
Il NIST Cybersecurity Framework è un insieme di linee guida sviluppato per ridurre i rischi legati alla sicurezza informatica. Elenca delle attività specifiche associate alla gestione del rischio di sicurezza informatica basandosi su standard e linee guida già esistenti. È uno dei più popolari framework dedicati alla sicurezza informatica ed è impiegato in modo diffuso perché fornisce un aiuto sotto l’aspetto della gestione del rischio.
Redatto dal National Institute of Standards and Technology (NIST), questo quadro di cybersecurity affronta la mancanza di standard quando si tratta di cybersecurity. Infatti, fornisce un insieme uniforme di regole, linee guida e standard per le organizzazioni da utilizzare nei vari settori. Il NIST Cybersecurity Framework (a volte abbreviato NIST CSF) è ampiamente considerato come il gold-standard per costruire un programma di cybersecurity.
Sia che tu abbia appena iniziato a stabilire un programma di cybersecurity o che tu stia già eseguendo un programma abbastanza maturo, il framework può fornire valore aggiunto. Agisce come uno strumento di gestione della sicurezza di alto livello che aiuta a valutare il rischio di cybersecurity in tutta l’organizzazione.

La struttura del NIST Cybersecurity Framework
Il NIST Cybersecurity Framework è strutturato principalmente in tre parti:
Core: contiene una serie di attività, risultati e riferimenti su aspetti e approcci legati alla sicurezza informatica.
Implementation Tiers: è un sistema di classificazione che aiuta le organizzazioni a fare chiarezza sugli aspetti dedicati alla gestione del rischio di sicurezza informatica.
Profile: in sostanza è l’elenco dei risultati che un’organizzazione ha scelto, in base alle proprie necessità, dalle categorie e sotto-categorie della struttura.
Funzioni e categorie delle attività di cybersecurity
Il Core del NIST possiamo dividerlo in 5 sezioni, che a loro volta sono suddivise in 23 categorie. Per ogni categoria si definisce una serie di sotto-categorie, per un totale complessivo di 108 sotto-categorie. Ogni sotto-categoria, fornisce delle Risorse informative che fanno riferimento a sezioni specifiche di altri standard di sicurezza, come ISO 27001, COBIT, NIST SP 800-53, ANSI/ISA e CCS CSC.
La complessità di questo framework, ha dato origine alla creazione di progetti di legge che guidano il NIST a creare delle linee guida facilmente accessibili alle piccole e alle medie imprese.
Sezioni del NIST Cybersecurity Framework
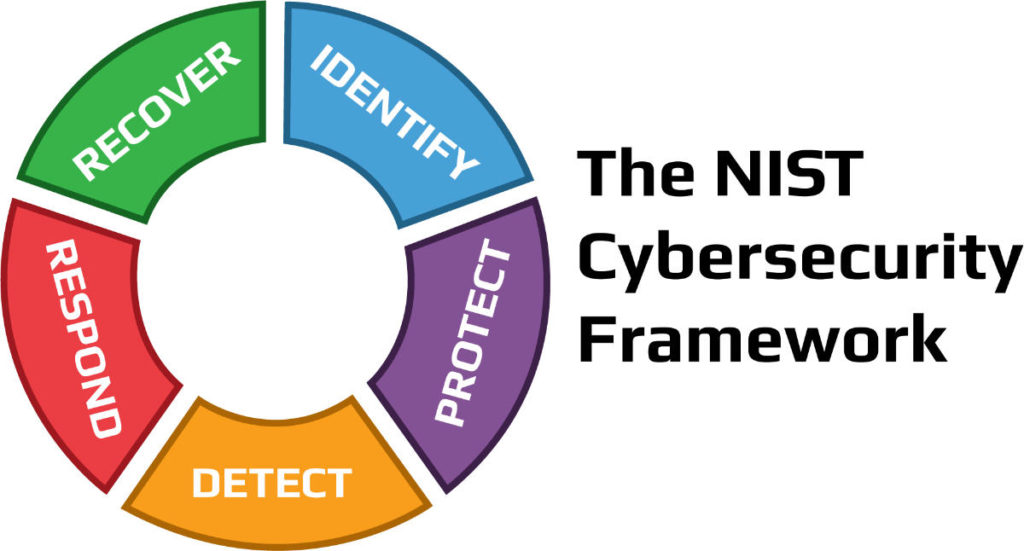
Identificazione (Identify)
La funzione di identificazione si concentra sul porre le basi per un efficace programma di cybersecurity. Questa funzione assiste nello sviluppo di una comprensione organizzativa per gestire il rischio di cybersecurity per sistemi, persone, beni, dati e capacità. Per consentire a un’organizzazione di concentrare e dare priorità ai suoi sforzi, coerentemente con la sua strategia di gestione del rischio e le esigenze di business, questa funzione ha sottolineato l’importanza di comprendere il contesto di business, le risorse che supportano le funzioni critiche, e i relativi rischi di cybersecurity.
