
Estimated reading time: 6 minutes
An advanced persistent threat (APT) is a broad term used to describe an attack campaign in which an intruder, or a group of intruders, establishes an illicit and long-term presence on a network in order to extract highly sensitive data. The targets of these assaults, which are chosen and studied with great care, typically include large corporations or government networks. The consequences of such intrusions are vast, and include:
- Theft of intellectual property (for example, trade secrets or patents)
- Compromise of sensitive information (for example, private data of employees and users)
- Sabotage of critical organizational infrastructures (for example, deletion of databases)
- Total control takeover of the site
Executing an APT assault requires more resources than a standard attack on web applications. The perpetrators are usually teams of experienced cybercriminals who have substantial financial backing. Some APT attacks are government-funded and used as weapons of cyber warfare.
Common attacks, such as Remote File Inclusion (RFI), SQL injection, and cross-site scripting (XSS), are frequently used by the perpetrators to establish a foothold in a targeted network. Then, Trojans and backdoor shells are often employed to expand that foothold and create a persistent presence within the perimeter.

Progression of Advanced Persistent Threats
A successful APT attack can be divided into three phases: 1) network infiltration, 2) expansion of the attacker’s presence, and 3) extraction of the accumulated data, all without being detected.
- Network Infiltration
As mentioned, every advanced persistent threat begins with an infiltration. Companies are typically infiltrated through the compromise of one of the following areas: web resources, network resources, or authorized human users. This is achieved either through malicious uploads or social engineering attacks. All these are threats regularly faced by large organizations.
Infiltrators may also simultaneously carry out a DDoS attack against their target. This serves both as a smokescreen to distract the network staff and as a means to weaken a security perimeter, making it easier to breach.
Once initial access is gained, attackers quickly install a backdoor malware shell that secures access to the network and allows for stealthy remote operations. Backdoors may also manifest as Trojans disguised as legitimate software.
- Expansion of Presence
After the foothold is established, attackers move to expand their presence within the network and thereby “create” the true advanced persistent threat.
This involves moving up the hierarchy of an organization, compromising staff members with access to the most sensitive data. By doing so, attackers are able to gather critical business information, including product line information, employee data, and financial records.
Depending on the ultimate goal of the attack, the accumulated data might be sold to a competing enterprise, altered to sabotage a company’s product line, or used to take down an entire organization. If sabotage is the motive, this phase is used to subtly gain control of more critical functions and manipulate them in a specific sequence to cause maximum damage.
For instance, attackers might delete entire databases within a company and then disrupt network communications to prolong the recovery process.
- Data Extraction
While an APT event is ongoing, the stolen information is typically stored in a secure location within the compromised network. Once enough data has been collected, the thieves must extract it without being detected.
Typically, white noise tactics are used to distract the security team so that the information can be moved out. This might take the form of a DDoS attack, again tying up network personnel and/or weakening the site’s defenses to facilitate extraction.

Security Measures Against Advanced Persistent Threats
Proper detection and protection against APTs require a multifaceted approach from network administrators, security providers, and individual users.
Traffic Monitoring
Monitoring incoming and outgoing traffic is considered best practice to prevent the installation of backdoors and block the extraction of stolen data. Inspecting traffic within the corporate network perimeter can also help alert security personnel to any unusual behavior that may indicate malicious activity.
A web application firewall (WAF) deployed at the network edge filters traffic to web servers, thus protecting one of your most vulnerable attack surfaces. Among other functions, a WAF can help eliminate application-level attacks, such as RFI and SQL injection attacks, commonly used during the APT infiltration phase.
Traffic monitoring services for internal traffic, such as network firewalls, are the other side of this equation. They can provide a granular view that shows how users are interacting within your network, while helping to identify internal traffic anomalies (e.g., irregular logins or unusually large data transfers). The latter could indicate an ongoing APT attack. It is also possible to monitor access to file shares or system honeypots.
Lastly, incoming traffic monitoring services might be useful for detecting and removing backdoor shells. For comprehensive monitoring services, adopting the SOCaaS from SOD might be right for you.

