
Estimated reading time: 6 minutes
I dati di threat intelligence forniscono alle aziende approfondimenti rilevanti e tempestivi necessari per comprendere, prevedere, rilevare e rispondere alle minacce alla sicurezza informatica. Le soluzioni di intelligence sulle minacce raccolgono, filtrano e analizzano grandi volumi di dati grezzi relativi a fonti esistenti o emergenti di minacce. Il risultato sono feed di threat intelligence e rapporti di gestione. I data scientist e i team di sicurezza utilizzano questi feed e report per sviluppare un programma con risposte mirate agli incidenti per attacchi specifici.
Tutti, dalla prevenzione delle frodi alle operazioni di sicurezza all’analisi dei rischi, traggono vantaggio dalla threat intelligence. Il software di intelligence sulle minacce fornisce visualizzazioni interattive e in tempo reale dei dati relativi alle minacce e alle vulnerabilità.
Il vantaggio offerto agli analisti ed esperti di sicurezza è evidente e serve a identificare facilmente e rapidamente i modelli degli attori delle minacce. Comprendere la fonte e l’obiettivo degli attacchi aiuta i capi d’azienda a mettere in atto difese efficaci per mitigare i rischi e proteggersi dalle attività che potrebbero avere un impatto negativo sull’azienda.
La cyber threat intelligence può essere classificata come strategica, tattica oppure operativa. Quella Strategica riguarda le capacità e gli intenti generali degli attacchi informatici. Di conseguenza anche lo sviluppo di strategie informate associate alla lotta contro le minacce a lungo termine. Quella Tattica riguarda le tecniche e le procedure che gli aggressori potrebbero utilizzare nelle operazioni quotidiane. Infine, la threat intelligence Operativa, fornisce informazioni altamente tecniche a livello forense riguardanti una specifica campagna di attacco.

Il ciclo della threat intelligence
Le soluzioni di intelligence sulle minacce raccolgono dati grezzi sugli attori e le minacce da varie fonti. Questi dati vengono poi analizzati e filtrati per produrre feed e rapporti di gestione che contengono informazioni che possono essere utilizzate in soluzioni automatizzate di controllo della sicurezza. Lo scopo principale di questo tipo di sicurezza è quello di mantenere le organizzazioni informate sui rischi delle minacce persistenti avanzate, delle minacce zero-day e degli exploit, e su come proteggersi da esse.
Il ciclo di intelligence delle minacce informatiche consiste nelle seguenti fasi.
Pianificazione: I requisiti dei dati devono essere prima definiti.
Raccolta: Si raccolgono grandi quantità di dati grezzi da fonti interne ed esterne di threat intelligence.
Elaborazione: I dati grezzi sono filtrati, categorizzati e organizzati.
Analisi: Questo processo trasforma i dati grezzi in flussi di informazioni sulle minacce con l’uso di tecniche analitiche strutturate in tempo reale e aiuta gli analisti a individuare gli indicatori di compromissione (IOC).
Diffusione: I risultati dell’analisi vengono immediatamente condivisi con i professionisti della sicurezza informatica e gli analisti di threat intelligence.
Feedback: Se tutte le domande trovano risposta, il ciclo si conclude. Se ci sono nuovi requisiti, il ciclo ricomincia dalla fase di pianificazione.
Indicatori comuni di compromissione
Le aziende sono sempre più sotto pressione per gestire le vulnerabilità della sicurezza e il panorama delle minacce è in continua evoluzione. I feed di threat intelligence possono aiutare in questo processo identificando gli indicatori comuni di compromissione (IOC). Non solo, possono anche raccomandare i passi necessari per prevenire attacchi e infezioni. Alcuni degli indicatori di compromissione più comuni includono:
Indirizzi IP, URL e nomi di dominio: Un esempio potrebbe essere un malware che prende di mira un host interno che sta comunicando con un noto attore di minacce.
Indirizzi e-mail, oggetto delle e-mail, link e allegati: Un esempio potrebbe essere un tentativo di phishing che si basa su un utente ignaro che clicca su un link o un allegato e avvia un comando dannoso.
Chiavi di registro, nomi di file e hash di file e DLL: Un esempio potrebbe essere un attacco da un host esterno che è già stato segnalato per un comportamento nefasto o che è già infetto.

Quali strumenti per la threat intelligence
Il crescente aumento del malware e delle minacce informatiche ha portato a un’abbondanza di strumenti di threat intelligence che forniscono preziose informazioni per proteggere le aziende.