Le attività essenziali in questa sezione del NIST includono:
Individuare le risorse fisiche e software per stabilire la base di un programma di gestione delle risorse
Definire l’ambiente di business dell’organizzazione, compreso il suo ruolo nella catena di fornitura
Scegliere le politiche di cybersecurity stabilite per definire il programma di governance e identificare i requisiti legali e normativi relativi alle capacità di cybersecurity dell’organizzazione
Identificare le vulnerabilità degli asset, le minacce alle risorse organizzative interne ed esterne e le attività di risposta al rischio per valutare il rischio
Stabilire una strategia di gestione del rischio, compresa l’identificazione della tolleranza al rischio
Produrre una strategia di gestione del rischio della catena di fornitura, comprese le priorità, i vincoli, le tolleranze di rischio e le ipotesi usate per sostenere le decisioni di rischio associate alla gestione dei rischi della catena di fornitura
Protezione (Protect)
La funzione di protezione del NIST delinea salvaguardie appropriate per garantire la fornitura di servizi di infrastrutture critiche. Inoltre, supporta la capacità di limitare o contenere l’impatto di un potenziale evento di cybersecurity.
Le attività critiche in questo gruppo includono:
Implementare le protezioni per la gestione delle identità e il controllo degli accessi all’interno dell’organizzazione, compreso l’accesso fisico e remoto
Responsabilizzare il personale attraverso la formazione sulla consapevolezza della sicurezza, compresa la formazione degli utenti privilegiati e basata sui ruoli
Stabilire una protezione della sicurezza dei dati coerente con la strategia di rischio dell’organizzazione per proteggere la riservatezza, l’integrità e la disponibilità delle informazioni
Implementare processi e procedure per mantenere e gestire le protezioni dei sistemi informativi e delle risorse
Proteggere le risorse organizzative attraverso la manutenzione, comprese le attività di manutenzione a distanza
Gestire la tecnologia per garantire la sicurezza e la resilienza dei sistemi, coerentemente con le politiche, le procedure e gli accordi organizzativi
Rilevamenti (Detect)
Rilevare potenziali incidenti di cybersecurity è fondamentale e questa funzione del Framework definisce le attività appropriate per identificare il verificarsi di un evento di cybersecurity in modo tempestivo. Le attività in questa funzione includono:
Garantire il rilevamento di anomalie ed eventi e la comprensione del loro potenziale impatto
Implementare capacità di monitoraggio continuo per monitorare gli eventi di cybersecurity e verificare l’efficacia delle misure di protezione, comprese le attività di rete e fisiche
Risposte (Respond)
La funzione di risposta del NIST si concentra sulle attività appropriate per agire in caso di un incidente di cybersecurity rilevato e supporta la capacità di contenere l’impatto di un potenziale incidente di cybersecurity.
