Estimated reading time: 6 minutes
The issue of information security is very topical in this historical period characterized by digitization. To protect themselves, businesses and individuals can use a variety of tools that can prevent an attack, but also help manage it. In this article we talk about Automated Response Integration and the automations in the SOCaaS offered by SOD .
Although the systems used are almost always based on efficient technologies, in recent years the implementation of SOCaaS services equipped with SNYPR for the analysis of Big Data is making a difference. The dedicated SOCaaS services facilitate end users in the use of security systems, basing their operation on automatic processes that protect company devices.

What is Automated Response Integration
The term Automated Response Integration identifies a specific approach to data analysis and consequent response in a cyber defense scenario. We see it today, in particular, related to our SOCaaS on which the SNYPR tool is applied, which we have already talked about in the past.
SNYPR and Automated Response Integration
In order to understand the potential of a SOCaaS service, with the implementation of SNYPR, it is appropriate to understand first what is meant by this term. When the word SNYPR is used, it identifies that examination tool capable of analyzing Big Data and simplifying its actions . A system equipped with SNYPR can examine a huge amount of data and identify the behaviors of everyone who interacts with the platform.
There is the combination of SIEM and UEBA logs, as well as an analysis dedicated to security in real time, very useful for automating the daily operations carried out in the infrastructure.
The operation of a SNYPR tool for corporate IT is based on the analysis of thousands of information collected, thanks to artificial intelligence. These analyzes are then used to prevent and intervene on cyber threats. The fact that most of these operations are automatic brings us to the field of Automated Response Integration.
Technically it differs from other platforms in the use of threat detection algorithms that have the ability to scan systems and logins performed by other devices in real time . A traditional system simply collects data, while a SOCaaS with SNYPR implementation can also detect much more harmful threats and adapt accordingly.
The strengths of Automated Response Integration with SNYPR / SOCaaS
One of the strengths of this tool is its Security Data Lake (SDL) based security system. This condition allows companies to keep a copy of the data in the SDL and submit the scan request at any time. There is no data lock, as in traditional systems, but an open system capable of sharing information with the different devices.
As it is easy to guess, it is precisely this availability of data and the possibility of in-depth analysis, which allows us to implement an Automated Response Integration strategy with our SOCaaS.
There are various system functions in the field that are noteworthy. These include: data enrichment, distributed behavioral analysis, historical investigation, scalability and data redundancy.
This coordination of services allows to have a concrete impact for IT security , a condition evident in three areas of SNYPR competence: internal threats, persistent threats and professional use.
The professional use of SNYPR: in recent years, the most important companies have equipped themselves with a SNYPR platform to protect their data storage and analysis infrastructures. The system constantly monitors the flow of information and adapts to the best conditions in the event of cyber attacks.
Automated Response Integration for automation in SOCaaS
From a technical point of view, a SNYPR system itself guarantees excellent potential, but it is with the SOCaaS implementation that it finds its maximum protection expression in IT systems.
The analysis of threats in a company system, although it is carried out in real time, requires the intervention of specialized technicians to identify the problem. With SOCaaS, identification is linked to automated actions to deal with possible threats, without the need for third-party intervention.
There is a real integration with automated response useful to prevent and eradicate possible threats . This process is essential not only to prevent business systems from being compromised, but also to protect companies and their IT departments, which can focus on other tasks.
Automated Response Integration functionality
Playbook: the tool can launch a playbook when SNYPR threats are detected. The transcript of the events is important to understand the origin of the threat.
Query: automation can manage actions or queries on end points directly from SNYPR, in order to face the cyber attack. This feature avoids the blocking of production in the most excited moments.
UEBA: As mentioned in the previous lines, an NSYPR-based tool can import UEBA alerts. The reference formats are usually CEF, which report warnings from any type of device, significantly affecting safety.
IP control : one of the strengths of this technology is the control of domains, IPs, files and URLs, ensuring maximum versatility for any type of work activity.
DNS and Whols data : The automated response is particularly useful in storing DNS and Whols data, as it is possible to check the validity of certificates and monitor unwanted access.
Vulnerability: You can schedule a network vulnerability scan. This analysis process is especially suitable for companies that send and receive a large flow of information outside the company context.