Questi strumenti si presentano sotto forma di piattaforme sia open source che proprietarie. Queste forniscono una serie di capacità di difesa contro le minacce informatiche, come l’analisi automatizzata dei rischi, la raccolta di dati privati, strumenti di ricerca rapida di threat intelligence, la segnalazione e condivisione di queste informazioni tra più utenti, avvisi curati, analisi dei rischi di vulnerabilità, monitoraggio del dark web, mitigazione automatizzata dei rischi, threat hunting e molto altro.
Abbiamo parlato di uno di questi strumenti in un altro articolo: il Mitre Att&ck. Questo è uno strumento molto utile per conoscere i comportamenti e le tecniche di attacco hacker. Questo grazie alle informazioni raccolte dalla threat intelligence e la conseguente condivisione. Un framework come questo è molto efficiente per creare meccanismi difensivi che consentono di mettere in sicurezza le infrastrutture aziendali.
Intelligenza artificiale e informazioni sulle minacce
Come abbiamo visto prima, la raccolta di informazioni da varie fonti non è altro che una delle fasi. Queste devono poi venire analizzate e successivamente elaborate in protocolli di controllo, per essere davvero utili per la sicurezza.
Per questo tipo di lavori di analisi, definizione di comportamenti baseline e controllo dei dati ci si affida sempre di più all’intelligenza artificiale e al deep learning. Un Next Generation SIEM, affiancato a una soluzione UEBA sono perfetti per questo tipo di protezione.
Il controllo del comportamento delle entità all’interno del perimetro effettuato dal UEBA è in grado di identificare ogni comportamento sospetto, in base alle informazioni raccolte e analizzate dal SIEM.
Conclusioni
Gli strumenti di difesa che abbiamo nominato sono il valore primario di un piano di sicurezza aziendale. Adottare soluzioni specifiche, implementare la threat intelligence e quindi una ricerca attiva degli indicatori di minacce, offre una posizione di vantaggio strategica. L’azienda può operare un passo avanti ai criminali, i quali possono far leva solo sull’effetto sorpresa contro le loro vittime. Proprio per questa situazione generale, ogni azienda dovrebbe essere nelle condizioni di non farsi cogliere alla sprovvista. Implementare soluzioni proattive è ormai necessario.
La threat intelligence è quindi un’arma da difesa dietro la quale mettere al riparo le risorse più importanti per poter lavorare in tranquillità.
Se vuoi sapere come possiamo aiutarti con i nostri servizi dedicati alla sicurezza, non esitare a contattarci, saremo lieti di rispondere a ogni domanda.
Useful links:
Cyber Threat Intelligence (CTI) – maggiore efficacia per la sicurezza IT
Progetti di Secure Online Desktop
Cos’è la Cyber Security? Definizione e proposte
Prevenire il shoulder surfing e il furto di credenziali aziendali
Tempo di lettura stimato: 6 minutes
Today we are talking about the CTI update of our services. Data security is an aspect that must always be taken into consideration to prevent data from being stolen in any way.
Network problems
When you have a presence connected to the network, especially if it contains sensitive data, the potential threats to which you are exposed are manifold. The theft of your customers’ data, in fact, is only one of the potential negative situations that can arise and that could compromise the solidity of your site and the reputation of your company.
The Cyber Threat Intelligence (CTI) service, was created with the aim, not only of discovering which areas are most at risk, but also of preventing targeted attacks. Prevention represents the right solution thanks to which it is possible to avoid that the situation can become difficult to deal with and that there may be future complex problems to be solved.

CTI: preventive-threat analysis
Thanks to the CTI service we offer and our Cyber Treath Hunter , it is possible to prevent a planned attack hits. The search for vulnerable areas of the IT infrastructure represents the first process of the CTI service we propose.
This information, in fact, is that which is processed in the Dark Web , where most of the design of the attacks. The analysis of data leakage, therefore, is carried out with extreme care to understand what and how much data may have become the object of hacker attention . Consequently, we can also understand what specific attack targets or upcoming information at risk may be.
The various analyzes are carried out with care and precision, to avoid that vulnerabilities are exploited and the security of the structure jeopardized. Thanks to the analysis carried out by a team of professionals, your company will prevent attacks from hitting you and triggering economic and image problems .
The analyzes carried out by Cyber Threat Intelligence
As regards the different phases of the analyzes proposed by us, these are carried out in a particularly accurate manner. We practice a series of procedures thanks to which it is possible to identify what are the potential threats that may be present in the network.
Let’s look at these steps to understand how we go about offering a complete service to our customers.
Global-data analysis
After having hypothesized the type of threat to be avoided, then the necessary data that must be analyzed, the team of technicians in charge takes care of carrying out a series of information gathering procedures. Thanks to this we can understand if the necessary data are well protected or at risk of breach . Basically we try to think like hackers before they prepare for the attack.
