
Estimated reading time: 7 minutes
When we talk about log management we refer to a precise process which consists of the centralized collection of data that comes from different operating environments such as: devices, databases, applications and much more. Logs are produced by various system events , many of which are particularly important in the business environment.
So let’s see some important details regarding log management.

The importance of collection-in-log-management
The procedure for collecting log data is important to achieve various objectives at the company level. The main ones are: to verify the vulnerability; manage possible security problems; control access to data and applications; the monitoring in real time ; check for any malfunctions at the application level.
From a regulatory point of view, then, log management is very important at a company level as allows you to observe the most important principles concerning data protection . This is established by the “EU 95/46 / EC” directive. It is also required by the obligations established by the “ General Data Protection Regulation (RGPD or GDPR) “.
Hence, these features illustrate how important good log management is and how it can help companies prevent potentially invasive events before they occur.
This type of action corresponds to what, in jargon, is called “Privacy by Design”. According to this principle, it becomes necessary to execute the right strategies to avoid creating risks and problems related to violations.
The-problems-to-face-in-log-management
Log management needs the correct balance between the dynamic availability of resources and the growing number of log data . In addition, from the first step of acquiring the log data, it is appropriate to consider several elements. These often generate various complexities such as, for example: the quantity of sources to be taken into account; the number of data logs created; the multiplicity of events that give life to data log ; the types of data log ; the method of acquiring the data logs ; the compliance of the data log protection systems.
Log management needs the correct balance between the dynamic availability of resources and the growing number of log data . In addition, from the first step of acquiring the log data, it is appropriate to consider several elements. These often generate various complexities such as, for example: the quantity of sources to be taken into account; the number of data logs created; the multiplicity of events that give life to data log ; the types of data log ; the method of acquiring the data logs ; the compliance of the data log protection systems.
It is therefore advisable to plan the strategies that allow you to adopt the right solutions for your log management staff. In this way, technicians will be able to intervene while respecting the requirements already mentioned.
The characteristics of a log-management infrastructure
The infrastructure for log management is formed by the union of hardware, software and network elements that are set up so that they can communicate effectively with each other. The communications between these components are made within the same network that is used for the common activities of the company.
Nevertheless, for a company it is also important to take into account the possibility of collecting data using a different network so that any spyware attacks or other incidents will alter, intercept or delete the data.
If from the logistical and architectural point of view it is not possible, in a company, to carry out this second possibility, alternative measures should be adopted such as, for example, data encryption.
Summarizing, therefore, a log management infrastructure should ensure compliance with the following requirements: maintaining information that serves to achieve the collection objective following the principles of “minimization” and “proportionality” ; ensure that data remain unalterable throughout their life span; ensure the integrity of the data collected without making changes; keep the data for a limited period of time.
The data-aggregation at the company-level
As companies grow and reach large numbers of applications within their environment, data collection becomes an increasingly important and decisive challenge.
In addition, if we take into account the difficulty of collecting sufficient data logs to be able to remain compliant, respect for privacy standards and security issues that arise from modern threats, we easily realize how the collection becomes an increasingly complex challenge.
So, at the enterprise level, the key to creating an efficient collection system is the ability to dynamically capture data in real time from all available sources. Have a solution that allows you to put your data in a central location, such as a data lake , and facilitate filtering , transformation, classification, allows you to make the log management task easier for the company.
SOCaaS and the advanced log management system
A very advanced solution is the one offered by the SOCaaS , in particular by its component SIEM , which leverages the innovation of artificial intelligence. This allows you to analyze the data collected so as to find possible suspicious data.
In addition, a qualified technical intervention is always made available at any time of the day with precise and non-distracting tasks. The intervention allows you to verify the alarm notifications that are generated by the system so as to exclude false positives , intervening to eliminate the threat and give constant reports over time .
The ever increasing data collection and the analysis of artificial intelligence allow to make the service very convenient and complete.
