Trust Takes Over: 63% of Orgs Implementing Globally April 22, 2024Though organizations are increasingly incorporating zero-trust strategies, for many, these strategies fail to address the entirety of an operation, according to Gartner.
- Where Hackers Find Your Weak Spots April 22, 2024The five intelligence sources that power social engineering scams.
- CISO Corner: Breaking Staff Burnout, GPT-4 Exploits, Rebalancing NIST April 19, 2024SecOps highlights this week include the executive role in "cyber readiness;" Cisco's Hypershield promise; and Middle East cyber ops heat up.
- Miggo Launches Application Detection and Response (ADR) Solution April 19, 2024
- FBI Director Wray Issues Dire Warning on China's Cybersecurity Threat April 19, 2024Chinese actors are ready and poised to do "devastating" damage to key US infrastructure services if needed, he said.
- UNDP, City of Copenhagen Targeted in Data-Extortion Cyberattack April 19, 2024A ransomware gang claimed responsibility for the attack, though it is unknown if a ransom was demanded or paid.
 Full Disclosure
Full Disclosure
- BACKDOOR.WIN32.DUMADOR.C / Remote Stack Buffer Overflow (SEH) April 19, 2024Posted by malvuln on Apr 19Discovery / credits: Malvuln (John Page aka hyp3rlinx) (c) 2024 Original source: https://malvuln.com/advisory/6cc630843cabf23621375830df474bc5.txt Contact: malvuln13 () gmail com Media: twitter.com/malvuln Threat: Backdoor.Win32.Dumador.c Vulnerability: Remote Stack Buffer Overflow (SEH) Description: The malware runs an FTP server on TCP port 10000. Third-party adversaries who can reach the server can send a specially […]
- SEC Consult SA-20240418-0 :: Broken authorization in Dreamehome app April 19, 2024Posted by SEC Consult Vulnerability Lab via Fulldisclosure on Apr 19SEC Consult Vulnerability Lab Security Advisory < 20240418-0 > ======================================================================= title: Broken authorization product: Dreamehome app vulnerable version:
- MindManager 23 - full disclosure April 19, 2024Posted by Pawel Karwowski via Fulldisclosure on Apr 19Resending! Thank you for your efforts. GitHub - pawlokk/mindmanager-poc: public disclosure Affected application: MindManager23_setup.exe Platform: Windows Issue: Local Privilege Escalation via MSI installer Repair Mode (EXE hijacking race condition) Discovered and reported by: Pawel Karwowski and Julian Horoszkiewicz (Eviden Red Team) Proposed mitigation:...
- CVE-2024-31705 April 14, 2024Posted by V3locidad on Apr 14CVE ID: CVE-2024-31705 Title : RCE to Shell Commands" Plugin / GLPI Shell Command Management Interface Affected Product : GLPI - 10.X.X and last version Description: An issue in Infotel Conseil GLPI v.10.X.X and after allows a remote attacker to execute arbitrary code via the insufficient validation of user-supplied input. […]
- SEC Consult SA-20240411-0 :: Database Passwords in Server Response in Amazon AWS Glue April 14, 2024Posted by SEC Consult Vulnerability Lab via Fulldisclosure on Apr 14SEC Consult Vulnerability Lab Security Advisory < 20240411-0 > ======================================================================= title: Database Passwords in Server Response product: Amazon AWS Glue vulnerable version: until 2024-02-23 fixed version: as of 2024-02-23 CVE number: - impact: medium homepage: https://aws.amazon.com/glue/ found:...