The data are subjected to careful analysis and above all are adequately divided. This procedure was created to simplify the phase of studying the data themselves , thus preventing an accumulation of information that could lead to confusion during the analysis phase.
The data and the second-analysis, between fundamental and secondary information
Once the information gathering phase is complete, we move on to the initial analysis of the same. With this fundamental step it is possible to eliminate all the information deemed superfluous leaving space for those that have greater relevance in the study phase.
At this point, the data analysis phase takes place, the purpose of which is to actually understand what concrete threats to avoid can be.
During the study phase it is decided which are the different procedures to be adopted on the infrastructure to prevent attacks from being successful. Through these analyzes, we can then decide precisely how to further increase corporate data defenses.
The choice of security-measures to be adopted
Finally, there is the implementation of security practices with a specific task: to make the analysis results operational.
Here’s how, thanks to this set of procedures, the CTI service we offer is incredibly useful to avoid potential problems. We remind you that even a single attack carried out can have a significant impact in economic terms.
Prevention of future-attacks
Thanks to this set of CTI analyzes, you can, therefore, prevent future attacks. Our team is not only concerned with analyzing potential and future threats, but also those that may be based on the current situation of the IT infrastructure.
We want to underline, in fact, how constant threats are subject to rapid evolution and how important it is to always be adequately protected and prevented. With services like SOCaaS and CTI, we securely monitor the corporate network making sure it remains safe and healthy.

CTI: The importance of maximum-online-security
We therefore encourage you to consider these security risk situations as less remote than you might think. These same situations can be the cause of a series of breaches and data losses that can compromise the company.
Thanks to our SOCaaS, and especially the CTI. it is possible to avoid that the data present on the corporate network can be easily intercepted.
Understanding what the threats are, having a detailed report and above all analyzing the countermeasures that must be adopted is our task and thanks to our state-of-the-art systems we offer a complete service capable of putting the infrastructure in total safety.
Our services cover many security risk situations and we generally offer many professional solutions for companies. The SOCaaS, with system SIEM and UEBA, as well as CTI and
Keeping safety always on top is our job, if you want more information, don’t hesitate to contact us!
Useful links:

Tempo di lettura stimato: 7 minutes
Quando parliamo di “left of boom” o “right of boom” ci riferiamo ad un concetto che all’apparenza può sembrare superficiale. Invece, è un potente strumento che offre la possibilità di analizzare i conflitti di sicurezza sia da un punto di vista offensivo che da uno difensivo. In una ipotetica linea temporale di un attacco, ciò che si trova alla sua sinistra (left of boom) si riferisce a quello che accade prima. Analogamente, ciò che sta alla destra, è quello che avviene dopo.
Nel linguaggio comune molto spesso anziché “boom” si utilizza il termine “bang”, ma il significato resta comunque invariato. Si tratta, in sostanza, dell’evento stesso intorno al quale si analizza il periodo precedente e successivo.
Quindi, “left of boom” è l’insieme di eventi che si verificano prima dell’attacco. “Right of boom”, invece, è l’insieme di eventi che seguono il “boom”. Questa è la differenza sostanziale tra i due termini. Se le azioni difensive riescono a rilevare gli eventi nel periodo “left of boom”, è possibile trovare e adottare soluzioni per prevedere quando accadrà il “boom”.