The potential of the SOCaaS-system for companies
As we have just seen, it is very convenient for companies to rely on a SOC service (SOCaaS). The greatest potential is represented precisely by the innovation brought about by artificial intelligence that allows you to achieve maximum results regarding the constant and continuous analysis of data so that it has the certainty of identifying possible threats in a very short time . Thanks to this system, therefore, risks will be prevented and mitigated.
An added value, then, is not having to hire specialized technicians with specific skills in identifying and verifying threats. Those who rely on this service will also be able to receive reports on the situation and notifications in case of problems.
SOCaaS, therefore, allows you to take the right precautions against those still unknown techniques and has the ability to find the link between data concerning possible attacks with still unknown systems. This is thanks to the analysis of user behavior and infrastructure intities ( UEBA ).
In addition, the structure of the system is designed to bring about constant improvement. The synergistic work between technicians and artificial intelligence allows us to identify even unconventional breach attempts.
For companies it means improving their defenses by adapting them based on the data collected previously.
SOCaaS is perfect for those companies that want to work safely using network-based infrastructures. This is a guarantee of defense against cyber attacks .

The-advantages of choosing our SOCaaS for log-management
Choosing to rely on our SOCaaS has several benefits.
The first is to save money in both the short and long term. In fact, you will avoid buying dedicated hardware and specific software . Plus, you won’t even need to hire new employees or upgrade the skills of those who already work.
Another benefit is having the professional support of technicians who update every day to have the skills to fight new types of threats. This type of assistance is priceless and it is extremely difficult to obtain within the company staff. This is also due to the current shortage of professionals in the sector.
A further advantage is to have always updated technology available . You will not have to worry and worry about always updating the software, because these, solely responsible for the collection of data for SOCaaS, are always kept to the latest version.
Do you want to get more information to learn more about the SOCaaS functionality of SOD? Contact us to find out how we can help you keep your company’s defenses up.
Useful links:
IT systems produce large quantities of log files, very useful tools for guaranteeing data security and application stability. However, in a complex ecosystem, the quantity of files and their location can become two insurmountable obstacles to overcome, in case it is necessary to consult the data efficiently. This is where log management systems come into play, which thanks to technologies such as Syslog-ng, are able to circumvent the problem. In the article, we see how a log file management solution can be a valuable investment.
What is a log file, what is it for
Any action that is performed on a machine or by it can be recorded in a log file. To understand what it is, let’s imagine that it is a ship’s logbook, in which every single event that happened on the boat is noted. In fact, the name derives from the nautical environment, in which the use of a logbook was common. This was nothing more than a diary in which navigation data were recorded at regular intervals: speed, wind strength and direction, water conditions and so on.
With the concept of recording useful information in a file that can be consulted later, the log file contains any changes, actions, states or modifications for security reasons. In case something goes wrong, it is easy to understand what happened by consulting a log file. This is especially true when we talk about servers and applications, data dissemination, IT security, etc.
Amount of log files
Some companies have up to a few dozen servers, others have hundreds, some thousands, and there are others that manage tens of thousands of servers. These systems produce a huge amount of data in the form of log files.
Complicating things is IT architecture. Very often machines are organized into subsystems, both for reasons of convenience and safety. In the unfortunate event that someone wants to consult the log files following an accident, we should despair. Which server holds the data we are interested in? Which subsystem is it in? These are not questions that can be answered simply, especially if you don’t know the source of the problem.
The management of the log files of a system (or Log Management) is essential in the collection of data, prevention and resolution of problems.