Relying on professionals
Not all SOCaaS-based services that implement SNYPR are identical to each other, some of them offer the same technology but different intervention methods. Among the most interesting solutions is our SOCaaS. For years we have been dealing with offering IT security solutions internationally and this is a guarantee of excellence, alongside our certifications and partnerships.
Our IT security service, based on Automated Response Integration, guarantees complete monitoring of corporate infrastructures, helping the company to avoid additional costs for ordinary or extraordinary maintenance of the devices.
Conclusions
The implementation of SOCaaS automated systems is now essential for companies that want to protect themselves from IT docking. Real-time analysis and notification of potential threats ensure essential peace of mind in an age increasingly exposed to digital dangers.
To find out how SOD and its services can help your company, do not hesitate to contact us, we will be happy to answer any questions.
Useful links:

Estimated reading time: 4 minutes
When we refer to artificial intelligence, we often refer to the great technologies that could control the world, with an obvious streak of science fiction. The reality is very different and is characterized by a technology with great potential, which is able to ensure countless advantages . Today we talk about how artificial intelligence can be implemented in monitoring.
The use of these technologies is unavoidably transversal to many sectors of the economy, but it is also usable in some aspects of everyday life. Some examples range from washing machines that, weighing the load of laundry, are able to choose the most advantageous washing program, to voice assistants that simplify our everyday life.
Very important in the corporate sector are the monitoring systems which were created precisely from these technologies which we will talk more about in a moment.
Thanks to the optimization of the computing capacity operated by artificial intelligence, it is possible to increase the efficiency of company equipment. Let’s see how.

What is artificial intelligence and how can it innovate monitoring ?
Today, artificial intelligence is declined in many ways. Perhaps the most important is processing a large amount of data then providing answers to complex questions. At the base of artificial intelligence there is the study of algorithms that deal with performing complex mathematical operations.
Artificial intelligence is a very useful tool within a company, as it is able to carry out very sophisticated and precise processing. These operations are capable of significantly improving the operations and productivity of numerous departments of the company itself.
Applied to monitoring, for example, artificial intelligence is capable of analyzing the logs coming from the network, both in terms of performance and behavior. The big step forward in the analysis and monitoring of an infrastructure consists precisely in recognizing whether certain behaviors that emerge from the logs are risky or not.
To achieve these results it is essential to have all those features that are available through artificial intelligence .
What are the advantages of using artificial intelligence for monitoring?
Artificial intelligence is able to provide companies that choose to use it countless advantages. Not only in terms of improving the performance of information systems, but also to make more efficient and improve the security of the same, preventing attacks.
This happens thanks to the analysis of the logs both from a technical and a behavioral point of view. Technical analysis highlights any ongoing problems, while behavioral analysis can prevent or immediately identify suspicious actions.
How can our monitoring system improve business efficiency?
Our monitoring system is able to improve business efficiency through numerous technical analyzes in able to be implemented not only on the entire system, but also on individual units.
The ability to analyze data in depth also allows you to improve the management of the entire IT structure and prevent overloads or attacks. Overall, the efficiency and safety of the infrastructure are increased at the same time through artificial intelligence applied to monitoring.
But there’s more: these analysis and monitoring systems are able to integrate with extreme effectiveness in complex architectures. By being able to analyze large amounts of data and being able to deduce behaviors and actions from these, efficiency in security is ensured.
Another advantage is the fact that this monitoring system does not require specific hardware. Software agents are installed on the systems to be controlled which have the sole task of sending data in the form of a log to the control system. analyses.
These systems therefore prove to be the ideal solution to keep large and small IT architectures under control, with the aim of improving efficiency and increasing overall security. In short, an application really interesting and useful of artificial intelligence in monitoring.

