 Giacomo Lanzi
Giacomo Lanzi
Zabbix: Web console for monitoring
An indispensable tool for keeping complex infrastructure controlled is a monitoring system. Secure Online Desktop (SOD) Web Console does just that: it offers the tools to control a network of machines and devices to verify its efficiency. Web Console is based on Zabbix, a scalable Open Source platform with huge capabilities.
Among the advantages of the SOD Web Console, there are the possibility of using agent less under some circumstances the great possibility of customization. The platform offered allows scripting in various languages, including Python, Perl or directly in the shell, just to give examples.
Monitoring with Web Console and Zabbix
To collect data from the infrastructure, it is necessary to install so-called software agents for the machines to be monitored. These software use native processes and free from the need to have dedicated environments such as Java or .Net.
The data collected by the agents are sent to a server that collects all the metrics and provides them to the console. From here it is then possible to analyze them, manipulate them and set triggers of notifications or automations useful for management.
When communicating between the components of the Zabbix monitoring system, only authorized IPs are accepted. Since the other connections are not accepted, security is guaranteed during data transfers between the software.
Web Console functionality
Every aspect of the infrastructure can be monitored through the Web Console offered by SOD. Even if it is not possible to install additional software, there is a limited control action without agents installed. This solution allows you to collect metrics on the responsiveness and availability of standard services, such as mail or web servers.
Scalability of data collection
The Zabbix system offered by the SOD Web Console is able to recover data and metrics from any device or software. Through the use of different control protocols, the available software agents are able to collect any type of data.
Monitoring supported
Through the Zabbix agents used, the data collected is complete and includes both hardware and software metrics.
For example, metrics from infrastructure network hardware are collected by SNMP agents. An optimal solution for network capacity management and planning. The measurements include the use of memory, CPU, RAM and the status of the logical ports of the controlled peripherals.
The controls include more levels of system complexity. Agents can collect information from:
– Hardware (CPU, fans, storage media, etc.)
– Network (ports used, memory usage, etc.)
– Operating systems (Unix, Windows, MacOs, etc.)
– Middleware software (Oracle, MySql, Apache, etc.)
– Web applications
– Cloud resources
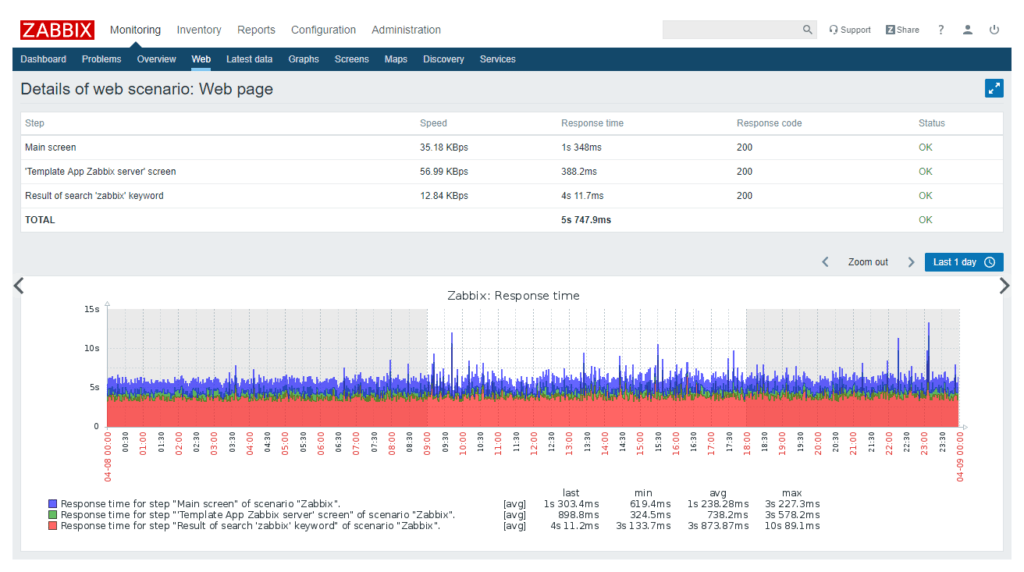
Monitoring web services
The built-in system for monitoring web services is worthy of specific mention.
Through the use of this function, it is possible to define the sequential steps to be performed for the analysis of a website. It is possible to monitor the site response speed and downloads, for example. But also availability, as well as data relating to e-commerce portals and other web based applications.
Scalability ‘
SOD Web Console is scalable and adaptable to the size of the infrastructure. From the small corporate IT network, to even very complex solutions from thousands of machines and devices. A single installation can support up to 3,000,000 checks per minute, collecting gigabytes of data per day.
Furthermore, through the use of proxy software components, it is possible to distribute the data collection and decentralize the calculation operations. In this way the control of ports and connections is more easily managed.
You can organize your network into sections where metrics are collected and calculated independently. The proxy in charge of the calculation will be the only connection outgoing from the subsystem.
Notifications and triggers
An efficient monitoring strategy provides not only the collection of data, but also a system for which any anomaly is reported in order to be able to intervene promptly.
The SOD Web Console implements a customizable system of triggers and notifications to be always informed in case something is not going as it should.
Ideally, once the first data is collected, the thresholds of values considered “normal” are established. On the basis of these, a notification system is customized which immediately communicates the exceeding of a safety threshold of certain parameters.
The management of metrics is thus very lightened by an automatic verification of their values. When a parameter presents an anomalous value, one would be immediately informed.
The notification methods supported are: email, SMS, Jabber or through other methods customizable through scripting.
How to request and install Web Console
It is possible to request SOD Web Console after a first initial meeting with our network architect. On that occasion, the computer perimeters of the network to be monitored and what the alarm notification modes are defined.
After this first step, our team will take care of installing all the software needed to collect metrics on the systems involved. Once these operations are completed, the system will be ready and accessible from a console in the cloud. The access data are provided only after the installation of the entire control system.
From the Web Console you will be able to check all monitored metrics, check performance and manage notifications.
Download the brochure or try a demo of the Web Console.
[btnsx id=”2931″]
Useful links:
How to have your computer network under control
Customers
Twitter FEED
Recent activity
-
SecureOnlineDesktop
Estimated reading time: 6 minutes L'impatto crescente delle minacce informatiche, su sistemi operativi privati op… https://t.co/FimxTS4o9G
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The growing impact of cyber threats, on private or corporate operating systems… https://t.co/y6G6RYA9n1
-
SecureOnlineDesktop
Tempo di lettura stimato: 6 minuti Today we are talking about the CTI update of our services. Data security is… https://t.co/YAZkn7iFqa
-
SecureOnlineDesktop
Estimated reading time: 6 minutes Il tema della sicurezza delle informazioni è di grande attualità in questo peri… https://t.co/tfve5Kzr09
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The issue of information security is very topical in this historical period ch… https://t.co/TP8gvdRcrF
Newsletter
{subscription_form_1}© 2023 Secure Online Desktop s.r.l. All Rights Reserved. Registered Office: via dell'Annunciata 27 – 20121 Milan (MI), Operational Office: via statuto 3 - 42121 Reggio Emilia (RE) – PEC [email protected] Tax code and VAT number 07485920966 – R.E.A. MI-1962358 Privacy Policy - ISO Certifications