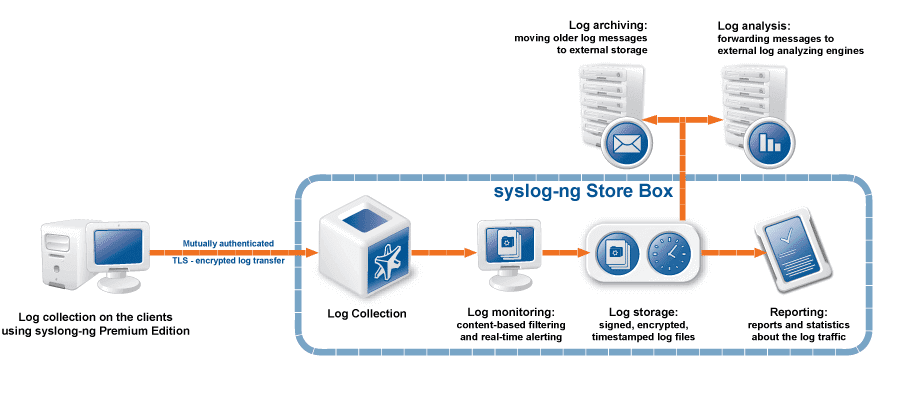
Secure Online Desktop Log Management
SOD offers a log management solution through Syslog-ng Premium Edition agents. These are in charge of the collection, transmission and storage of log files. Not only are they collected and centralized in a single virtual place, but the data are also normalized, ie “translated” into standardized formats so that they can be consulted and compared more easily.
Real-time normalization, reporting and classification
Thanks to normalization, it is possible to carry out cross-sectional full-text searches in a few seconds to all the log files collected. Complex operations are guaranteed by the possibility of using wildcards and Boolean operators. The analysis of the collected data is therefore very simplified, which allows the data to also be used to monitor the efficiency of the system, identify possible future problems and intervene before it is too late.
It is also possible to generate customized reports consisting of graphs and statistics with the aim of certifying compliance with standards and regulations such as PCI-DSS, ISO 27001, SOX and HIPAA.
One of the most interesting features of syslog-ng is the ability to automatically classify messages and sort them into classes. These can then be used to label the type of event described in the log. Examples of possible classes: user login, application crash, file transfer, etc.
Extraction and correlation of messages in log files
The classification of messages opens the door to a further functionality: the extraction and correlation of messages. Once each message contained in the log file has been normalized and classified according to your needs, it is possible to assign different tags, to add an additional filter level.
To give an example: once a user’s login messages have been collected, it is possible to label them as user_login, and then isolate them by extracting them and collecting them in a separate file to perform further processing on these messages.
Syslog-ng also makes it possible to correlate events in real time, to prevent data from a single event being scattered across multiple log files. For example, the access and exit data (log-in and log-out) are often recorded far from each other, even in different log files. Through correlation, the data of a single event can be collected and analyzed in isolation.
Automatic backup
The stored log messages and the configuration of the Log Management service can be periodically transferred to a remote server using the following protocols:
– Network File System protocol (NFS)
– Rsync over SSH
– Server Message Block protocol (SMB / CIFS)
Performance
The log file collection and management system with syslog-ng PE agents operates on over 50 platforms, including all Linux distributions and commercial versions of Unix and Windows. The service is able to manage huge quantities of messages, up to over 100,000 per second and over 70 GB of raw log files per hour, from 5000 different sources (servers, applications, etc.).
Ask us for more information about our Log Monitoring service to know specifically how it can be implemented in your systems and how it can help you.
[btnsx id=”2931″]
Useful links:
New service | Log Management – High performance service for collecting logs
syslog server – High performance service for collecting logs
-
- Use all the strengths of the syslog-ng Premium Edition
- Find logs, secure sensitive data with granular access policies and generate reports
- Forward logs to third-party tools
SYSLOG SERVER – CLOUD LOG MANAGEMENT SERVICE TO MANAGE YOUR LOGS
Log Management service allows you to keep logs (applications, system, audit logs, query databases, etc) in the Secure Online Desktop Cloud secure from any tampering with respect to data retention rules.
COLLECT AND INDEX LOG DATA IN CLOUD
Log Management service uses the syslog-ng Premium Edition as log collection agents which provide highly scalable and reliable log collection. Installers are available for 50+ platforms, including the most popular Linux distributions, commercial versions of UNIX and Windows.