What are the fields of application of this technology?
We apply artificial intelligence systems to monitoring, benefiting our customers enormously. First we can collect large amounts of data, enrich it automatically and finally analyze it. The analyzes are carried out both from a technical and a behavioral point of view.
The result is a dedicated system, our SOCaaS, which makes risk mitigation extremely efficient, particularly quick intervention in the event of an anomaly and also provides regular reports.
This service is able to bring together all the features listed in the article, and to offer it as a solution for companies that want a superior security system.
Better efficiency, safety, versatility, operability, are just some of the paradigms used to define the services we make available to our customers. Our main goal is to simplify and make your company’s IT security more efficient.
Do not hesitate to contact us if you want to know more, we will be happy to answer any questions.
Useful links:

Estimated reading time: 6 minutes
Out of nowhere, someone replies to an email conversation dated months ago. This is a real conversation that actually happened. Maybe it’s about a meeting, a job opportunity. This email seems very relevant, but beware, it could be zombie phishing .
Indeed, something is wrong, the topic discussed has been over for months and now there is a strange error message in the body of the email. This is a sneaky tactic: revive a long dead email conversation.

Not the usual phishing
The Cofense ™ Phishing Defense Center ™ (PDC) spotted a large Zombie Phishing campaign in 2018. The scam , like almost any phishing attack, is carried out through compromised email accounts.
Scammers take over an email account and respond to long-closed conversations with a phishing link or malicious attachment (e.g. malware or a keylogger ) . Since the email subject is usually relevant to the victim, a curiosity-driven click is very likely to occur . In fact, let’s not forget that the original conversation was already present in the messages received, it is easy to think that it is a follow up or similar.
These Zombie Phishing attacks appear to use automatically generated infection URLs to evade detection. No two links are alike, and they are hidden behind “error” messages without too many frills in the body of the message. This scenario provides a pattern of apparent legitimacy for the users who are victims.
The zombies in computer science
In the computer industry, a zombie is a compromised computer connected to the network. The compromised state could be due to a hacker, virus, malware, or trojan horse .
The infected machine performs malicious tasks under a remote direction. Zombie computer botnets are often used to spread email spam and launch denial-of-service (DoS) attacks.
Types of attack
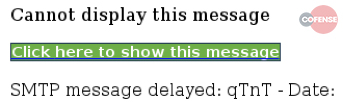
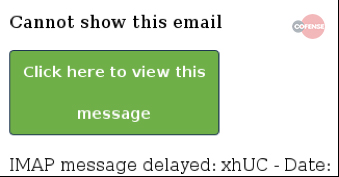
Here are some observed patterns of Zombie Phishing carrying malicious links . A distinguishing factor was the use of two distinct graphic templates containing button or link error messages.
The message reads something like “Incomplete message” or “Inability to show the whole message”. The link or button invites you to click to see the original message. Obviously the click only involves the installation of a malware or other similar events . Note that no two identical links have been identified, a sign that probably a bot was generating the addresses.
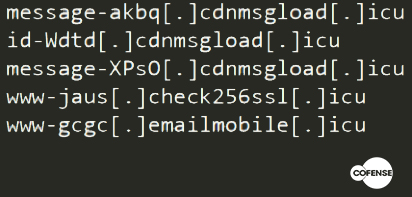
Another common factor is the use of domains with the .icu TLD. This is probably a factor that varies considerably over time. Here are some of the domains found in the first analysis of 2018:
These zombie phish attacks have been observed to use official organizational logos to add legitimacy to the fake login pages. A common practice in phishing techniques that we have already seen in other articles.
Landing pages are designed to look like a legitimate online portal, including a company logo and even a favicon. In these cases the ultimate goal is the theft of the victim’s credentials .
Furthermore, any victim who visits the malicious website is “tagged” using the host’s IP address as an identifier and, after entering the credentials, is directed to the same spam website seen by other victims. This is often done via obfuscated links using URL shorteners (such as hxxps://href[.]Li/).
If the same host tries to visit the phishing link again, the fake login page is skipped and you are forwarded directly to the spam page. This markup and URL shortener obfuscation helps attackers keep a low profile and continue their campaign unabated.
Conversation Hijacking