Additional Measures Against Advanced Persistent Threats
In addition to the best practices already mentioned for preventing an advanced persistent threat on the corporate network, it is wise to take action on multiple fronts. In numerous other articles, we have discussed how beneficial it is for the security team to have a single place to monitor every point of the network. An excellent tool for this purpose is a SOC.
Our SOCaaS offers all the functionalities of a Security Operations Center without the burden of investing in equipment and specialized personnel. Moreover, thanks to UEBA technology, not only is our SOC able to retrieve and systematically store logs, but it is also actively involved in identifying suspicious user behavior.
These features are great for increasing the responsiveness of the security team and averting even attempts of advanced persistent threats against the corporate network.
To learn how we can help your company enhance its security, do not hesitate to contact us; we will be pleased to answer any questions.
Useful links:
Link utili:

Tempo di lettura stimato: 5 minutes
In un altro articolo abbiamo già parlato della Cyber Threat Intelligence spiegando cos’è, come funziona e le sue varie tipologie. Oggi, invece, ci focalizzeremo più sull’importanza della Cyber Threat Intelligence, approfondendo come può essere utile alle aziende per fornire risposte in ambito di sicurezza, contenendo i rischi e fornendo informazioni che supportino la risposta agli incidenti.
L’importanza della Cyber Threat Intelligence
In un mondo in cui le tecnologie e le minacce informatiche sono sempre in continua evoluzione, un’azienda non può permettersi di trascurare l’importanza della Cyber Threat Intelligence. Ogni giorno sul web avvengono innumerevoli attacchi informatici e furti di dati a danno di aziende e privati. Queste grandi quantità di informazioni, vengono poi catalogate e vendute illegalmente sul Dark Web.
Gli hacker sono soliti vendere informazioni in questa parte del web perché garantisce loro l’anonimato. Infatti, a differenza del web tradizionale, per poter accedere a questi luoghi virtuali, bisogna utilizzare un browser che mascheri il proprio indirizzo IP. Questo complica le attività di tracciamento dei criminali da parte delle autorità e rende il dark web un posto completamente anonimo.
Uno degli obbiettivi che si pone la CTI è quello di monitorare le informazioni presenti in questa grande parte del web a scopo analitico. Il fine è quello di prevenire e arginare i danni che questi dati potrebbero provocare.
Monitorare il Dark Web e il Deep Web
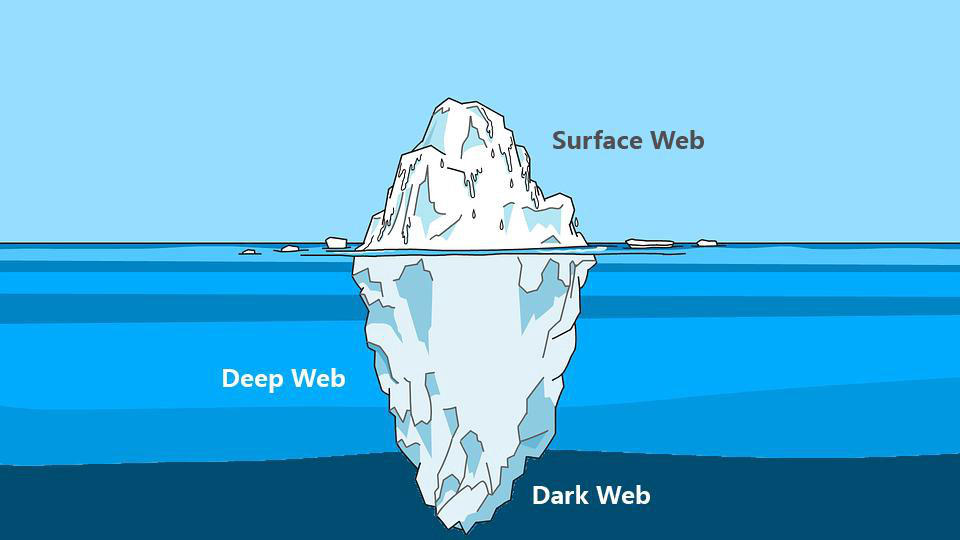
Spesso, quando parliamo di Deep Web e di Dark Web, pensiamo che siano presenti solo ed esclusivamente attività illegali, ma non è corretto. Ci sono anche forum, blog e siti web che hanno il fine di divulgare informazioni difficilmente reperibili sul web tradizionale.
Purtroppo però, è anche vero che i criminali sfruttano questa sezione della rete per vendere ogni genere di informazione. Queste comprendono numeri di telefono, indirizzi email, dati bancari, documenti, passaporti, credenziali d’accesso amministrative di siti web. C’è praticamente di tutto.
Questo genere di informazioni, nelle mani di un malintenzionato (o di un competitor), potrebbe compromettere l’integrità di un’intera azienda, dei suoi dipendenti e dei suoi clienti. Le conseguenze provocate da una violazione di dati, potrebbero inoltre manifestarsi anche sotto forma di danni alla reputazione dell’azienda.
Quando un cliente fornisce ad un’azienda i suoi dati personali si aspetta che vengano trattati con il massimo rispetto. I clienti potrebbero sentirsi “traditi” dall’azienda che avrebbe dovuto garantire loro la sicurezza delle proprie informazioni personali.
Un esempio clamoroso è stato il furto di dati avvenuto nel 2019 ai danni di Facebook Inc. (Fonte)
Ben 533 milioni di dati personali appartenenti agli utilizzatori della piattaforma sono stati sottratti, suddivisi per 106 paesi e diffusi gratuitamente sul web portando nuovamente la società al centro di polemiche.

