SOCaaS [EDR]: AUTONOMOUS BREACH PROTECTION
Home » SOCaaS [EDR]: AUTONOMOUS BREACH PROTECTION
SOC as a Service [EDR]
The solution to unify and automate security
SOCaaS [EDR] is the service that relieves your company of all the management of impending threats.
A 360° active-passive service that includes:
- Monitoring
- Analysis and control
- Attack prevention and detection
- Constant calibration based on events
- Updates on all new threats
How does it work

Agents
Software agents are installed on all Endpoints.
Configuration
They are customized according to the characteristics of the infrastructure.
Activation
The agents are activated and begin their work of collecting and alerting.

Passive action
Agents block known threats and enrich logs.
Active action
The most important threats generate an alert to our staff who actively intervene to solve the problem.
Security assured
In conclusion, the best passive-active conclusion to really protect your network.
What is a SOC
A SOC, acronym for Security Operations Center, is a team of experts dedicated to protecting organizations from cyber attacks.
Imagine SOC as a symbiosis of
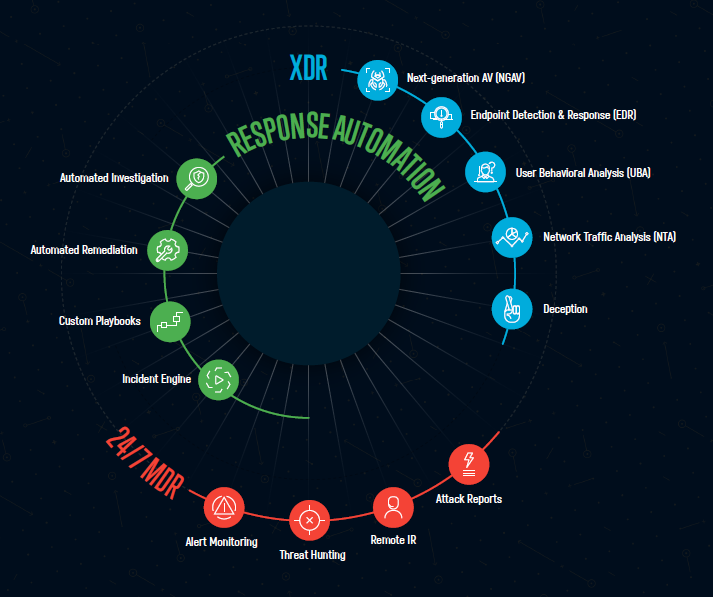

What SOCaaS can do for your business
Our “SOC as a Service” system integrates different methods of intervention to reduce threats.
The combination of technical implementations and real people creates a security system that improves over time and that will adapt to the types of threats your business can face.
The main features
Detection and patching of missing security updates is performed on a regular basis and significantly reduces the risk exposure of off-the-shelf exploits
Ideal for a closed and deterministic environment. Any change in status of known threat-free files is immediately brought to the attention of the operator by an alert.
Granular visibility and reporting of all outgoing entities – hosts, installed software, etc. – are central to various IT security and management needs.
Keeping logs for an unlimited period of time allows organizations to comply with various regulatory requirements
Instant view of threat activity status
across the entire environment: file, network, users, and hosts.


SOC as Service [NGS]
SOC as Service [NGS] is the sibling of the [EDR] solution.
A Security Operations Center (SOC) with Endpoint Detection and Response (EDR) focuses on protecting endpoints, such as computers and mobile devices, using behavior-based threat detection techniques. Instead, a SOC with Next-Generation Security (NGS) focuses on analyzing real-time data from a variety of sources, including endpoints, networks and applications, to identify threats and respond to them faster. In summary, an EDR SOC is more specific while an NGS SOC is broader and more integrated.
The union between the two systems makes it possible to achieve a level of security that was unthinkable until recently, with the effectiveness of up-to-date technical measures and a real and competent staff.
The steps in detecting a problem
SOAR (Security Orchestration, Automation and Response) che mettiamo in pratica è rappresentato dai passaggi illustrati e schematizzati qui sotto. There are several systems and technologies put into practice, including the aforementioned SDL and UEBA, which make up the SOC. But those are just the machine part of the SOAR.
To these is added the staff made up of ethical hackers who constantly verify the data that could identify a cyber threat, intervening, if necessary, to block the breach.
Collection of log files

Analyzing data from agents

Anomaly detection

Manual actions

Possible problem

Customer Notification

Certifications and safety
Secure Online Desktop is an ISO 27001 certified company, which for our customers means that we provide guaranteed IT security services.
We particularly care about the cyber security of our customers, the efficiency of the resources used and the competence of our employees.
Your company data is important!
The entire architecture of the service resides in the cloud.
Your job: install an agent.
We’ll take care of the rest!
Send us a message for more information
We are available to answer your questions and evaluate your situation together to offer you the best services.
Customers
Twitter FEED
Recent activity
-
SecureOnlineDesktop
Estimated reading time: 6 minutes L'impatto crescente delle minacce informatiche, su sistemi operativi privati op… https://t.co/FimxTS4o9G
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The growing impact of cyber threats, on private or corporate operating systems… https://t.co/y6G6RYA9n1
-
SecureOnlineDesktop
Tempo di lettura stimato: 6 minuti Today we are talking about the CTI update of our services. Data security is… https://t.co/YAZkn7iFqa
-
SecureOnlineDesktop
Estimated reading time: 6 minutes Il tema della sicurezza delle informazioni è di grande attualità in questo peri… https://t.co/tfve5Kzr09
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The issue of information security is very topical in this historical period ch… https://t.co/TP8gvdRcrF
Newsletter
{subscription_form_1}Products and Solutions
News
- NIS: what it is and how it protects cybersecurity April 22, 2024
- Advanced persistent threats (APTs): what they are and how to defend yourself April 17, 2024
- Penetration Testing and MFA: A Dual Strategy to Maximize Security April 15, 2024
- Penetration Testing: Where to Strike to Protect Your IT Network March 25, 2024
- Ransomware: a plague that brings companies and institutions to their knees. Should you pay the ransom? Here is the answer. March 6, 2024
Google Reviews

Ottima azienda, servizi molto utili, staff qualificato e competente. Raccomandata!read more
Ottimo supportoread more
E' un piacere poter collaborare con realtà di questo tiporead more
Un ottimo fornitore.
Io personalmente ho parlato con l' Ing. Venuti, valore aggiunto indubbiamente.read more

© 2023 Secure Online Desktop s.r.l. All Rights Reserved. Registered Office: via dell'Annunciata 27 – 20121 Milan (MI), Operational Office: via statuto 3 - 42121 Reggio Emilia (RE) – PEC [email protected] Tax code and VAT number 07485920966 – R.E.A. MI-1962358 Privacy Policy - ISO Certifications