The conversation hijacking tactic is by no means new and is now living a new life with zombie phishing . Scammers have hijacked compromised email accounts to distribute malware and phishing emails as replies to conversations that have been concluded for years now.
This technique is still popular because it makes victims much more likely to click on links and download or open files. The threshold of attention against classic phishing attacks is lowered when messages are brought into conversations already in their inbox .
A couple of years old example of this was the botnet Geodo . Basically it is insertion into existing email threads ( conversation hijacking ) to deliver malicious documents. These, in turn, download a sample of Geodo or other malware such as Ursnif , which according to Key4Biz was the most widespread in Italy in June 2020.
However, the effectiveness of this tactic can greatly depend on the content of the conversations . A reply to an automated advertising email is less likely to cause an infection than a reply to a help-desk support thread.
There have been several Geodo zombie phishing campaigns consisting of replies to automated advertising emails. This is an indication that, in some cases, campaigns consist of indiscriminate replies to all emails in a mailbox. Since the volume of these conversation hijacking is still relatively low, the small reach of these emails is probably limited by the number of ongoing conversations .
Certain account types are therefore more likely to attract the direct attention of threat actors and induce them to invest additional effort and time in developing unique phishing campaigns for those accounts.
Defense from zombie-phishing
Here are some quick tips to avoid losing your credentials in a Zombie Phishing attack:
- Beware of email subjects that may seem relevant but come from old conversations
- Beware of any error message in the body of the message
- Don’t trust attached documents just because they’re replying to a conversation
- Hover your mouse over buttons or links in suspicious messages to check for suspicious domains
It has been observed that these campaigns have gotten smarter . To combat this and other forms of phishing, employee training is key.
A properly trained workforce is what it takes to defend your organization against Zombie Phishing attacks.
SOD offers a full service in this regard . We begin by attacking the company in a controlled manner, testing any weaknesses in employee safety or behavior. Subsequently, specific training is designed to remedy the gaps and fully train the staff.
To keep defenses high, our SOCaaS includes the analysis of user behavior, logs of connected machines and the network in a to immediately identify phishing attempts.
Useful links:

Estimated reading time: 10 minutes
Social engineering is the term used for a wide range of malicious activities performed through human interactions. It uses psychological manipulation to trick users into making security mistakes or provide sensitive information. Then, with that information, the hacker is able to successfully carry out targeted attacks, such as data theft, a ransomware or a ‘ interruption of services.
Social engineering attacks usually occur in stages . The perpetrator first investigates the intended victim to gather the necessary background information , such as potential entry points and weak security protocols, required to proceed with the attack. Then, the attacker moves to gain the victim’s trust and provide incentives for subsequent actions that violate security practices, such as disclosing sensitive information or granting access to critical resources.
What makes social engineering particularly dangerous is that it relies on human error rather than vulnerabilities in software and operating systems . Mistakes made by legitimate users are much less predictable, making them more difficult to identify and thwart than a malware-based intrusion.