- [KIS-2024-03] Invision Community <= 4.7.16 (toolbar.php) Remote Code Execution Vulnerability April 11, 2024Posted by Egidio Romano on Apr 10------------------------------------------------------------------------------ Invision Community
- [KIS-2024-02] Invision Community <= 4.7.15 (store.php) SQL Injection Vulnerability April 11, 2024Posted by Egidio Romano on Apr 10-------------------------------------------------------------------- Invision Community
- Multiple Issues in concretecmsv9.2.7 April 11, 2024Posted by Andrey Stoykov on Apr 10# Exploit Title: Multiple Web Flaws in concretecmsv9.2.7 # Date: 4/2024 # Exploit Author: Andrey Stoykov # Version: 9.2.7 # Tested on: Ubuntu 22.04 # Blog: http://msecureltd.blogspot.com Verbose Error Message - Stack Trace: 1. Directly browse to edit profile page 2. Error should come up with verbose stack trace […]
- OXAS-ADV-2024-0001: OX App Suite Security Advisory April 11, 2024Posted by Martin Heiland via Fulldisclosure on Apr 10Dear subscribers, We're sharing our latest advisory with you and like to thank everyone who contributed in finding and solving those vulnerabilities. Feel free to join our bug bounty programs for OX App Suite, Dovecot and PowerDNS at YesWeHack. This advisory has also been published at https://documentation.open-xchange.com/appsuite/security/advisories/html/2024/oxas-adv-2024-0001.html. […]
- Trojan.Win32.Razy.abc / Insecure Permissions (In memory IPC) April 11, 2024Posted by malvuln on Apr 10Discovery / credits: Malvuln (John Page aka hyp3rlinx) (c) 2024 Original source: https://malvuln.com/advisory/0eb4a9089d3f7cf431d6547db3b9484d.txt Contact: malvuln13 () gmail com Media: twitter.com/malvuln Threat: Trojan.Win32.Razy.abc Vulnerability: Insecure Permissions (In memory IPC) Family: Razy Type: PE32 MD5: 0eb4a9089d3f7cf431d6547db3b9484d SHA256: 3d82fee314e7febb8307ccf8a7396b6dd53c7d979a74aa56f3c4a6d0702fd098 Vuln ID: MVID-2024-0678...
Customers
Twitter FEED
Recent activity
-
SecureOnlineDesktop
Estimated reading time: 6 minutes L'impatto crescente delle minacce informatiche, su sistemi operativi privati op… https://t.co/FimxTS4o9G
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The growing impact of cyber threats, on private or corporate operating systems… https://t.co/y6G6RYA9n1
-
SecureOnlineDesktop
Tempo di lettura stimato: 6 minuti Today we are talking about the CTI update of our services. Data security is… https://t.co/YAZkn7iFqa
-
SecureOnlineDesktop
Estimated reading time: 6 minutes Il tema della sicurezza delle informazioni è di grande attualità in questo peri… https://t.co/tfve5Kzr09
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The issue of information security is very topical in this historical period ch… https://t.co/TP8gvdRcrF
Newsletter
{subscription_form_1}Products and Solutions
News
- NIS: what it is and how it protects cybersecurity April 22, 2024
- Advanced persistent threats (APTs): what they are and how to defend yourself April 17, 2024
- Penetration Testing and MFA: A Dual Strategy to Maximize Security April 15, 2024
- Penetration Testing: Where to Strike to Protect Your IT Network March 25, 2024
- Ransomware: a plague that brings companies and institutions to their knees. Should you pay the ransom? Here is the answer. March 6, 2024
Google Reviews

Ottima azienda, servizi molto utili, staff qualificato e competente. Raccomandata!read more
Ottimo supportoread more
E' un piacere poter collaborare con realtà di questo tiporead more
Un ottimo fornitore.
Io personalmente ho parlato con l' Ing. Venuti, valore aggiunto indubbiamente.read more

© 2023 Secure Online Desktop s.r.l. All Rights Reserved. Registered Office: via dell'Annunciata 27 – 20121 Milan (MI), Operational Office: via statuto 3 - 42121 Reggio Emilia (RE) – PEC [email protected] Tax code and VAT number 07485920966 – R.E.A. MI-1962358 Privacy Policy - ISO Certifications