Le attività essenziali per questa funzione includono:
Garantire l’esecuzione del processo di pianificazione della risposta durante e dopo un incidente
Gestire le comunicazioni con gli stakeholder interni ed esterni durante e dopo un Analizzare l’incidente per Garantire una risposta efficace e sostenere le attività di recupero, compresa l’analisi forense e la determinazione dell’impatto degli incidenti
Eseguire attività di mitigazione per prevenire l’espansione di un evento e per risolvere l’incidente
Implementare miglioramenti incorporando le lezioni apprese dalle attività di rilevamento/risposta attuali e precedenti
Recupero (Recover)
La funzione recupero del framework identifica le attività appropriate per rinnovare e mantenere i piani di resilienza e per ripristinare qualsiasi capacità o servizio che sia stato compromesso a causa di un incidente di cybersecurity. Il recupero tempestivo alle normali operazioni è importante per ridurre l’impatto di un incidente.
Le attività essenziali per questa funzione si sovrappongono in qualche modo a quelle di risposta e includono:
Assicurare che l’organizzazione implementi processi e procedure di pianificazione del recupero per ripristinare i sistemi e/o gli asset colpiti da incidenti di cybersecurity
Implementare miglioramenti basati sulle lezioni apprese e sulle revisioni delle strategie esistenti
Le comunicazioni interne ed esterne sono coordinate durante e dopo il recupero da un incidente di cybersecurity
Come iniziare con il NIST Cybersecurity Framework
Allinearsi con il framework significa enumerare tutte le vostre attività ed etichettare questi elementi con una di queste 5 etichette di funzione. Per esempio, l’etichetta Identify sarà per gli strumenti che vi aiutano a inventariare le vostre risorse. Strumenti come Firewall andranno in Protect. Tuttavia, a seconda delle loro capacità, li potreste voler mettere anche in Detect insieme ai vostri SIEM. Gli strumenti di risposta agli incidenti e i playbook vanno in Respond. I vostri strumenti di backup e ripristino fanno parte di Recover.
Una volta che avete fatto questo esercizio, alcune delle sezioni potrebbero sembrare più vuote di altre e potreste sentirvi a disagio per la descrizione della funzione corrispondente.
Questo è un bene, perché ora potete articolare ciò che manca al vostro programma di cybersecurity.
Conclusioni
In questo articolo abbiamo compreso cos’è il NIST Cybersecurity Framework e come è strutturato analizzando alcune delle sue sezioni principali e degli elementi che compongono queste sezioni.
Tuttavia, il nostro consiglio è quello di rivolgervi a un provider SaaS che vi possa fornire gli strumenti per implementare il NIST in modo efficiente senza alcun rischio. Le nostre soluzioni SaaS possono aiutare in questo senso e invitiamo a contattarci per sapere come i nostri servizi possono aiutare la tua azienda in ambito di sicurezza informatica.
Non esitare a contattarci per saperne di più, risponderemo a ogni vostra domanda.
Useful links:

Tempo di lettura stimato: 5 minutes
In un altro articolo abbiamo già parlato della Cyber Threat Intelligence spiegando cos’è, come funziona e le sue varie tipologie. Oggi, invece, ci focalizzeremo più sull’importanza della Cyber Threat Intelligence, approfondendo come può essere utile alle aziende per fornire risposte in ambito di sicurezza, contenendo i rischi e fornendo informazioni che supportino la risposta agli incidenti.
L’importanza della Cyber Threat Intelligence
In un mondo in cui le tecnologie e le minacce informatiche sono sempre in continua evoluzione, un’azienda non può permettersi di trascurare l’importanza della Cyber Threat Intelligence. Ogni giorno sul web avvengono innumerevoli attacchi informatici e furti di dati a danno di aziende e privati. Queste grandi quantità di informazioni, vengono poi catalogate e vendute illegalmente sul Dark Web.