Note that the target of a social engineer is not necessarily a network or software . Being able to enter a building evading security, and then installing a device or stealing documents, are actions that still fall under this type of attack.
The techniques of social engineering
Social engineering attacks come in many different forms and can be carried out wherever human interaction is involved . The following are five most common methods of digital social engineering attacks.
Baiting (from “bait”)
As the name suggests, baiting attacks use a false promise (a decoy , indeed) to whet the victim’s greed or curiosity. They lure users into a trap that steals their personal information or installs malware on their systems.
The most infamous form of baiting uses physical media to disperse malware . For example, attackers leave the bait (typically infected keys) in conspicuous areas where potential victims are certain to see them (e.g. bathrooms, elevators, the parking lot of a targeted company). The decoy has a legitimate look, like a label indicating the content, like the company’s payroll. The clue that reveals what it should contain may change, of course, but has the potential to be potentially very interesting .
Victims pick up the bait out of curiosity and insert it into a work or home computer, resulting in automatic installation of malware on the system.
Lure scams don’t necessarily have to be done in the physical world. Forms of online baiting consist of enticing advertisements leading to malicious sites or encouraging users to download a malware-infected application. Here it leads to the phishing techniques, which we will see shortly.
Defense notes : to defend against these social engineering attacks, as well as paying close attention to what is connected to your computer, it does not hurt to have an efficient antivirus and anti-malware system. For the company, a new generation SIEM system and UEBA help in detect suspicious user behavior and greatly reduce the risk of malware infection.

Scareware (from “to scare”)
Scareware consists of bombarding victims with false alarms and fake threats . Users are tricked into thinking their system is infected with malware, prompting them to install software that has no real benefit (other than the perpetrator) or is malware itself. Scareware is also called deception software ( deception software ), rogue scanner software and fraudware .
A common example of scareware is the legitimate-looking popup banner that appears in your browser as you browse the web , displaying text such as “ Your computer may be infected with spyware programs harmful “. In other cases, the popup offers to install the tool (often infected with malware) for you, or directs you to a malicious site where your computer is infected.
Scareware is also distributed via spam email which distributes bogus warnings, or offers users to buy useless / harmful services. Social engineering is often very imaginative and manages to find ever new ways to deceive. Always be alert.
Defense notes : In case you suspect that the received message is really legitimate, it is best to seek a solution actively , i.e. without using the links suggested by the message same. For example, we received a message from a service announcing that our account has been compromised. If in doubt, you can contact the support of the service directly from their site to ask for clarification. Avoid using the links suggested by the suspicious message at all costs .

Pretexting (from “to pretend”)
In this social engineering attack, an attacker gains information through a series of cleverly constructed lies . The scam is often initiated by an perpetrator who pretends to need sensitive information from a victim in order to perform a critical task.
The attacker usually begins by establishing trust with his victim by impersonating colleagues, police, bank and tax officials, or others who have a right to know authority . The hacker asks questions that are apparently necessary to confirm the victim’s identity, through which he collects important personal data.

Many types of information are collected using this technique, such as identity card numbers, personal addresses and telephone numbers, telephone records, staff vacation dates, bank records, and even security information relating to a physical facility.
Any information, however harmless it may seem, could later be used for a second attack. Even the name of a security guard hired by the company could already be enough to build trust and ask for a tear to the rule when asking for the access code to automatic doors.
Phishing (from “to fish”)
As one of the most popular types of social engineering attacks, phishing scams are email and text message campaigns that aim to create a sense of urgency , curiosity or fear in the victims . Then it prompts them to reveal sensitive information, click links to malicious websites, or open attachments that contain malware.
An example is an email sent to users of an online service notifying them of a policy violation that requires immediate action on their part, such as a mandatory password change. Includes a link to a website, nearly identical in appearance to its legitimate version, which prompts the user to enter their current credentials and new password . After submitting the form, the information is sent to the attacker.
Since identical, or nearly identical, messages are sent to all users in phishing campaigns, detecting and blocking them is much easier for mail servers that have access to threat-sharing platforms.
Defense note : While it is true that in some cases we have become accustomed to not giving weight to these kinds of messages, it is also true that social engineers have become increasingly clever. There is no need to let your guard down. Instead, it is very useful to always be wary of messages that require credentials.
These attacks leverage the fact that it’s easy to fool some users, whether out of distraction or naivety. The best defense is employee training through a ethical phishing service and subsequent targeted training.