Le aziende che cercano di proteggere i dati dei propri clienti, fornitori e dipendenti investono in strumenti di analisi e monitoraggio.
Affidandosi a dei professionisti, è possibile ricevere tempestivamente un avviso ogni qualvolta che un’informazione sensibile viene pubblicata su un forum o su un sito web presente nel Dark Web. Per questo l’importanza della Cyber Threat Intelligence gioca un ruolo chiave nel ramo della sicurezza informatica aziendale.
Monitorare il Dark Web dunque, significa avere la possibilità di poter rilevare tempestivamente eventuali informazioni sensibili prima che esse possano causare problemi alle aziende.

Strumenti per monitorare il Dark Web
Essendo una porzione di internet difficilmente accessibile e non indicizzata dai motori di ricerca, analizzare e monitorare le risorse presenti sul Deep Web diventa più complicato. Per questo motivo ci vengono in aiuto diversi strumenti progettati con lo scopo di semplificare il processo di indagine e analisi.
Un software che potrebbe essere d’aiuto durante un’attività d’investigazione è Onionscan, un programma Open Source completamente gratuito.
Il progetto Onionscan e la CTI
Il progetto Onionscan si pone due obiettivi:
– Aiutare gli operatori a trovare e risolvere problemi di sicurezza operativa
– Aiutare i ricercatori a monitorare e tracciare i siti presenti nel Deep Web
Il software è scaricabile sulla pagina Github dedicata, contenente anche una guida per l’installazione e una lista delle dipendenze necessarie per eseguire il software.
Una volta installato, per poterlo utilizzare basta semplicemente digitare nella riga di comando:
onionscan nomesitowebdascansionare.onion
Certamente, il solo accesso a uno strumento come questo non basta a fornire una copertura efficace. Infatti, l’importanza della Cyber Threat Intelligence risiede in gran parte nel saper effettuare le ricerche e interpretare i dati.
Conclusioni
Abbiamo visto cos’è e come funziona un’attività di monitoring del Dark Web e soprattutto abbiamo iniziato a comprendere l’importanza della Cyber Threat Intelligence.
Investire in queste soluzioni garantisce un’ulteriore sicurezza all’azienda. Mettere al sicuro i dati dei propri clienti e dei propri dipendenti non può essere un optional, ogni azienda dovrebbe essere sensibile a queste tematiche ed investire le proprie risorse per prevenire spiacevoli situazioni.
SOD offre un servizio apposito che si prefigge proprio di fornire informazioni di CTI preziose per la difesa proattiva e la risoluzione di criticità prima che diventino dei veri problemi.
Se hai bisogno di ulteriori chiarimenti non esitare a contattarci, siamo pronti a rispondere ad ogni tua domanda.
Useful links:

Estimated reading time: 5 minutes
Cyber Threat Hunting is a proactive security search across networks, endpoints and datasets to hunt down malicious, suspicious or risky activities that have escaped detection by existing tools.
Definition
There is a distinction between malware detection and cyber threat hunting . Threat detection is a passive approach to monitoring data and systems to identify potential security problems. However, it is a necessity and can help a threat hunter . Instead, proactive threat hunting tactics have evolved to use new threat intelligence on previously collected data to identify and classify potential risks before the attack .
Security personnel cannot afford to believe that their security system is impenetrable. Must always remain vigilant for the next threat or vulnerability . Rather than sitting around and waiting for threats to strike, cyber threat hunting develops hypotheses based on knowing the behaviors of threat actors and validating those hypotheses through active research in the environment .
With threat hunting, an expert doesn’t start with an alarm or indicators of compromise (IOC), but with deeper reasoning. In many cases the threat hunter’s efforts create and concretize the alarm or the IOC.
This aggressively assumes that a breach has occurred or will occur at the company. Security officers hunt down threats in their environment rather than rely on automatisms.

Threat hunting practice
For companies that are ready to take a more proactive approach to cybersecurity , which tries to stop attacks before they get too deep, adding threat hunting protocols to their security program is the next logical step.
After consolidating endpoint security and incident response strategies to mitigate the now unavoidable known malware attacks, companies can begin to take the offensive . This means digging deep and finding what hasn’t been detected yet. This is precisely the purpose of cyber threat hunting.
As mentioned earlier, threat hunting is an aggressive tactic that starts from the premise of the “assumption of violation”. Attackers are already inside an organization’s network and are secretly monitoring and moving into it.
This may sound far-fetched, but in reality, attackers can be inside a network for days, weeks, and even months . In the meantime, they prepare and execute attacks as advanced persistent threats, with no automatic defense detecting their presence . Cyber threat hunting stops these attacks by looking for covert indicators of compromise (IOCs) so they can be mitigated before the attacks reach their goals.

The key elements of a threat hunting
The goal of the threat hunt is to monitor daily activities and traffic across the network and investigate possible anomalies to find any undiscovered malicious activity that could lead to a complete breach . To achieve this level of proactive detection, threat hunting incorporates four equally important components.
1. Methodology
To be successful in hunt for threats, companies must commit to a proactive, full-time approach that is continuous and evolving. Instead, a responsive, ad hoc implementation, “ when we have time “, will be self-defeating and will only lead to minimal results.
2. Technology
Most companies already have comprehensive endpoint security solutions with automatic detection. Threat hunting works in addition to these and adds advanced technologies . The aim is to find anomalies, unusual patterns, and other traces of attackers that shouldn’t be in systems and files.
The new cloud-native endpoint protection (EPP) platforms that leverage big data analytics can capture and analyze large volumes of non-data filtered on endpoints, while behavioral analytics and artificial intelligence can provide broad, high-speed visibility into malicious behaviors that seem normal at first.
3. Highly qualified and dedicated staff
The threat hunters are a race of their own. These experts know how to use the security technology deployed by companies. In addition, also combine the aspiration to go on the offensive with intuitive problem-solving skills to uncover and mitigate hidden threats.
4. Threat intelligence
Having access to evidence-based global intelligence from experts from around the world (e.g. Miter Att & amp; ck ) further improves and accelerates hunting for existing threats. Hunters are aided by information such as attack classifications for identifying malware and threat groups , as well as advanced threat indicators.

The abilities of a threat hunter
The Threat Hunting Report from Crowd Research Partners confirms the importance of certain capabilities for threat hunting. When asked to rank the most important skill, the survey found that:
69% chose threat intelligence
57% chose behavior analysis
56% chose automatic detection
54% chose machine learning and automated analysis