The indexing engine is optimized for performance. Depending on its exact configuration, one syslog-ng Store Box can collect and index up to 100,000 messages per second for sustained periods. A single Log Management instance can collect log messages from more than 5,000 log sources. When deployed in a client-relay configuration, a single Log Collector can collect logs from tens of thousands of log sources
SEARCH, TROUBLESHOOT, AND REPORT
With full-text search, you can search through billions of logs in seconds via the intuitive web-based user interface. Wildcards and Boolean operators allow you to perform complex searches and drill down on the results. Users can gain a quick overview and pinpoint problems. Users can easily create customized reports from the charts and statistics they create on the search interface to demonstrate compliance with standards and regulations such as PCI-DSS, ISO 27001, SOX and HIPAA.
HIGHLY SCALABLE INDEXING ENGINE
The Log Management service is optimized for performance, and can handle enormous amounts of messages. Depending on its exact configuration, it can index over 100,000 messages per second for sustained periods and process over 70 GB of raw logs per hour.
syslog server – REAL-TIME LOG DATA TRANSFORMATION
Filter, Parse, Re-Write
The syslog-ng application can sort the incoming log messages based on their content and various parameters like the source host, application, and priority. Directories, files, and database tables can be created dynamically using macros. Complex filtering using regular expressions and boolean operators offers almost unlimited flexibility to forward only the important log messages to the selected destinations
Parse key-value pairs
Log Aggregator can separate a message consisting of whitespace or comma-separated key-value pairs (for example firewall logs) into name-value pairs.
Parse sudo log messages
Privileged user accounts represent the highest security risk, as they allow access to the most sensitive data and resources. The sudo parser enables you to enrich your log message data with details of privilege escalation events.
Normalize data with PatternDB
The syslog-ng application can compare the contents of the log messages to a database of predefined message patterns.
Real-time log message classification
By comparing log messages to known patterns, syslog-ng is able to identify the exact type of the messages, and sort them into message classes. The message classes can be used to classify the type of the event described in the log message. The message classes can be customized, and, for example, can label the messages as user login, application crash, file transfer, etc.
Extracting important information from messages
In addition to classifying messages, you can also add different tags which can be used later for filtering messages, for example, to collect messages tagged as user_login to a separate file or to perform conditional post processing on the tagged messages.
Real-time event correlation
Syslog-ng also makes real-time event correlation possible. This can be useful in many different situations. For example, important data for a single event is often scattered into multiple syslog messages. Also, login and logout events are often logged far away from each other, even in different log files, making log analysis difficult. Using correlation these can be collected into a single new message.
syslog server – AUTOMATED BACKUP OF STORED DATA
Stored log messages and the configuration of SSB can be periodically transferred to a remote server using the following protocols
:
– Network File System protocol (NFS);
– Rsync over SSH;
– Server Message Block protocol (SMB/CIFS).
Customers
Twitter FEED
Recent activity
-
SecureOnlineDesktop
Estimated reading time: 6 minutes L'impatto crescente delle minacce informatiche, su sistemi operativi privati op… https://t.co/FimxTS4o9G
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The growing impact of cyber threats, on private or corporate operating systems… https://t.co/y6G6RYA9n1
-
SecureOnlineDesktop
Tempo di lettura stimato: 6 minuti Today we are talking about the CTI update of our services. Data security is… https://t.co/YAZkn7iFqa
-
SecureOnlineDesktop
Estimated reading time: 6 minutes Il tema della sicurezza delle informazioni è di grande attualità in questo peri… https://t.co/tfve5Kzr09
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The issue of information security is very topical in this historical period ch… https://t.co/TP8gvdRcrF
Newsletter
{subscription_form_1}© 2023 Secure Online Desktop s.r.l. All Rights Reserved. Registered Office: via dell'Annunciata 27 – 20121 Milan (MI), Operational Office: via statuto 3 - 42121 Reggio Emilia (RE) – PEC [email protected] Tax code and VAT number 07485920966 – R.E.A. MI-1962358 Privacy Policy - ISO Certifications