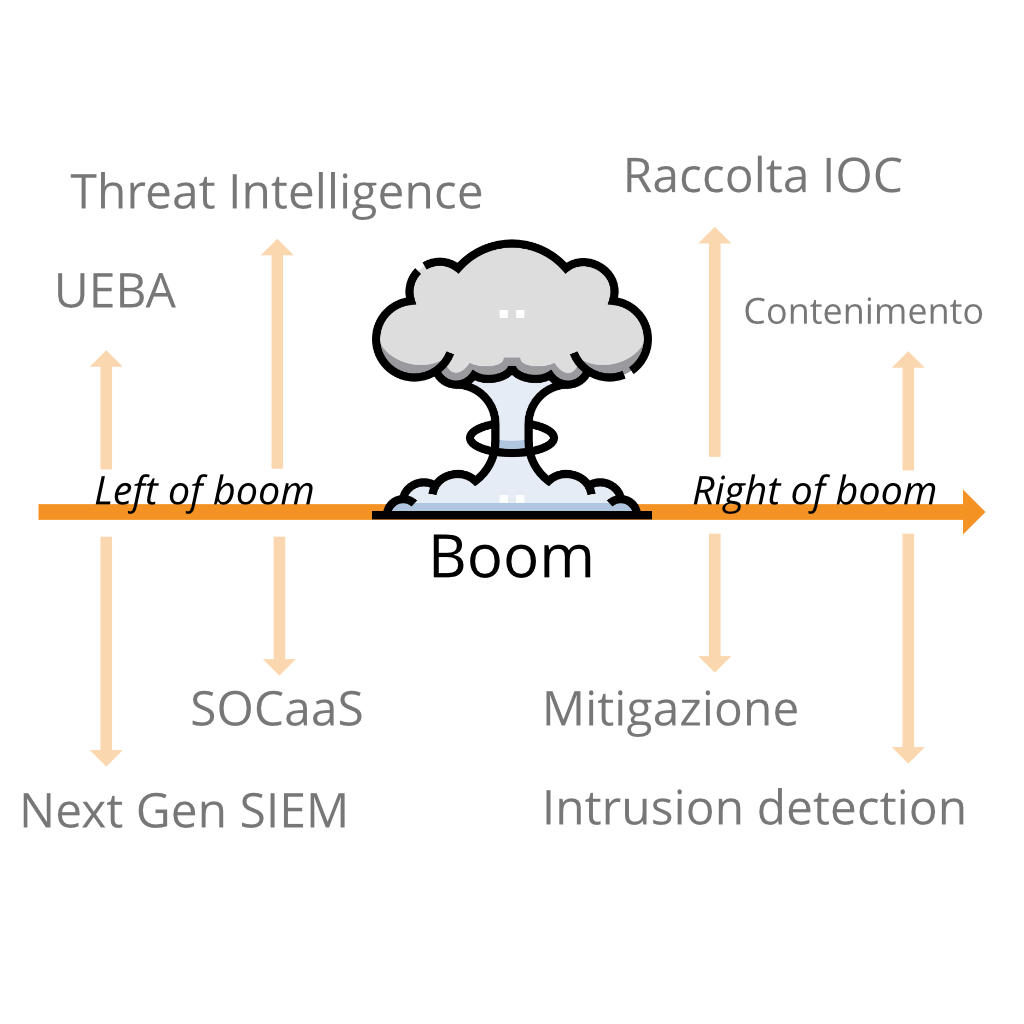
Per una persona inesperta nell’ambito della sicurezza informatica, questi concetti riguardanti la linea temporale di un attacco informatico potrebbero non essere nemmeno presi in considerazione, per questo motivo molte aziende preferiscono avvalersi di un SOCaaS.
Left of Boom
Un buon penetration tester riesce a rilevare alcuni eventi di tipo “left of boom”, ma spesso si tralascia la raccolta di informazioni sulle minacce. Certe volte non è in grado di distinguere tra loro concetti come “ingegneria della sicurezza, scoperta e risoluzione delle vulnerabilità” da un “controllo di prevenzione automatizzato”.
Non esiste in realtà un vero strumento valido di prevenzione, più che altro i controlli di sicurezza sono controlli di rilevamento. Alcuni di questi controlli integrano dei meccanismi di risposta automatizzati che impediscono il susseguirsi di spiacevoli eventi.
Un’applicazione web che previene attacchi di tipo XSS o SQLI è davvero utile per rilevare input non validi e risponde scartando il contenuto prima che l’iniezione possa verificarsi.
Un firewall progettato per bloccare le porte rileva semplicemente il traffico indesiderato in relazione al protocollo usato per la connessione e al numero della porta verso la quale si desidera accedere, interrompendo e reimpostando la richiesta di connessione.
Questi esempi si legano bene al concetto di “right of boom”. I controlli di prevenzione rilevano il “boom”, l’evento, e rispondono immediatamente arginando i possibili danni. “Left of boom” e “right of boom” sono così vicini nella linea temporale che sono difficilmente distinguibili, fino a quando non si esegue un’analisi accurata degli eventi.
Questo è uno dei motivi per cui i professionisti, nell’ambito della sicurezza informatica, amano i controlli di prevenzione. Lavorano rapidamente per correggere gli errori prima che gli hacker riescano a raggiungere i loro obbiettivi, limitando i danni.
Un SOCaaS in questi casi è una delle soluzioni migliori da adottare per proteggere l’integrità di un sistema informatico.
Right of Boom
Generalmente minore è la distanza tra “right of boom” e il tempo di risposta ad una minaccia, minori sono le conseguenze provocate da un eventuale attacco informatico. Ovviamente questa è solo una considerazione logica, non vale come regola assoluta.