The profile of a threat hunter
Threat hunters look for attackers who manage to break through vulnerabilities that a company might not even know exist . These attackers spend a considerable amount of time planning and performing the reconnaissance, acting only when they know they can successfully penetrate the network without warning. They also inject and build malware that has not yet been recognized or use techniques that do not rely on malware at all, to provide a persistent base from which to attack.
What does it take to outsmart even the smartest attackers?
A cyber threat hunter is relentless and can find even the smallest trace of what attackers have left behind. In general, threat hunters use their skills to undo the small changes that occur when attackers make their moves within a system or file.
The best threat hunters rely on their instincts to sniff out the stealth moves of the most dangerous attacker.
Are you a threat hunter? Contact us!
SOD is looking for a SOC / ICT analyst to add to the team. If you think you’re the right person, visit this page to view the detailed job posting.
Useful links:
Cyber Threat Intelligence (CTI) – greater effectiveness for IT security
Long-term search: what’s new in the SOCaaS service
SIEM has existed for quite some time, but it is not yet well understood. Also, the fact that technology has evolved significantly in recent years doesn’t help shed some light. Today we see where we are, trying to understand the Next Generation SIEM and the managed systems offered as services that make use of the latest generation SIEM (SOCaaS, for example). Let’s see what all this means for companies.
Being a fundamental part of the SOCaaS offered by SOD, it seems appropriate to explain in detail what a Next Generation SIEM is and what its functions are.
A brief history of SIEM
Before examining what a Next Generation SIEM is, it is right to briefly review the history of this technology and its beginning.
The term Security Information and Event Management (SIEM) was coined in 2005 by Mark Nicolett and Amrit T. Williams of Gartner. The word is the merger of Security Event Management (SEM) and Security Information Management (SIM).
Its original definition given by the creators of the term is: a technology that supports the detection of threats and the response to security incidents, through the collection in real time and historical analysis of events from a wide variety of sources of contextual data.
SIEM was born out of the need to address the huge number of alarms issued by intrusion prevention systems (IPS) and intrusion detection systems (IDS) that were overwhelming IT departments. By helping organizations aggregate events and better analyze those within the network, SIEM has helped organizations improve threat detection. It has also led organizations to take a more proactive approach to security. Preventive security technologies are no longer sufficient on their own.
The difficulties of SIEMs in the early years
Eager to improve their cybersecurity situation, many enterprise-wide organizations have rapidly adopted SIEM technology. Over the years, however, inherited problems have emerged from the past:
1. The datasets were inflexible, so some SIEMs were unable to process the required data, which meant their effectiveness was limited
2. They were difficult to maintain and manage, which added complexity and drained staff resources
3. SIEMs produced a high number of false positives, creating even more work for the security teams
4. With the advancement of technology, SIEMs have struggled to keep up with the evolution of threats and therefore the IT risk for companies has grown
The Next Generation SIEM arrives
Many advanced threats are now polymorphic rather than static. That is, they are able to constantly modify their behavior to evade detection. As such, Next Generation SIEM systems must not only process more data, but also become much more capable of recognizing new patterns within them.
Given the difficulties and limitations of inherited SIEM systems, many thought they would disappear over time. But this did not happen, SIEM still remains a key technology used by companies. However, technology has had to evolve.
While SIEM once relied on only a handful of data sources, the “Next Generation” of SIEM systems was developed to process a greater volume and variety of data, as well as correlating it in a timely fashion.
