Piergiorgio Venuti
Piergiorgio Venuti
Let’s Encrypt Free Certificates for all Webhosting users
Let’s Encrypt is a free, automated and open Certification Authority. The objective of Let’s Encrypt and the ACME protocol is to make it possible to set up an HTTPS server and have it automatically obtain a browser-trusted certificate, without any human intervention. This is accomplished by running a certificate management agent on the web server.
With our Webhosting service based on Plesk technology you can have free SSL certificates with Let’s Encrypt so all your web pages will be secured.
Plesk plugin is installed by default on all subscriptions, you just need to enable it if you like to use SSL certificate to protect your web site.
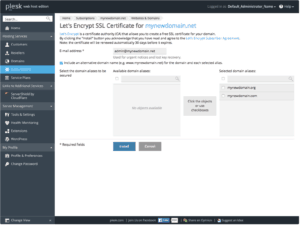
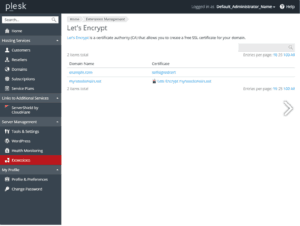
Creating SSL Certificates with Let’s Encrypt
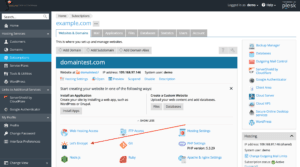
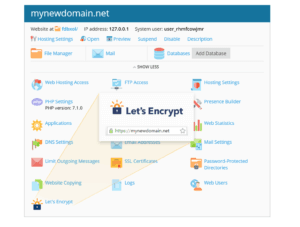
To create your SSL Certificate just logon in your Webhosting portal, click on domain you like to create SSL certificates then click on related icon like show below:
If you still don’t have a Webhosting service you can access to Webhosting demo.
Screenshots
HTTPS and SEO
Once again Google dictates the rules to comply with so as not to see its site “penalized” compared to others. We are not talking about the classic penalties already explained in this section .. but we can talk about “positioning factor” as evidenced by one of the first statements provided by Google in 2014: “Https as a positioning factor”.
Starting from January 2017, to help users browse the web safely, Google Chrome will indicate as “NOT SECURE” all those pages that collect passwords or credit cards.
Unlike other positioning factors, implementing an SSL certificate involves difficulties, risks and costs.
[btnsx id=”2931″]
Useful links:
CloudFlare free Plesk extension for Webhosting users
Customers
Twitter FEED
Recent activity
-
SecureOnlineDesktop
Estimated reading time: 6 minutes L'impatto crescente delle minacce informatiche, su sistemi operativi privati op… https://t.co/FimxTS4o9G
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The growing impact of cyber threats, on private or corporate operating systems… https://t.co/y6G6RYA9n1
-
SecureOnlineDesktop
Tempo di lettura stimato: 6 minuti Today we are talking about the CTI update of our services. Data security is… https://t.co/YAZkn7iFqa
-
SecureOnlineDesktop
Estimated reading time: 6 minutes Il tema della sicurezza delle informazioni è di grande attualità in questo peri… https://t.co/tfve5Kzr09
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The issue of information security is very topical in this historical period ch… https://t.co/TP8gvdRcrF
Newsletter
{subscription_form_1}© 2023 Secure Online Desktop s.r.l. All Rights Reserved. Registered Office: via dell'Annunciata 27 – 20121 Milan (MI), Operational Office: via statuto 3 - 42121 Reggio Emilia (RE) – PEC [email protected] Tax code and VAT number 07485920966 – R.E.A. MI-1962358 Privacy Policy - ISO Certifications