Per alcune violazioni, la linea temporale tra l’evento e l’eliminazione completa della minaccia è discutibile, poiché il rilevamento è avvenuto dopo che l’hacker ha raggiunto il suo obbiettivo. Se gli hacker riescono ad infiltrarsi nel sistema ma vengono fermati in tempo, non arrecando nessun danno all’infrastruttura. In questo secondo caso, quindi, non c’è il “boom” di cui stiamo parlando.
Un esempio di right of boom
Per spiegare meglio il concetto di “right of boom” potremmo prendere come esempio un comune “malware”. I malware generalmente vengono sviluppati per attaccare in massa molti dispositivi, senza tanta discrezione. Con “right of boom” ci riferiamo a quel periodo di tempo che è passato da quando è avvenuta l’infezione da parte del malware.
Se hai letto gli altri articoli pubblicati da noi avrai appreso come gli hacker utilizzano queste tipologie di infezioni allo scopo di raccogliere informazioni sensibili, che vengono rivendute ad un terzo soggetto. Se il “right of boom” è più breve del tempo che l’hacker impiega per vendere queste informazioni, il danno può essere contenuto.
I migliori sistemi di sicurezza riescono ad accorciare il tempo “right of boom” riuscendo a raccogliere informazioni sugli attaccanti nel “left of boom”. Ci si può riuscire implementando delle contromisure in base al modello di minaccia. Questi strumenti permettono di scansionare intere infrastrutture, osservando i nuovi indicatori di minaccia giorni o addirittura settimane prima che gli attacchi si distribuiscano.
Come abbiamo visto anche in altri articoli, non sempre gli attacchi si svolgono in breve tempo. È, anzi, più probabile che gli hacker coinvolti agiscano in un primo, lento, periodo solo per raccogliere le informazioni necessario per sferrare l’attacco. Nel periodo “right of boom”, tornano utili strumenti come la cyber threat intelligence e un team di threat hunting.

Perché sono importanti i concetti “Right e Left of boom”
Se ci mettessimo nell’ottica dell’hacker, il concetto di “right of boom” e di “left of boom” può aiutare a decidere quale schema d’azione sia meglio intraprendere.
Supponiamo il caso in cui un hacker abbia a disposizione due metodi per potersi introdurre in un sistema informatico. Se uno dei due metodi potrebbe venire rilevato nel periodo “left of boom”, invece l’altro nel “right of boom”, è ovvio che l’hacker preferirà il secondo. Infatti, questo garantirebbe maggiori probabilità di successo dell’attacco.
Analogamente, tra due metodi che possono essere rilevati “right of boom” si sceglie quello che ha più possibilità di venir scoperto in ritardo. Più tempo passa dal boom alla rilevazione, maggiori sono le probabilità di successo. Questo tipo di ragionamento è importante per determinare quale tattica ha una linea temporale più ampia.
Ragionare in quest’ottica non è affatto semplice, richiede delle conoscenze avanzate da parte dell’esperto di sicurezza. Richiede inoltre il dover prendere in considerazione tutte quelle ipotesi che potrebbero potenzialmente determinare il successo dell’hacker.
Velocità
Un hacker è in grado di riuscire a prevedere se, utilizzando determinate tattiche, riuscirebbe a raggiungere l’obbiettivo più velocemente rispetto all’esperto che cerca di rilevare gli attacchi. Il “boom” è il primo contatto, nell’insieme delle tattiche d’intrusione utilizzate per accedere illegalmente ad un sistema informatico. Le rimanenti tattiche si collocano prima e dopo di esso.
Velocità e furtività solitamente si annullano a vicenda. Infatti, molto spesso si può essere più veloci sacrificando parte della furtività.
Velocità e furtività non vanno molto d’accordo quando parliamo di attacchi informatici. Essere furtivi, evitando di lasciare tracce, richiede più attenzione e quindi inevitabilmente anche più tempo. Tuttavia se lo scopo di un hacker non è un singolo obbiettivo ma una serie di più obbiettivi, l’essere veloci può rivelarsi efficace.
Per difendersi dagli attacchi, è possibile raccogliere gli indicatori di compromissione (IOC) per rimediare alle vulnerabilità presenti e per introdurre nuovi controlli di rilevamento, rendendo più sicuro il sistema informatico.
Conclusioni
È importante conoscere il concetto di linea temporale degli attacchi e abbiamo visto come i concetti di “left of boom” e “right of boom” influenzino i meccanismi di risposta alle minacce di intrusione.
I concetti che abbiamo visto in questo articolo, nonostante non aggiungano niente di concreto alle tecniche di difesa o di attacco di un sistema, offrono un punto di vista. Nella continua lotta tra hacker e operatori di sicurezza, avere una strategia vincente significa non solo disporre di strumenti efficienti, ma anche pianificare in modo dettagliato ogni dettaglio, prima e dopo gli attacchi.