Gartner reported that the SIEM market is continuously growing. One reason for this growth is that Next Gen SIEM systems are now used by midsize organizations, not just large enterprises.
What are the capabilities of Next Gen SIEM?
Next Gen SIEMs, sometimes referred to as analytical SIEMs or SIEM 3.0, have brought new capabilities to organizations and their security teams.
– Allow faster integration into a corporate infrastructure through an open architecture to cover cloud, on-premise and BYOD resources
– Include real-time visualization tools to understand the most important and high-risk activities
– Use scenario and behavior analysis to “photograph” well understood scenarios and highlight significant changes in behavior
– Integrate and use Threat Intelligence information from customized, open source and commercial sources
– Provide a flexible framework that allows for the implementation of a tailored workflow for key organizational use cases
– Measure status against regulatory frameworks (e.g. PCI DSS) for prioritization and risk management
Security Orchestration, Automation and Response
Security Orchestration, Automation and Response (SOAR) is a growing security area that Next Gen SIEM vendors are exploiting to contribute and take advantage of the latest features. In its essence, SOAR has two fundamental aspects:
1. It allows to bring more data to a Next Gen SIEM for analysis
SOAR is helping SIEM technology to become smarter and big data oriented, thus enabling security teams to make faster and better informed decisions. Broader intelligence means more reliable threat identification and fewer false positives.
2. Help automate incident response
Another important way SOAR is influencing the evolution of SIEM Next Gen is to help standardize incident analysis and response procedures. The goal is to partially or completely automate response activities in order to reduce the potential harm and inconvenience that breaches can cause. Such response activities could include blocking compromised user accounts and blocking IP addresses on a firewall.
By automating routine actions, SOAR helps security teams become more efficient and frees them up time to focus on threat hunting and patch management.
User Behavior Analysis (UEBA)
Another important feature of Next Generation SIEMs is the use of User and Entity Behavior Analytics (UEBA). UEBA does not track security events or monitor devices, but instead focuses on monitoring and analyzing the behavior of an organization’s users.
UEBA can be extremely useful in helping organizations identify compromised accounts, as well as insider threats. It works using advanced machine learning and behavioral profiling techniques to identify anomalous activity such as account compromise and abuse of privileges. By not using rules-based monitoring, the UEBA is more effective in detecting anomalies over time.
The challenges for a modern SIEM
Despite unquestionable advances in detecting complex cyber threats, SIEM Next Gens can still, if not used and maintained properly, generate a large number of alerts. For organizations without IT resources and dedicated security personnel, researching these alerts to distinguish true network security problems from false positives can be extremely complex and time-consuming.
Even when real threats are identified, knowing how to respond to them can be just as challenging.
Getting the most out of SIEM to help address growing security challenges will also depend on better trained personnel who can use the systems more effectively and validate alarms. For organizations that lack in-house knowledge or skills, it therefore makes sense to work with an external vendor who can cover or augment security capabilities.
A full SOCaaS service, including Next Generation SIEM and UEBA for threat hunting, is the ideal choice. Not only does it save time in terms of validating and checking alarms, but also in economic terms, not having to face installation costs and staff training.
If you are interested in learning more, do not hesitate to contact us, we will answer your questions.
[btnsx id=”2931″]
Useful links:
Security: Pentest and verification of vulnerabilities
What is a Network Lateral Movement and how to defend yourself
Is SOCaaS useful for your business?
Computer network security: PT vs. VA
SIEM in computer science: history
SIEM software: what it is and how it works