Gli hacker sono soliti vendere informazioni in questa parte del web perché garantisce loro l’anonimato. Infatti, a differenza del web tradizionale, per poter accedere a questi luoghi virtuali, bisogna utilizzare un browser che mascheri il proprio indirizzo IP. Questo complica le attività di tracciamento dei criminali da parte delle autorità e rende il dark web un posto completamente anonimo.
Uno degli obbiettivi che si pone la CTI è quello di monitorare le informazioni presenti in questa grande parte del web a scopo analitico. Il fine è quello di prevenire e arginare i danni che questi dati potrebbero provocare.
Monitorare il Dark Web e il Deep Web
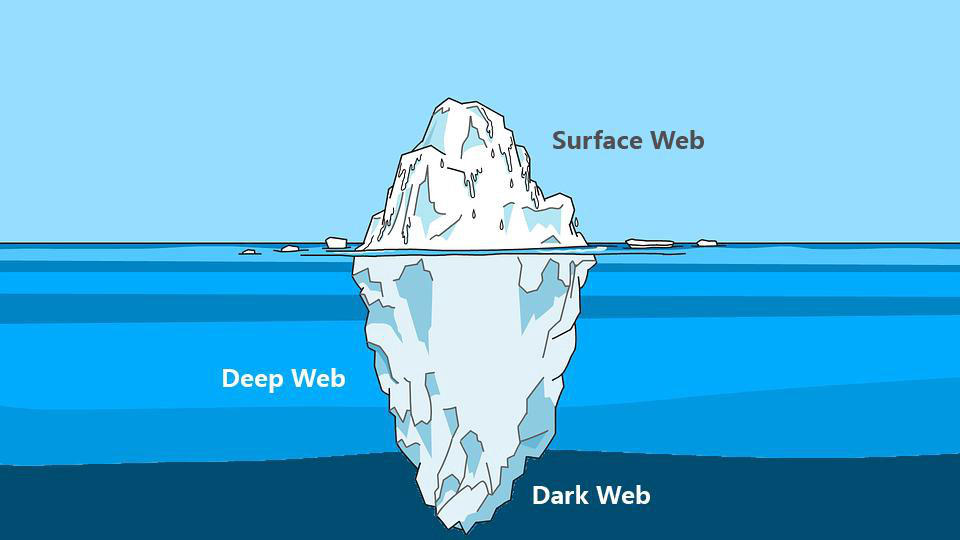
Spesso, quando parliamo di Deep Web e di Dark Web, pensiamo che siano presenti solo ed esclusivamente attività illegali, ma non è corretto. Ci sono anche forum, blog e siti web che hanno il fine di divulgare informazioni difficilmente reperibili sul web tradizionale.
Purtroppo però, è anche vero che i criminali sfruttano questa sezione della rete per vendere ogni genere di informazione. Queste comprendono numeri di telefono, indirizzi email, dati bancari, documenti, passaporti, credenziali d’accesso amministrative di siti web. C’è praticamente di tutto.
Questo genere di informazioni, nelle mani di un malintenzionato (o di un competitor), potrebbe compromettere l’integrità di un’intera azienda, dei suoi dipendenti e dei suoi clienti. Le conseguenze provocate da una violazione di dati, potrebbero inoltre manifestarsi anche sotto forma di danni alla reputazione dell’azienda.
Quando un cliente fornisce ad un’azienda i suoi dati personali si aspetta che vengano trattati con il massimo rispetto. I clienti potrebbero sentirsi “traditi” dall’azienda che avrebbe dovuto garantire loro la sicurezza delle proprie informazioni personali.
Un esempio clamoroso è stato il furto di dati avvenuto nel 2019 ai danni di Facebook Inc. (Fonte)
Ben 533 milioni di dati personali appartenenti agli utilizzatori della piattaforma sono stati sottratti, suddivisi per 106 paesi e diffusi gratuitamente sul web portando nuovamente la società al centro di polemiche.