Per sapere come un SOCaaS può aiutarti a monitorare l’infrastruttura aziendale e cogliere gli indizi “left of boom”, non esitare a contattarci, sapremo rispondere a ogni domanda e ti offriremo una soluzione per la tua azienda.
Useful links:

Tempo di lettura stimato: 5 minutes
In un altro articolo abbiamo già parlato della Cyber Threat Intelligence spiegando cos’è, come funziona e le sue varie tipologie. Oggi, invece, ci focalizzeremo più sull’importanza della Cyber Threat Intelligence, approfondendo come può essere utile alle aziende per fornire risposte in ambito di sicurezza, contenendo i rischi e fornendo informazioni che supportino la risposta agli incidenti.
L’importanza della Cyber Threat Intelligence
In un mondo in cui le tecnologie e le minacce informatiche sono sempre in continua evoluzione, un’azienda non può permettersi di trascurare l’importanza della Cyber Threat Intelligence. Ogni giorno sul web avvengono innumerevoli attacchi informatici e furti di dati a danno di aziende e privati. Queste grandi quantità di informazioni, vengono poi catalogate e vendute illegalmente sul Dark Web.
Gli hacker sono soliti vendere informazioni in questa parte del web perché garantisce loro l’anonimato. Infatti, a differenza del web tradizionale, per poter accedere a questi luoghi virtuali, bisogna utilizzare un browser che mascheri il proprio indirizzo IP. Questo complica le attività di tracciamento dei criminali da parte delle autorità e rende il dark web un posto completamente anonimo.
Uno degli obbiettivi che si pone la CTI è quello di monitorare le informazioni presenti in questa grande parte del web a scopo analitico. Il fine è quello di prevenire e arginare i danni che questi dati potrebbero provocare.
Monitorare il Dark Web e il Deep Web
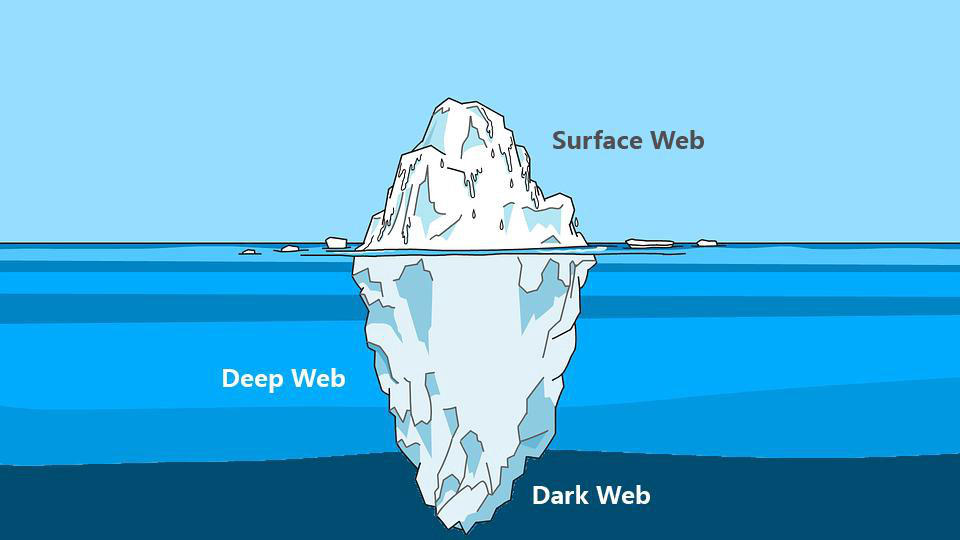
Spesso, quando parliamo di Deep Web e di Dark Web, pensiamo che siano presenti solo ed esclusivamente attività illegali, ma non è corretto. Ci sono anche forum, blog e siti web che hanno il fine di divulgare informazioni difficilmente reperibili sul web tradizionale.
Purtroppo però, è anche vero che i criminali sfruttano questa sezione della rete per vendere ogni genere di informazione. Queste comprendono numeri di telefono, indirizzi email, dati bancari, documenti, passaporti, credenziali d’accesso amministrative di siti web. C’è praticamente di tutto.
Questo genere di informazioni, nelle mani di un malintenzionato (o di un competitor), potrebbe compromettere l’integrità di un’intera azienda, dei suoi dipendenti e dei suoi clienti. Le conseguenze provocate da una violazione di dati, potrebbero inoltre manifestarsi anche sotto forma di danni alla reputazione dell’azienda.