A SIEM solution in IT is one of the essential components of a SOC (Security Operation Center). Its task is to collect information and analyze it in search of anomalies and possible breaches in the system. But the defense process hasn’t always been that simple. What we now call SIEM, Security Information and Event Management, is the union of two different types of cyber security tools.
SIM and SEM: the origins
Before the arrival of a complete SIEM solution in computing, security was heavily focused on perimeter security and did not keep the internal network adequately controlled. The first solutions developed in the 90s were basic and basically dealt with security information management (SIM) or security event management (SEM). They were solutions available as tools that had to be deployed on-site in the data center to be protected. This limited scalability, because adding capacity required the purchase of additional equipment.
These early solutions were also built on proprietary databases that forced customers to use technology from a single vendor. If you wanted to move your data to another system, the process was long and complicated. It should also be noted that archiving was more expensive, so only the most valuable data was collected. Furthermore, although the SIM and SEM solutions contained all the data necessary for the defense, the search and alarm were rudimentary. Additionally, they depended on experienced security analysts to research, understand and interpret what they found in the data.
SIEM origins in computer science
As data became more sensitive and technology more powerful, SIEM systems (SIM + SEM) became capable of ingesting, processing and storing a great deal of data. Next-generation SIEM IT solutions are able to use signature-based alerts to identify threats in collected data. However, only those alerts that have identified indicators of compromise (IOC) of a certain threat can be identified in this way.
To be clear, if the type of attack to which a system is subjected has not been cataloged in a series of IOCs, a first generation SIEM is not able to detect it. The main drawback of those systems was the very limited ability to detect unknown cyber threats.
To give a practical example: it was possible to use a rule like this: “give a warning if a user enters 10 consecutive wrong passwords“. In theory this could be used to detect brute force password attacks. But what if the attacker only tried 9 passwords in a row? Or what if the alarm was given for a very forgetful user?
Next Gen SIEM (NGS)
A next generation SIEM is built on a large data platform that provides unlimited scalability and is hosted in the cloud. A next gen SIEM includes log management, advanced threat detection based on behavior analysis and automatic incident response, all on a single platform.
This eliminates the problems that old on-premises systems were prone to. Not having to install anything and being able to send the necessary data to the cloud quite simply, the computing power of the local machine is not compromised and the SIEM can manage all the data safely.
How a SIEM proceeds in cyber threat analysis
1. Data Collection: An IT SIEM solution collects data from across the organization using agents installed on various devices, including endpoints, servers, network equipment and other security solutions. Next generation SIEM includes support for cloud applications and infrastructure, business applications, identity data and non-technical data feeds.
2. Data enrichment: Enrichment adds further context to events. SIEM will enrich data with identity, resources, geolocation and threat information.
3. Data storage: The data will then be stored in a database so that it can be searched for during investigations. The next generation SIEM exploits open source architectures and big data architectures, exploiting their scalability.
4. Correlation and Analysis: SIEM solutions use several techniques to draw actionable conclusions from SIEM data. These techniques vary greatly.
5. Report: A SIEM, particularly a next generation SIEM, gives you the ability to quickly search for data, allowing you to dig through alerts and search for threat actors and indicators of compromise. The displayed data can be saved or exported. It is also possible to use out-of-the-box reports or create ad hoc reports as needed.
What a SIEM is used for
Threat hunting and investigation
The ability to perform threat hunting on a SIEM is critical to understanding the true patterns of attacks based on access, activity and data breaches. By developing a detailed and contextual view of attacks, security analysts can more easily develop policies, countermeasures and incident response processes to help mitigate and remove the threat.
Response in case of an accident
An effective response to incidents is essential to intervene more quickly and reduce the residence time of the threat. For this, a SIEM provides an incident response playbook with configurable automated actions. A SIEM is able to integrate with third party solutions for security orchestration (SOAR) or individual case management.
Defense against insider threats
The reason why insider threats are such a big problem is because it’s not about entering the perimeter, but about exploiting insider positions. They can be your employees, contractors or business associates. It may be they themselves wanting to exploit their location, or their account may have been hacked.
With all kinds of internal threats, the attacker tries to stay hidden, gathering sensitive data to exploit. This could cause significant damage to the company, its position in the industry and its relationship with consumers or investors. By using a SIEM, you avoid this risk.
Cyber threat detection
Your organization is likely to have at least one sensitive data repository. Cybercriminals thrive on looting this data for financial gain. Many breaches begin with a simple phishing email against an organization’s target. Simply clicking on an attachment can leave malicious code behind. A SIEM will allow you to monitor advanced cyberthreat patterns such as phishing, beaconing and lateral movement.
Compliance standards
For many industries, adherence to compliance standards is critical. A SIEM can help by providing reports focused on data compliance requests. Integrated packages covering all major mandates, including PCI DSS, SOX, and ISO 27001, are a standard feature of SIEMs as well.
Next Generation SIEM
A next generation SIEM is not just a cloud hosted system. It also makes use of the implementation of AI and Machine Learning to increase the defense of the IT system.
We will see it in a future article, but it is right to specify that the SOCaaS offered by SOD makes use of the latest generation technology offered by Next Gen. SIEM systems. Contact us to find out more about it and talk to experts who can dispel all your doubts.
[btnsx id=”2931″]
Useful links:
Security: Pentest and verification of vulnerabilities
What is a Network Lateral Movement and how to defend yourself
Is SOCaaS useful for your business?
Computer network security: PT vs. VA

Customers
Twitter FEED
Recent activity
-
SecureOnlineDesktop
Estimated reading time: 6 minutes L'impatto crescente delle minacce informatiche, su sistemi operativi privati op… https://t.co/FimxTS4o9G
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The growing impact of cyber threats, on private or corporate operating systems… https://t.co/y6G6RYA9n1
-
SecureOnlineDesktop
Tempo di lettura stimato: 6 minuti Today we are talking about the CTI update of our services. Data security is… https://t.co/YAZkn7iFqa
-
SecureOnlineDesktop
Estimated reading time: 6 minutes Il tema della sicurezza delle informazioni è di grande attualità in questo peri… https://t.co/tfve5Kzr09
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The issue of information security is very topical in this historical period ch… https://t.co/TP8gvdRcrF
Newsletter
{subscription_form_1}© 2023 Secure Online Desktop s.r.l. All Rights Reserved. Registered Office: via dell'Annunciata 27 – 20121 Milan (MI), Operational Office: via statuto 3 - 42121 Reggio Emilia (RE) – PEC [email protected] Tax code and VAT number 07485920966 – R.E.A. MI-1962358 Privacy Policy - ISO Certifications















