Veeam Cloud Connect
 Giacomo Lanzi
Giacomo Lanzi
Avoid Ransomware: That’s why it’s best not to take any risks
ransomware gangs have been targeting businesses in recent times, demanding larger payments than they can extort from consumers. The plan was very successful. According to the new data, 70% of the attacked companies paid the ransom to get their data back. Avoiding ransomware is a necessity, these figures implicitly prove it. If such a large number of companies pay, it…
 Piergiorgio Venuti
Piergiorgio Venuti
7 motivi per NON rinnovare un backup tradizionale
Veeam Availability Ogni giorno sempre più clienti dei backup tradizionali passano a Veeam®. Perché? Perché le tecnologie progettate per l’era client-server non possono offrire l’Availability 24.7.365 di cui necessitano le aziende moderne, né la capacità di ripristinare in pochi minuti o secondi qualsiasi servizio IT in esecuzione nel cloud ibrido. [bg_collapse view=”button-blue” color=”#ffffff” icon=”eye” expand_text=”Maggiori informazioni” collapse_text=”Mostra meno” ] La sostituzione…
 Piergiorgio Venuti
Piergiorgio Venuti
Remote access for MSPs in Veeam Backup & Replication 9.5 Update 2
Veeam Backup Remote Access. We are happy to announce that the RTM build of Veeam Backup & Replication 9.5 Update 2 is now read up and running on Veeam Cloud Connect service! This is the latest update for our flagship product and adds support for the upcoming release of Veeam Agent for Microsoft Windows 2.0 along with other significant enhancements…
 Piergiorgio Venuti
Piergiorgio Venuti
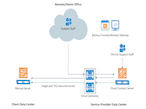
BaaS with Veeam Cloud Connect
Veeam 2017 Availability Report 3 Steps To Avoid $21.8M In Downtime Costs [btnsx id=”4150″] Examining the real world impacts when service Availability goals are not met. Veeam® commissioned ESG to survey over 1,000 global IT decision makers to better understand the protection, recovery, and Availability challenges they are facing today. Overall results were surprising – demonstrating a startling amount of…
Customers
Twitter FEED
Recent activity
-
SecureOnlineDesktop
Estimated reading time: 6 minutes L'impatto crescente delle minacce informatiche, su sistemi operativi privati op… https://t.co/FimxTS4o9G
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The growing impact of cyber threats, on private or corporate operating systems… https://t.co/y6G6RYA9n1
-
SecureOnlineDesktop
Tempo di lettura stimato: 6 minuti Today we are talking about the CTI update of our services. Data security is… https://t.co/YAZkn7iFqa
-
SecureOnlineDesktop
Estimated reading time: 6 minutes Il tema della sicurezza delle informazioni è di grande attualità in questo peri… https://t.co/tfve5Kzr09
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The issue of information security is very topical in this historical period ch… https://t.co/TP8gvdRcrF
Newsletter
{subscription_form_1}© 2023 Secure Online Desktop s.r.l. All Rights Reserved. Registered Office: via dell'Annunciata 27 – 20121 Milan (MI), Operational Office: via statuto 3 - 42121 Reggio Emilia (RE) – PEC [email protected] Tax code and VAT number 07485920966 – R.E.A. MI-1962358 Privacy Policy - ISO Certifications