Spear phishing (from “spear, and “to fish”)
This is a more targeted version of phishing in which an attacker chooses specific individuals or businesses . They then tailor their messages based on their victims’ characteristics, job positions, and contacts to make their attack less obvious. Spear phishing requires a lot more effort from the author and can take weeks and months to complete. They are much harder to detect and have better success rates when done skillfully.
A spear phishing scenario could involve an attacker who, impersonating an organization’s IT consultant, sends an email to one or more employees. It is worded and signed exactly as the consultant normally does, thus fooling recipients into thinking it is an authentic message. The message prompts recipients to change their password and provides them with a link that redirects them to a malicious page where the attacker now captures their credentials.

How to defend against social engineering attacks
Social engineers manipulate human feelings, such as curiosity or fear, to carry out patterns and lure victims into their traps. Therefore, it is essential to be cautious whenever you feel alarmed by an email, attracted to an offer displayed on a website, or when you come across digital media wandering around. Being alert can help protect you from most social engineering attacks that happen online.
Additionally, the following tips can help you improve your vigilance in relation to social engineering attacks.
- Do not open emails and attachments from suspicious sources . If you don’t know the sender in question, you don’t need to reply to an email. Even if you know them and are suspicious of their message, cross-check and confirm the news from other sources , such as over the phone or directly from a service provider’s website. Even an email that appears to come from a trusted source may have been initiated by an attacker.
- Use multi-factor authentication . One of the most valuable pieces of information attackers look for is your user credentials . Using 2-factor authentication helps ensure the protection of your account in case of system compromise. There are free applications for all types of mobile devices that allow you to implement this type of authentication.
- Be wary of attractive offers . If an offer seems too tempting , think twice before accepting it as real. Use Google to check the topic and quickly determine if you are dealing with a legitimate offer or a trap.
- Update your antivirus / antimalware software . Make sure automatic updates are turned on. Check periodically that updates have been applied and scan your system for possible infections.
If your company has an IT department, these recommendations should be standard security measures.

Security services for companies
When you think about the data that your company holds and manages, you are never too cautious in defense. Social engineering relies on the fact that an employee hacks more easily than a computer , which is often true.
In addition to the cyber protection measures listed above, it is good that all employees are aware of the risks and potential threats.
SOD offers a series of services that go in this direction. The first and perhaps most important is ethical phishing in which we try to attack the company with phishing techniques . We find out what the weak points are and organize internal training to provide the right tools for staff.
We also have the classic Vulnerability Assessment and Penetration Test for testing cybersecurity systems. Addons are applicable to this service to cover a greater number of areas. There is a specific addon for app analysis and code review , but also one where we try to hack the company with physical attacks . We will test the physical security of the company, the ability to enter buildings, access to network controllers and more.
Finally, to keep networks under control, the SOCaaS service allows you to monitor the entire network, identify suspicious actions (with behavior analysis via artificial intelligence), unauthorized installations, breach attempts and much more.
Data security in the company is really important, contact us to find out how we can help you!
Useful links:

Estimated reading time: 5 minutes
A Zero-Day attack (also known as 0-day) exploits a software vulnerability unknown to security officers and the software vendor. Hackers can exploit the weakness, as long as it is not mitigated, through Zero-Day exploit or, indeed, attack.
The term “zero-day” originally referred to the number of days after the software was released. A “zero-day” software, therefore, meant a program obtained by forcing a developer’s computer before release. The term was then applied to the vulnerabilities that this practice allows to exploit. Once the vendor becomes aware of the vulnerability, they usually patch or recommend solutions to mitigate it.
Software vulnerabilities
Software often has vulnerabilities. These are unintentional flaws, or code problems that could hypothetically be exploited.For example, there may be a flaw that allows a cybercriminal to access otherwise secure data. Programmers are often on the lookout for these vulnerabilities and when they discover them, they analyze them, produce a patch to fix them, then distribute that patch in a new version of the software.
However, this is a time-consuming process. When the flaw becomes known, hackers around the world can start trying to exploit it.
Zero-Day Attack
If a hacker manages to exploit the vulnerability before the developers find a solution, this exploit then becomes known as a Zero-Day attack.
Zero-day vulnerabilities can take almost any form, because they can manifest themselves as any type of vulnerability in software. For example, they can take the form of missing data encryption, SQL injection, buffer overflows, missing permissions, bugs, or problems with password security.
This makes these vulnerabilities difficult to find before they are exploited in zero-day attacks. This, in some ways, is good news: it also means that hackers will have a hard time finding them. But also that it is difficult to defend against these vulnerabilities effectively.
How to protect yourself
We have seen how difficult it is to protect yourself from the possibility of a zero-day attack, because it can take many forms. Almost any type of security vulnerability could be exploited as a zero-day if a patch is not produced in time. Also, many software developers intentionally try not to disclose the vulnerability publicly in the hope that they can distribute a patch before any hacker discovers the vulnerability.
There are a few strategies that can help you defend your business against zero day attacks:
Stay informed on Zero-Day attacks
Zero-day exploits aren’t always advertised, but occasionally we hear about a vulnerability that could potentially be exploited. If you stay tuned to the news and pay attention to releases from your software vendors, you may have time to put security measures in place or respond to a threat before it is exploited. A good way to do this is to follow your suppliers’ newsletters. At the bottom of this page you will find the form to subscribe to the SOD one.
Keep your systems up to date
Developers are constantly working to keep their software up to date and secure to prevent the possibility of exploits.When a vulnerability is discovered, it is only a matter of time before they produce a patch. However, it is up to you and your team to make sure your software platforms are always up to date. The best approach in this case is to enable automatic updates, so that the software is updated routinely, and without the need for manual intervention.
Use additional security measures
Make sure you’re using security solutions that protect you from a zero-day attack. SOD offers a solution that includes a set of tools that allow you to raise your defenses significantly. SOCaaS is a real security operations center for your company. Using state-of-the-art tools such as SIEM and UEBA and thanks to granular control over the monitored network, every attack attempt is identified in the shortest possible time.
Each type of data produced by the interconnected systems in the infrastructure is collected, normalized and analyzed for anomalies. This means that not only are you checking for known indicators of compromise (IOC), but suspicious operations and behavior of facility users are also monitored. In this way, it is also possible to identify attack attempts that are normally very difficult to detect, such as those involving Zero-Day Attacks, but not only. In fact, through the SOCaaS service, it is possible to identify compromised accounts, the violation of protected data, lateral movement attacks, phishing, etc.
The security of a company’s IT system is a very important topic that we care a lot about. The compromise or loss of sensitive data can cost a lot from both an economic and a reputational point of view. Do not neglect this important aspect for the safety of your business, contact us to tell us about your situation, we will be happy to show you how we can help you.
Useful links:
Vulnerability Assessment and Penetration test
Protecting a site in WordPress: security package
Long-term search: what’s new in the SOCaaS service
Contact us
Customers
Twitter FEED
Recent activity
-
SecureOnlineDesktop
Estimated reading time: 6 minutes L'impatto crescente delle minacce informatiche, su sistemi operativi privati op… https://t.co/FimxTS4o9G
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The growing impact of cyber threats, on private or corporate operating systems… https://t.co/y6G6RYA9n1
-
SecureOnlineDesktop
Tempo di lettura stimato: 6 minuti Today we are talking about the CTI update of our services. Data security is… https://t.co/YAZkn7iFqa
-
SecureOnlineDesktop
Estimated reading time: 6 minutes Il tema della sicurezza delle informazioni è di grande attualità in questo peri… https://t.co/tfve5Kzr09
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The issue of information security is very topical in this historical period ch… https://t.co/TP8gvdRcrF
Newsletter
{subscription_form_1}© 2023 Secure Online Desktop s.r.l. All Rights Reserved. Registered Office: via dell'Annunciata 27 – 20121 Milan (MI), Operational Office: via statuto 3 - 42121 Reggio Emilia (RE) – PEC [email protected] Tax code and VAT number 07485920966 – R.E.A. MI-1962358 Privacy Policy - ISO Certifications