Quando un cliente fornisce ad un’azienda i suoi dati personali si aspetta che vengano trattati con il massimo rispetto. I clienti potrebbero sentirsi “traditi” dall’azienda che avrebbe dovuto garantire loro la sicurezza delle proprie informazioni personali.
Un esempio clamoroso è stato il furto di dati avvenuto nel 2019 ai danni di Facebook Inc. (Fonte)
Ben 533 milioni di dati personali appartenenti agli utilizzatori della piattaforma sono stati sottratti, suddivisi per 106 paesi e diffusi gratuitamente sul web portando nuovamente la società al centro di polemiche.

Le aziende che cercano di proteggere i dati dei propri clienti, fornitori e dipendenti investono in strumenti di analisi e monitoraggio.
Affidandosi a dei professionisti, è possibile ricevere tempestivamente un avviso ogni qualvolta che un’informazione sensibile viene pubblicata su un forum o su un sito web presente nel Dark Web. Per questo l’importanza della Cyber Threat Intelligence gioca un ruolo chiave nel ramo della sicurezza informatica aziendale.
Monitorare il Dark Web dunque, significa avere la possibilità di poter rilevare tempestivamente eventuali informazioni sensibili prima che esse possano causare problemi alle aziende.

Strumenti per monitorare il Dark Web
Essendo una porzione di internet difficilmente accessibile e non indicizzata dai motori di ricerca, analizzare e monitorare le risorse presenti sul Deep Web diventa più complicato. Per questo motivo ci vengono in aiuto diversi strumenti progettati con lo scopo di semplificare il processo di indagine e analisi.
Un software che potrebbe essere d’aiuto durante un’attività d’investigazione è Onionscan, un programma Open Source completamente gratuito.
Il progetto Onionscan e la CTI
Il progetto Onionscan si pone due obiettivi:
– Aiutare gli operatori a trovare e risolvere problemi di sicurezza operativa
– Aiutare i ricercatori a monitorare e tracciare i siti presenti nel Deep Web
Il software è scaricabile sulla pagina Github dedicata, contenente anche una guida per l’installazione e una lista delle dipendenze necessarie per eseguire il software.
Una volta installato, per poterlo utilizzare basta semplicemente digitare nella riga di comando:
onionscan nomesitowebdascansionare.onion
Certamente, il solo accesso a uno strumento come questo non basta a fornire una copertura efficace. Infatti, l’importanza della Cyber Threat Intelligence risiede in gran parte nel saper effettuare le ricerche e interpretare i dati.
Conclusioni
Abbiamo visto cos’è e come funziona un’attività di monitoring del Dark Web e soprattutto abbiamo iniziato a comprendere l’importanza della Cyber Threat Intelligence.
Investire in queste soluzioni garantisce un’ulteriore sicurezza all’azienda. Mettere al sicuro i dati dei propri clienti e dei propri dipendenti non può essere un optional, ogni azienda dovrebbe essere sensibile a queste tematiche ed investire le proprie risorse per prevenire spiacevoli situazioni.
SOD offre un servizio apposito che si prefigge proprio di fornire informazioni di CTI preziose per la difesa proattiva e la risoluzione di criticità prima che diventino dei veri problemi.
Se hai bisogno di ulteriori chiarimenti non esitare a contattarci, siamo pronti a rispondere ad ogni tua domanda.
Useful links:

Estimated reading time: 5 minutes
Cyber Threat Hunting is a proactive security search across networks, endpoints and datasets to hunt down malicious, suspicious or risky activities that have escaped detection by existing tools.
Definition
There is a distinction between malware detection and cyber threat hunting . Threat detection is a passive approach to monitoring data and systems to identify potential security problems. However, it is a necessity and can help a threat hunter . Instead, proactive threat hunting tactics have evolved to use new threat intelligence on previously collected data to identify and classify potential risks before the attack .
Security personnel cannot afford to believe that their security system is impenetrable. Must always remain vigilant for the next threat or vulnerability . Rather than sitting around and waiting for threats to strike, cyber threat hunting develops hypotheses based on knowing the behaviors of threat actors and validating those hypotheses through active research in the environment .
With threat hunting, an expert doesn’t start with an alarm or indicators of compromise (IOC), but with deeper reasoning. In many cases the threat hunter’s efforts create and concretize the alarm or the IOC.
This aggressively assumes that a breach has occurred or will occur at the company. Security officers hunt down threats in their environment rather than rely on automatisms.

Threat hunting practice
For companies that are ready to take a more proactive approach to cybersecurity , which tries to stop attacks before they get too deep, adding threat hunting protocols to their security program is the next logical step.