Le aziende che cercano di proteggere i dati dei propri clienti, fornitori e dipendenti investono in strumenti di analisi e monitoraggio.
Affidandosi a dei professionisti, è possibile ricevere tempestivamente un avviso ogni qualvolta che un’informazione sensibile viene pubblicata su un forum o su un sito web presente nel Dark Web. Per questo l’importanza della Cyber Threat Intelligence gioca un ruolo chiave nel ramo della sicurezza informatica aziendale.
Monitorare il Dark Web dunque, significa avere la possibilità di poter rilevare tempestivamente eventuali informazioni sensibili prima che esse possano causare problemi alle aziende.

Strumenti per monitorare il Dark Web
Essendo una porzione di internet difficilmente accessibile e non indicizzata dai motori di ricerca, analizzare e monitorare le risorse presenti sul Deep Web diventa più complicato. Per questo motivo ci vengono in aiuto diversi strumenti progettati con lo scopo di semplificare il processo di indagine e analisi.
Un software che potrebbe essere d’aiuto durante un’attività d’investigazione è Onionscan, un programma Open Source completamente gratuito.
Il progetto Onionscan e la CTI
Il progetto Onionscan si pone due obiettivi:
– Aiutare gli operatori a trovare e risolvere problemi di sicurezza operativa
– Aiutare i ricercatori a monitorare e tracciare i siti presenti nel Deep Web
Il software è scaricabile sulla pagina Github dedicata, contenente anche una guida per l’installazione e una lista delle dipendenze necessarie per eseguire il software.
Una volta installato, per poterlo utilizzare basta semplicemente digitare nella riga di comando:
onionscan nomesitowebdascansionare.onion
Certamente, il solo accesso a uno strumento come questo non basta a fornire una copertura efficace. Infatti, l’importanza della Cyber Threat Intelligence risiede in gran parte nel saper effettuare le ricerche e interpretare i dati.
Conclusioni
Abbiamo visto cos’è e come funziona un’attività di monitoring del Dark Web e soprattutto abbiamo iniziato a comprendere l’importanza della Cyber Threat Intelligence.
Investire in queste soluzioni garantisce un’ulteriore sicurezza all’azienda. Mettere al sicuro i dati dei propri clienti e dei propri dipendenti non può essere un optional, ogni azienda dovrebbe essere sensibile a queste tematiche ed investire le proprie risorse per prevenire spiacevoli situazioni.
SOD offre un servizio apposito che si prefigge proprio di fornire informazioni di CTI preziose per la difesa proattiva e la risoluzione di criticità prima che diventino dei veri problemi.
Se hai bisogno di ulteriori chiarimenti non esitare a contattarci, siamo pronti a rispondere ad ogni tua domanda.
Useful links:
Customers
Twitter FEED
Recent activity
-
SecureOnlineDesktop
Estimated reading time: 6 minutes L'impatto crescente delle minacce informatiche, su sistemi operativi privati op… https://t.co/FimxTS4o9G
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The growing impact of cyber threats, on private or corporate operating systems… https://t.co/y6G6RYA9n1
-
SecureOnlineDesktop
Tempo di lettura stimato: 6 minuti Today we are talking about the CTI update of our services. Data security is… https://t.co/YAZkn7iFqa
-
SecureOnlineDesktop
Estimated reading time: 6 minutes Il tema della sicurezza delle informazioni è di grande attualità in questo peri… https://t.co/tfve5Kzr09
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The issue of information security is very topical in this historical period ch… https://t.co/TP8gvdRcrF
Newsletter
{subscription_form_1}© 2023 Secure Online Desktop s.r.l. All Rights Reserved. Registered Office: via dell'Annunciata 27 – 20121 Milan (MI), Operational Office: via statuto 3 - 42121 Reggio Emilia (RE) – PEC [email protected] Tax code and VAT number 07485920966 – R.E.A. MI-1962358 Privacy Policy - ISO Certifications