After consolidating endpoint security and incident response strategies to mitigate the now unavoidable known malware attacks, companies can begin to take the offensive . This means digging deep and finding what hasn’t been detected yet. This is precisely the purpose of cyber threat hunting.
As mentioned earlier, threat hunting is an aggressive tactic that starts from the premise of the “assumption of violation”. Attackers are already inside an organization’s network and are secretly monitoring and moving into it.
This may sound far-fetched, but in reality, attackers can be inside a network for days, weeks, and even months . In the meantime, they prepare and execute attacks as advanced persistent threats, with no automatic defense detecting their presence . Cyber threat hunting stops these attacks by looking for covert indicators of compromise (IOCs) so they can be mitigated before the attacks reach their goals.

The key elements of a threat hunting
The goal of the threat hunt is to monitor daily activities and traffic across the network and investigate possible anomalies to find any undiscovered malicious activity that could lead to a complete breach . To achieve this level of proactive detection, threat hunting incorporates four equally important components.
1. Methodology
To be successful in hunt for threats, companies must commit to a proactive, full-time approach that is continuous and evolving. Instead, a responsive, ad hoc implementation, “ when we have time “, will be self-defeating and will only lead to minimal results.
2. Technology
Most companies already have comprehensive endpoint security solutions with automatic detection. Threat hunting works in addition to these and adds advanced technologies . The aim is to find anomalies, unusual patterns, and other traces of attackers that shouldn’t be in systems and files.
The new cloud-native endpoint protection (EPP) platforms that leverage big data analytics can capture and analyze large volumes of non-data filtered on endpoints, while behavioral analytics and artificial intelligence can provide broad, high-speed visibility into malicious behaviors that seem normal at first.
3. Highly qualified and dedicated staff
The threat hunters are a race of their own. These experts know how to use the security technology deployed by companies. In addition, also combine the aspiration to go on the offensive with intuitive problem-solving skills to uncover and mitigate hidden threats.
4. Threat intelligence
Having access to evidence-based global intelligence from experts from around the world (e.g. Miter Att & amp; ck ) further improves and accelerates hunting for existing threats. Hunters are aided by information such as attack classifications for identifying malware and threat groups , as well as advanced threat indicators.

The abilities of a threat hunter
The Threat Hunting Report from Crowd Research Partners confirms the importance of certain capabilities for threat hunting. When asked to rank the most important skill, the survey found that:
69% chose threat intelligence
57% chose behavior analysis
56% chose automatic detection
54% chose machine learning and automated analysis

The profile of a threat hunter
Threat hunters look for attackers who manage to break through vulnerabilities that a company might not even know exist . These attackers spend a considerable amount of time planning and performing the reconnaissance, acting only when they know they can successfully penetrate the network without warning. They also inject and build malware that has not yet been recognized or use techniques that do not rely on malware at all, to provide a persistent base from which to attack.
What does it take to outsmart even the smartest attackers?
A cyber threat hunter is relentless and can find even the smallest trace of what attackers have left behind. In general, threat hunters use their skills to undo the small changes that occur when attackers make their moves within a system or file.
The best threat hunters rely on their instincts to sniff out the stealth moves of the most dangerous attacker.
Are you a threat hunter? Contact us!
SOD is looking for a SOC / ICT analyst to add to the team. If you think you’re the right person, visit this page to view the detailed job posting.
Useful links:
Cyber Threat Intelligence (CTI) – greater effectiveness for IT security
Customers
Twitter FEED
Recent activity
-
SecureOnlineDesktop
Estimated reading time: 6 minutes L'impatto crescente delle minacce informatiche, su sistemi operativi privati op… https://t.co/FimxTS4o9G
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The growing impact of cyber threats, on private or corporate operating systems… https://t.co/y6G6RYA9n1
-
SecureOnlineDesktop
Tempo di lettura stimato: 6 minuti Today we are talking about the CTI update of our services. Data security is… https://t.co/YAZkn7iFqa
-
SecureOnlineDesktop
Estimated reading time: 6 minutes Il tema della sicurezza delle informazioni è di grande attualità in questo peri… https://t.co/tfve5Kzr09
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The issue of information security is very topical in this historical period ch… https://t.co/TP8gvdRcrF
Newsletter
{subscription_form_1}© 2023 Secure Online Desktop s.r.l. All Rights Reserved. Registered Office: via dell'Annunciata 27 – 20121 Milan (MI), Operational Office: via statuto 3 - 42121 Reggio Emilia (RE) – PEC [email protected] Tax code and VAT number 07485920966 – R.E.A. MI-1962358 Privacy Policy - ISO Certifications












